Microsoft fixes Windows Smart App Control zero-day exploited since 2018
by nlqip

Microsoft has fixed a Windows Smart App Control and SmartScreen flaw that has been exploited in attacks as a zero-day since at least 2018.
On vulnerable systems, threat actors have abused the vulnerability (now tracked as CVE-2024-38217) to circumvent Smart App Control and the Mark of the Web (MotW) security feature to launch untrusted or potentially dangerous binaries and apps without warnings.
“To exploit this vulnerability, an attacker could host a file on an attacker-controlled server, then convince a targeted user to download and open the file. This could allow the attacker to interfere with the Mark of the Web functionality,” Microsoft explained in a security advisory published today.
“An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as SmartScreen Application Reputation security check and/or the legacy Windows Attachment Services security prompt.”
Smart App Control in Windows 11 uses Microsoft’s app intelligence services and code integrity features to detect and block potentially harmful apps or binaries.
It replaces SmartScreen in Windows 11, but SmartScreen will still automatically take over if Smart App Control is not enabled to protect against malicious content. Both security features are activated when users try to open files marked with a “Mark of the Web” label.
Last month, Elastic Security Labs disclosed CVE-2024-38217 as a flaw in handling LNK files, known as LNK stomping. This flaw allows attackers to bypass Smart App Control security features that otherwise block untrusted applications from launching.
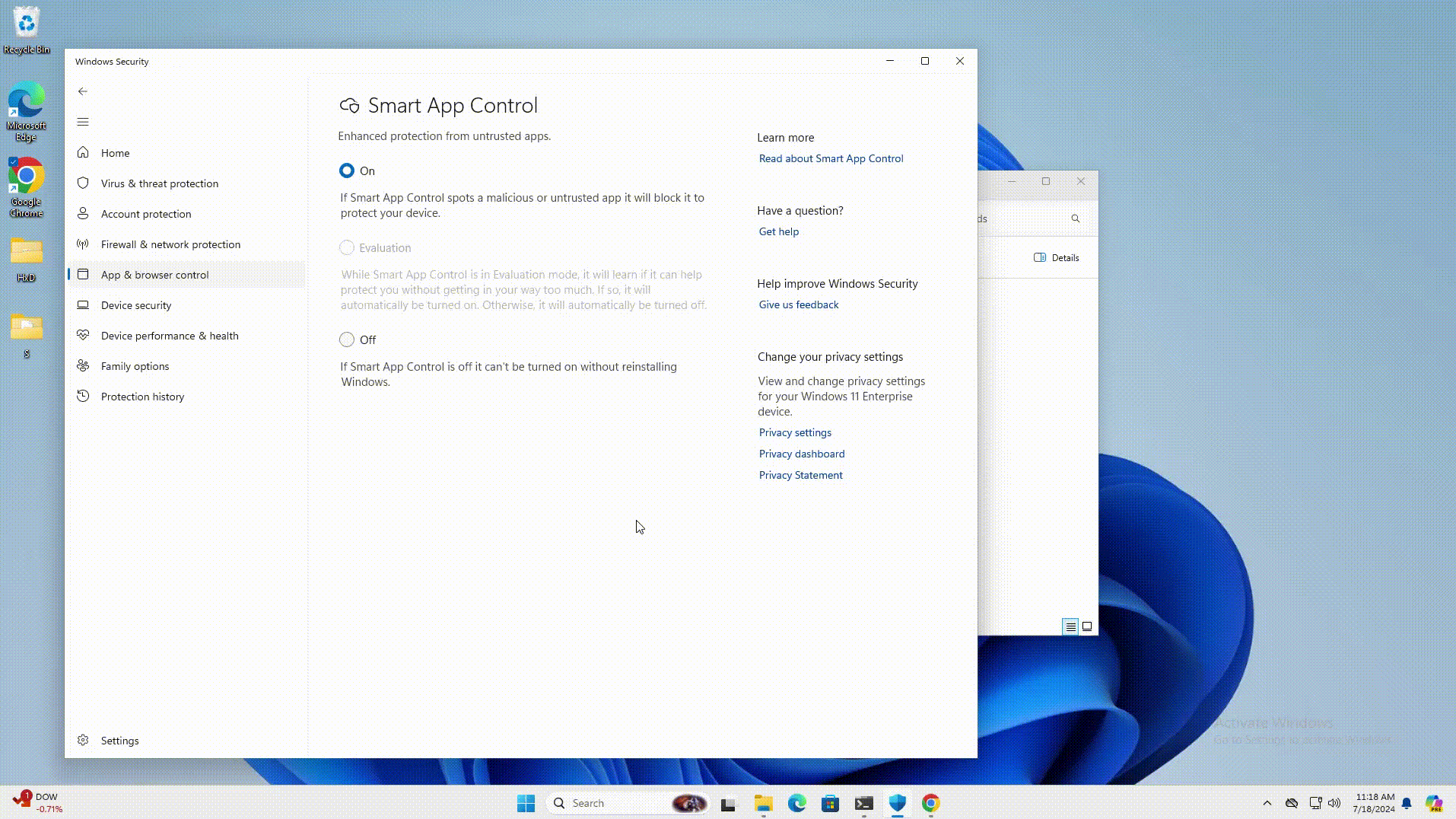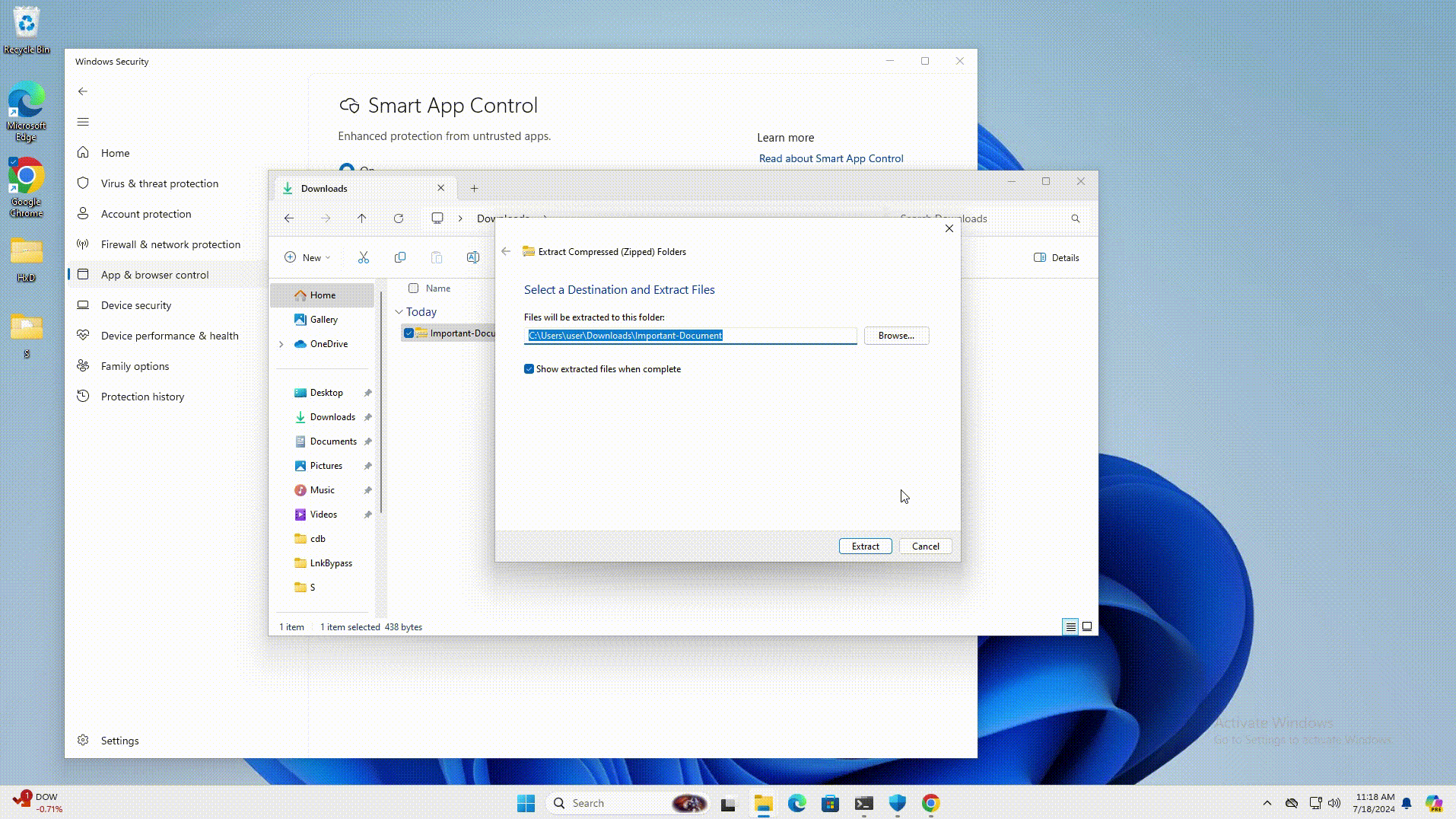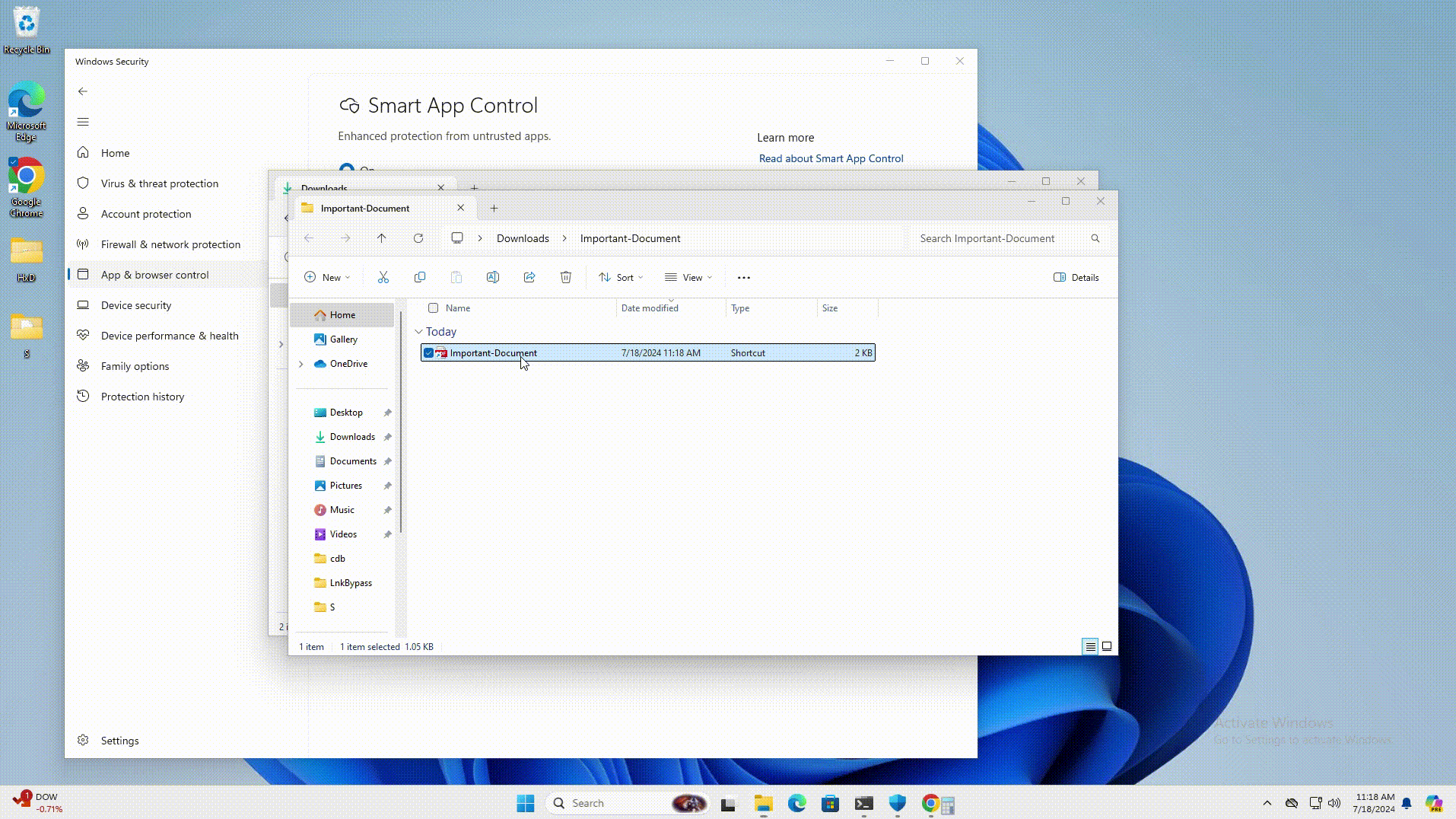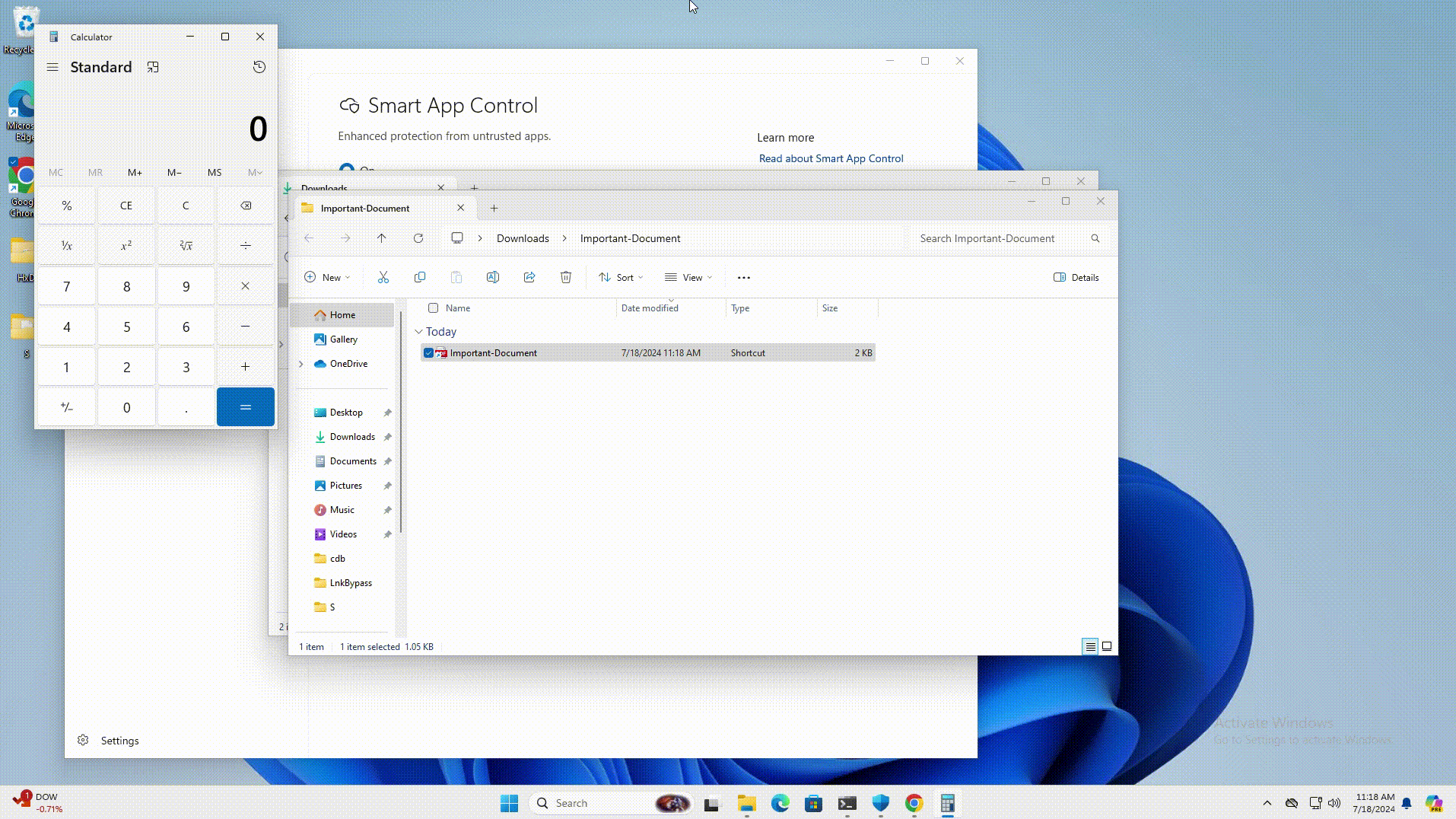
LNK stomping involves creating LNK files with unconventional target paths or internal structures. When a user clicks on one of these files, Windows Explorer (explorer.exe) automatically adjusts the LNK file to use its canonical formatting. However, this process also removes the “Mark of the Web” (MotW) label from downloaded files, a marker that Windows security features use to trigger an automated security check.
To exploit this flaw, attackers can add a dot or space to the target executable path (for instance, adding it to the binary name like “powershell.exe.”) or create an LNK file with a relative path like “.target.exe.” When the target clicks the link, Windows Explorer identifies the correct executable, updates the path, removes the MotW label, and launches the file, bypassing security checks.
Elastic Security Labs said in August that there is reason to believe that the vulnerability has been exploited for years, as multiple samples have been found on VirusTotal, the oldest dating back over six years.
The company shared its findings with the Microsoft Security Response Center, which acknowledged the issue and said it “may be fixed in a future Windows update.”
Elastic Security Labs researcher Joe Desimone has also developed and shared an open-source tool for evaluating a file’s Smart App Control trust level.
Source link
lol
Microsoft has fixed a Windows Smart App Control and SmartScreen flaw that has been exploited in attacks as a zero-day since at least 2018. On vulnerable systems, threat actors have abused the vulnerability (now tracked as CVE-2024-38217) to circumvent Smart App Control and the Mark of the Web (MotW) security feature to launch untrusted or potentially…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
