New PIXHELL acoustic attack leaks secrets from LCD screen noise
by nlqip
A novel acoustic attack named ‘PIXHELL’ can leak secrets from air-gapped and audio-gapped systems, and without requiring speakers, through the LCD monitors they connect to.
In a PIXHELL attack, malware modulates the pixel patterns on LCD screens to induce noise in the frequency range of 0-22 kHz, carrying encoded signals within those acoustic waves that can be captured by nearby devices such as smartphones.

Source: Arxiv.org
The researchers’ tests showed that data exfiltration is possible at a maximum distance of 2 meters (6.5 ft), achieving a data rate of 20 bits per second (bps).
While this is too slow to make large file transfers practical, real-time keylogging and stealing small text files that might contain passwords or other information are still possible.
Covert audio channel
PIXHELL was developed by Dr. Mordechai Guri of the Ben-Gurion University of the Negev, known for his extensive research in methods to leak data from air-gapped environments.
Just last week, the researcher published another paper on a novel side-channel attack dubbed “RAMBO” (Radiation of Air-gapped Memory Bus for Offense) that can steal data from an air-gapped environment by generating electronic radiation from a device’s RAM components.
The PIXHELL attack method takes advantage of the unintended acoustic emissions from LCD screens resulting from coil whine, capacitor noise, or intrinsic vibrations that cannot be physically eliminated from the devices.
Using specially crafted malware, an attacker can encode sensitive data like encryption keys or keystrokes into acoustic signals using modulation schemes such as:
- On-Off Keying (OOK): Data is encoded by switching the sound on and off.
- Frequency Shift Keying (FSK): Data is encoded by switching between different frequencies.
- Amplitude Shift Keying (ASK): Data is encoded by changing the amplitude (volume) of the sound.

Source: Arxiv.org
Next, the modulated data is transmitted via the LCD screen by changing the pixel patterns on it, which alters the sound emitted from the device’s components.
A nearby microphone on a rogue or compromised device such as a laptop or smartphone can pick up the acoustic signals and may later transmit them to the attacker for demodulation.
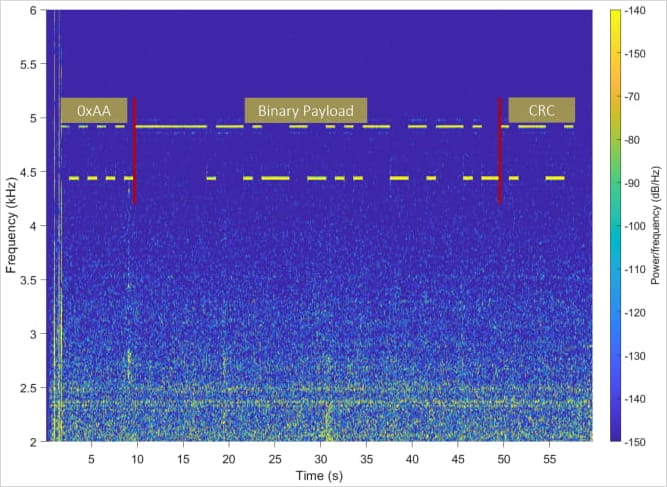
Source: Arxiv.org
Notably, PIXHELL can be executed in a setting involving multiple signal sources and a single recipient, so it’s possible to capture secrets from several air-gapped systems simultaneously, if those were infected by malware.
The sound frequencies produced by the PIXHELL malware are typically in the 0 – 22 kHz frequency range which is hardly audible to humans. For comparison, humans typically detect sounds in a frequency range between 20Hz to 20kHz and an average adult’s upper limit is typically around 15-17kHz.
At the same time, the pixel patterns used in the attack are low-brightness or invisible to the user, which makes the attack particularly stealthy.
Potential countermeasures
Several defenses can be implemented against PIXHELL and other types of acoustic side-channel attacks. In highly critical environments, microphone-carrying devices should be banned entirely from certain areas out of an abundance of caution.
Jamming or noise generation, where background noise is introduced to disrupt the acoustic signals and increase the signal-to-noise ratio (SNR) to make the attack impractical, is also a solution.
Dr. Guri also suggests monitoring the screen buffer with a camera to detect unusual pixel patterns that do not match the system’s normal operations.
Complete technical details about PIXHELL attack and potential defense strategies are available in the technical paper titled PIXHELL Attack: Leaking Sensitive Information
from Air-Gap Computers via ‘Singing Pixels’.
Source link
lol
A novel acoustic attack named ‘PIXHELL’ can leak secrets from air-gapped and audio-gapped systems, and without requiring speakers, through the LCD monitors they connect to. In a PIXHELL attack, malware modulates the pixel patterns on LCD screens to induce noise in the frequency range of 0-22 kHz, carrying encoded signals within those acoustic waves that can…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
