RansomHub ransomware abuses Kaspersky TDSSKiller to disable EDR software
by nlqip

The RansomHub ransomware gang has been using TDSSKiller, a legitimate tool from Kaspersky, to disable endpoint detection and response (EDR) services on target systems.
After taking down the defenses, RansomHub deployed the LaZagne credential-harvesting tool to extract logins from various application databases that could help move laterally on the network.
TDSSKiller abused in ransomware attacks
Kaspersky created TDSSKiller as a tool that can scan the system for the presence of rootkits and bootkits, two types of malware that are particularly difficult to detect and can evade standard security tools.
EDR agents are more advanced solutions that operate, at least partially, at the kernel level, as they need to monitor and control low-level system activities such as file access, process creation, and network connections, all providing real-time protection against threats like ransomware.
Cybersecurity company Malwarebytes reports that they recently observed RansomHub abusing TDSSKiller to interact with kernel-level services using a command line script or batch file that disabled the Malwarebytes Anti-Malware Service (MBAMService) running on the machine.
Source: Malwarebytes
The legitimate tool was employed following the reconnaissance and privilege escalation phase, and executed from a temporary directory (‘C:Users<User>AppDataLocalTemp’) using a dynamically generated filename (‘{89BCFDFB-BBAF-4631-9E8C-P98AB539AC}.exe’).
Being a legitimate tool signed with a valid certificate, TDSSKiller does not risk RansomHub’s attack getting flagged or stopped by security solutions.
Next, RansomHub used the LaZagne tool in an attempt to extract credentials stored in databases using LaZagne. In the attack that Malwarebytes investigated, the tool generated 60 file writes that were likely logs of the stolen credentials.
The action to delete a file could be the result of the attacker trying to cover their activity on the system.
Defending against TDSSKiller
Detecting LaZagne is straightforward as most security tools flag it as malicious. However, its activity can become invisible if TDSSKiller is used to deactivate the defenses.
TDSSKiller is in a gray area, as some security tools, including Malwarebytes’ ThreatDown, label it as ‘RiskWare’, which could also be a red flag to users.
The security firm suggests activating the tamper protection feature on the EDR solution, to make sure that attackers can’t disable them with tools like TDSSKiller.
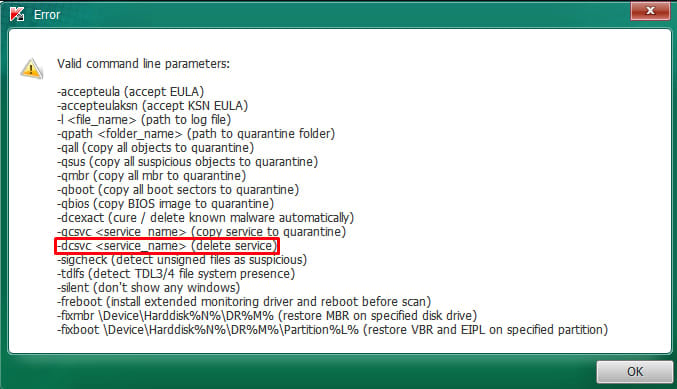
Additionally, monitoring for the ‘-dcsvc’ flag, the parameter that disables or deletes services, and for the execution of TDSSKiller itself can help detect and block the malicious activity.
Source link
lol
The RansomHub ransomware gang has been using TDSSKiller, a legitimate tool from Kaspersky, to disable endpoint detection and response (EDR) services on target systems. After taking down the defenses, RansomHub deployed the LaZagne credential-harvesting tool to extract logins from various application databases that could help move laterally on the network. TDSSKiller abused in ransomware attacks Kaspersky…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
