New Vo1d malware infects 1.3 million Android TV streaming boxes
by nlqip
Threat actors have infected over 1.3 million Android TV streaming boxes with a new Vo1d backdoor malware, allowing the attackers to take full control of the devices.
Android TV is Google’s operating system for smart TVs and streaming devices, offering an optimized user interface for TVs and remote navigation, integrated Google Assistant, built-in Chromecast, live TV support, and the ability to install apps.
The operating system powers the smart TV features for numerous manufacturers, including TCL, Hisense, and Vizio TVs. It also acts as the operating system for standalone TV streaming media devices, such as the NVIDIA Shield.
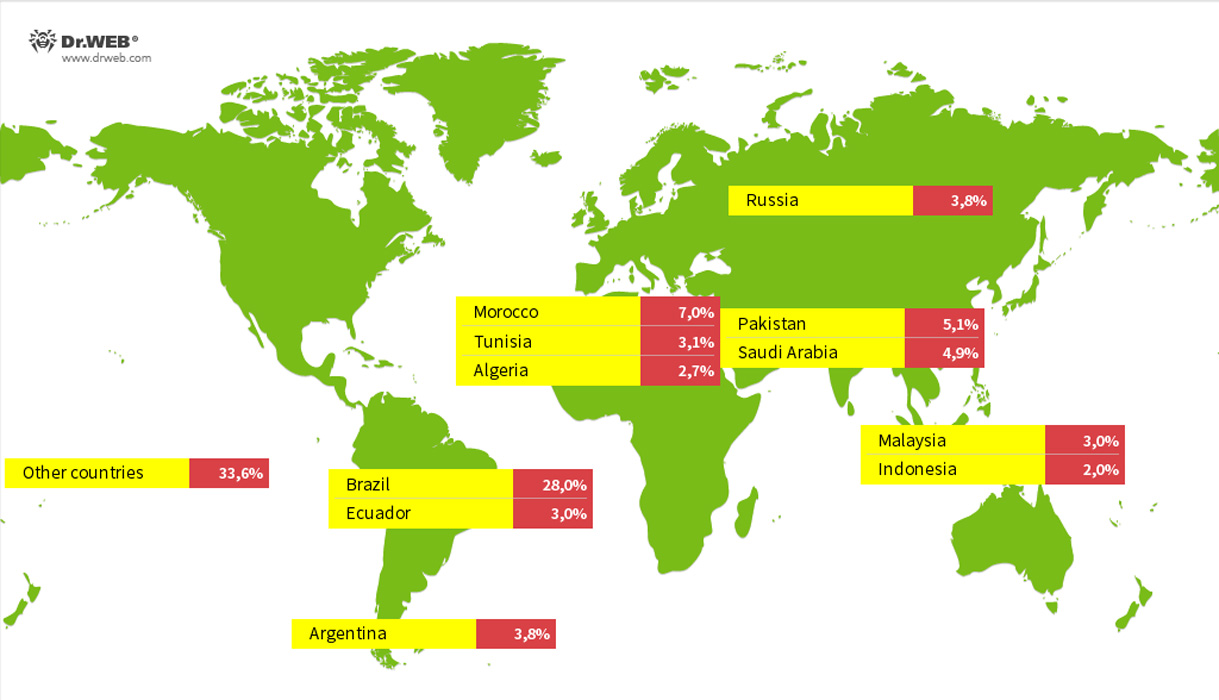
In a new report by Dr.Web, researchers found 1.3 million devices infected with the Vo1d malware in over 200 countries, with the largest number detected in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia.
Source: Dr.Web
The Android TV firmware seen being targeted in this malware campaign include:
- Android 7.1.2; R4 Build/NHG47K
- Android 12.1; TV BOX Build/NHG47K
- Android 10.1; KJ-SMART4KVIP Build/NHG47K
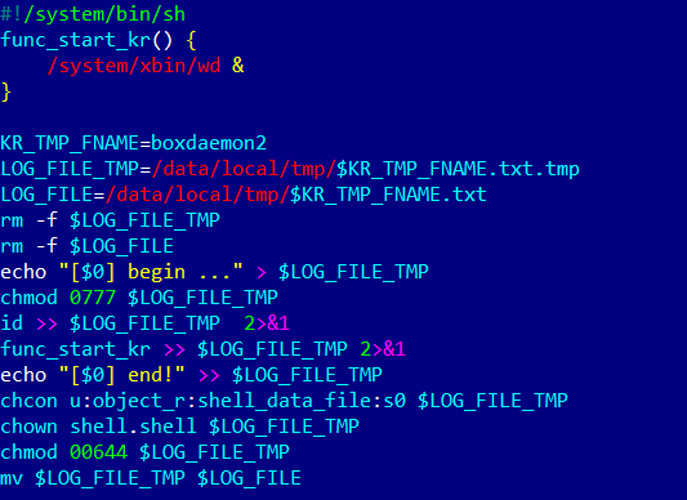
Depending on the version of the Vo1d malware installed, the campaign will modify the install-recovery.sh, daemonsu, or replace the debuggerd operating system files, all of which are startup scripts commonly found in Android TV.
Source: Dr.Web
The malware campaign uses these scripts for persistence and to launch the Vo1d malware on boot.
The Vo1d malware itself is located in the files wd and vo1d, which the malware is named after.
“Android. Vo1d’s main functionality is concealed in its vo1d (Android.Vo1d.1) and wd (Android.Vo1d.3) components, which operate in tandem,” explains Dr.Web.
“The Android.Vo1d.1 module is responsible for Android. Vo1d.3’s launch and controls its activity, restarting its process if necessary. In addition, it can download and run executables when commanded to do so by the C&C server.”
“In turn, the Android.Vo1d.3 module installs and launches the Android.Vo1d.5 daemon that is encrypted and stored in its body. This module can also download and run executables. Moreover, it monitors specified directories and installs the APK files that it finds in them.”
While Dr.Web does not know how Android TV streaming devices are being compromised, researchers believe they are targeted because they commonly run outdated software with vulnerabilities.
“One possible infection vector could be an attack by an intermediate malware that exploits operating system vulnerabilities to gain root privileges,” concludes Dr.Web.
“Another possible vector could be the use of unofficial firmware versions with built-in root access.”
To prevent infection by this malware, it is advised that Android TV users check for and install new firmware updates as they become available. Also be sure to remove these boxes from the internet in case they are being remotely exploited through exposed services.
Last but not least, avoid installing Android applications as APKs from third-party sites on Android TV as they are a common source of malware.
A list of IOCs for the Vo1d malware campaign can be found on Dr. Web’s GitHub page.
Source link
lol
Image: Midjourney Threat actors have infected over 1.3 million Android TV streaming boxes with a new Vo1d backdoor malware, allowing the attackers to take full control of the devices. Android TV is Google’s operating system for smart TVs and streaming devices, offering an optimized user interface for TVs and remote navigation, integrated Google Assistant, built-in Chromecast,…
Recent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
