Port of Seattle hit by Rhysida ransomware in August attack
by nlqip

Port of Seattle, the United States government agency overseeing Seattle’s seaport and airport, confirmed on Friday that the Rhysida ransomware operation was behind a cyberattack impacting its systems over the last three weeks.
The agency revealed on August 24 that the attack forced it to isolate some of its critical systems to contain the impact. The resulting IT outage disrupted reservation check-in systems and delayed flights at Seattle-Tacoma International Airport.
Today, three weeks after the initial disclosure, the Port officially confirmed that the August breach was a ransomware attack coordinated by Rhysida ransomware affiliates.
“This incident was a “ransomware” attack by the criminal organization known as Rhysida. There has been no new unauthorized activity on Port systems since that day. It remains safe to travel from Seattle-Tacoma International Airport and use the Port of Seattle’s maritime facilities,” it said in a press release.
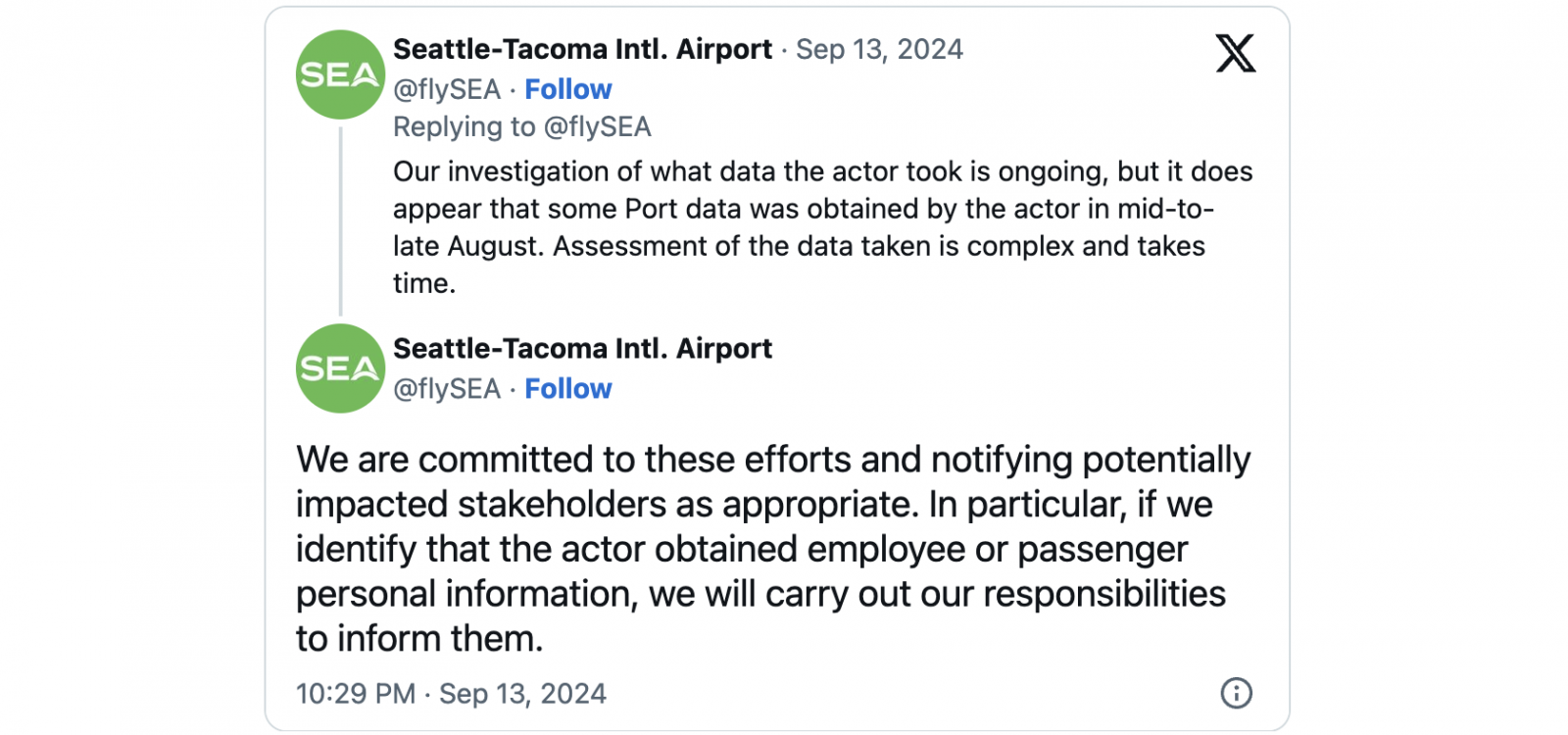
“Our investigation has determined that the unauthorized actor was able to gain access to certain parts of our computer systems and was able to encrypt access to some data.”
The Port’s decision to take systems offline and the ransomware gang encrypting those that weren’t isolated in time caused outages impacting multiple services and systems, including baggage, check-in kiosks, ticketing, Wi-Fi, passenger display boards, the Port of Seattle website, the flySEA app, and reserved parking.
While the Port has already brought most affected systems back online within the week, it’s still working on restoring other key services, like the Port of Seattle website, SEA Visitor Pass, TSA wait times, and flySEA app access (unless downloaded before the August ransomware attack).
The Port has also decided not to give into the ransomware gang’s demands to pay for a decryptor even though the attackers would likely publish data stolen in mid-to-late August on their dark web leak site.
“The Port of Seattle has no intent of paying the perpetrators behind the cyberattack on our network,” said Steve Metruck, Executive Director of the Port of Seattle. “Paying the criminal organization would not reflect Port values or our pledge to be a good steward of taxpayer dollars.”
Rhysida is a relatively new ransomware-as-a-service (RaaS) operation that surfaced in May 2023 and quickly gained notoriety after breaching the British Library and the Chilean Army (Ejército de Chile).
The U.S. Department of Health and Human Services (HHS) linked Rhysida to attacks against healthcare organizations. At the same time, CISA and the FBI warned that this cybercrime gang was also behind many opportunistic attacks targeting victims across a wide range of other industry sectors.
For instance, in November, Rhysida breached Sony subsidiary Insomniac Games and leaked 1,67 TB of documents on the dark web after the game studio refused to pay a $2 million ransom.
Its affiliates have also breached the City of Columbus, Ohio, MarineMax (the world’s largest recreational boat and yacht retailer), and the Singing River Health System. The latter warned almost 900,000 people that their data had been stolen in an August 2023 Rhysida ransomware attack.
Source link
lol
Image: MidjourneyPort of Seattle, the United States government agency overseeing Seattle’s seaport and airport, confirmed on Friday that the Rhysida ransomware operation was behind a cyberattack impacting its systems over the last three weeks. The agency revealed on August 24 that the attack forced it to isolate some of its critical systems to contain the…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA