Exploit code released for critical Ivanti RCE flaw, patch now
by nlqip

A proof-of-concept (PoC) exploit for CVE-2024-29847, a critical remote code execution (RCE) vulnerability in Ivanti Endpoint Manager, is now publicly released, making it crucial to update devices.
The flaw is a deserialization of untrusted data issue impacting Ivanti Endpoint Manager before 2022 SU6 and EPM 2024, which was fixed as part of the September 2024 update on September 10, 2024.
The vulnerability was discovered by security researcher Sina Kheirkhah (@SinSinology), who reported it through the Zero Day Initiative (ZDI) on May 1, 2024.
The same researcher has now published the full details on how CVE-2024-29847 can be exploited, which will likely fuel attacks in the wild.
The CVE-2024-29847 flaw
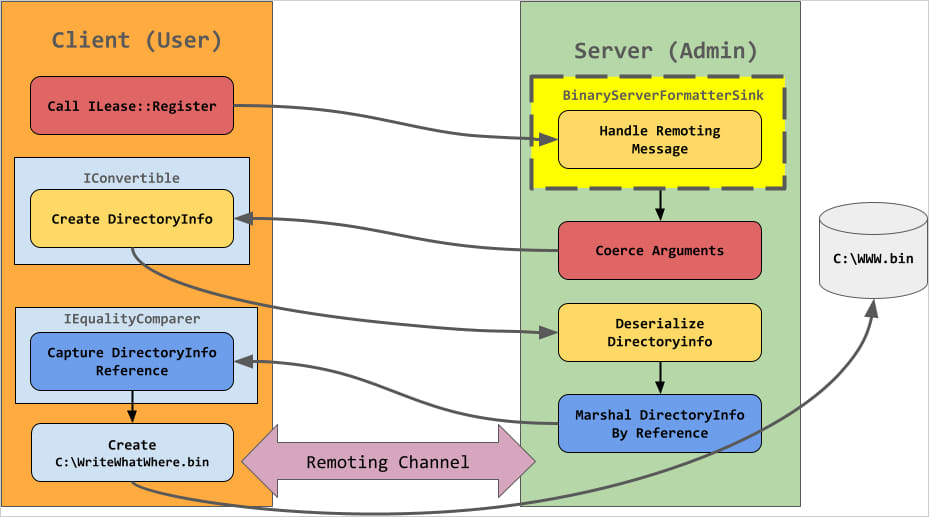
The root cause of the flaw lies in the insecure deserialization within the AgentPortal.exe executable, specifically, the OnStart method of the service, which uses the deprecated Microsoft .NET Remoting framework to facilitate communication between remote objects.
The service registers a TCP channel with dynamically assigned ports and no security enforcement, making it possible for a remote attacker to inject malicious objects.
Kheirkhah’s attack flow involves crafting a Hashtable containing serialized objects to send to the vulnerable endpoint, which, upon deserialization, executes arbitrary operations by calling methods on the DirectoryInfo or FileInfo objects.
These enable the attacker to perform file operations such as reading or writing files on the server, including web shells that can execute arbitrary code.
It is noted in the write-up that a low-type filter restricts which objects can be deserialized. However, using a technique described by James Forshaw, it’s possible to bypass the security mechanism.
Source: summoning.team
Patch now!
Ivanti has made a security ‘hot patch’ available for EPM 2022 and 2024, with SU6 and September 2024 updates, respectively.
The vendor offers no other mitigations or workarounds, so applying the security update in the bulletin is the only recommendation.
In January, CISA warned that a critical authentication bypass vulnerability in Ivanti’s Endpoint Manager Mobile product was actively exploited in attacks.
Last week, Ivanti confirmed that hackers are actively exploiting a high-severity remote code execution flaw, tracked as CVE-2024-8190, in its Cloud Services Appliance (CSA).
CISA also added the flaw to its Known Exploited Vulnerabilities catalog, setting the deadline to secure vulnerable appliances to October 4, 2024.
Source link
lol
A proof-of-concept (PoC) exploit for CVE-2024-29847, a critical remote code execution (RCE) vulnerability in Ivanti Endpoint Manager, is now publicly released, making it crucial to update devices. The flaw is a deserialization of untrusted data issue impacting Ivanti Endpoint Manager before 2022 SU6 and EPM 2024, which was fixed as part of the September 2024…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
