Temu denies breach after hacker claims theft of 87 million data records
by nlqip

Temu denies it was hacked or suffered a data breach after a threat actor claimed to be selling a stolen database containing 87 million records of customer information.
The threat actor put the alleged data up for sale yesterday on the BreachForums hacking forum, along with a small sample to serve as proof of the stolen data.
Temu says it has examined and cross-checked the data samples with its database, but no matches were found.
Hacker claims to breach Temu
Temu is a rapidly growing e-commerce platform offering a wide range of products at competitive prices, focusing on low-cost clothing, home goods, electronics, and accessories.
Temu is Chinese but operates globally, including in Europe and the United States, where it gained popularity for its deep discounts and promotional strategies.
Though Temu has faced scrutiny over concerns relating to data privacy, product quality, and shipping times, it has not found itself at the epicenter of a major data breach incident as of yet.
Yesterday, a threat actor using the moniker ‘smokinthashit’ claimed to have stolen a database with 87 million records from Temu and attempted to sell it to other cybercriminals.
The threat actor published samples of the allegedly stolen data that contained usernames and IDs, IP addresses, full names, dates of birth, gender, shipping addresses, phone numbers, and hashed passwords.
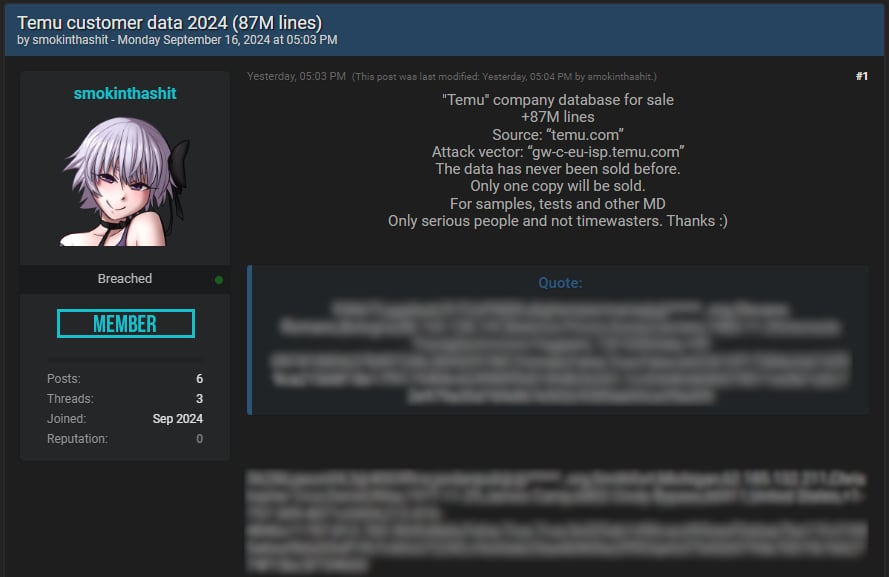
Source: BleepingComputer
Temu says it wasn’t breached
Responding to BleepingComputer’s request for comment, Temu categorically denied the published data is theirs and said it would press charges against those spreading this misinformation.
“Temu’s security team has conducted a comprehensive investigation into the alleged data breach and can confirm that the claims are categorically false; the data being circulated is not from our systems. Not a single line of data matches our transaction records,” Temu told BleepingComputer.
“We take any attempt to tarnish our reputation or harm our users extremely seriously and reserve the right to pursue legal action against those responsible for spreading false information and attempting to profit from such malicious activities.”
“At Temu, the security and privacy of our users are paramount. We follow industry-leading practices for data protection and cybersecurity, ensuring that consumers can shop with peace of mind on our platform.”
The e-commerce platform also underlined that it follows industry-leading data protection and cybersecurity practices, noting the app’s MASA certification, independent validations, its HackerOne bug bounty program, and compliance with the PCI DSS payment security standard.
Threat actor says the breach is real
BleepingComputer contacted the threat actor about the breach, and they continued to say they breached Temu.
The threat actor claims to still have access to the company’s email and internal panels, and that there are vulnerabilities in their code.
However, the threat actor did not share any proof of these claims, and BleepingComputer cannot determine whether they are valid.
Whether or not the data breach claims are valid, they can still harm a firm’s reputation and seed distrust in customers.
Out of an abundance of caution, if you are a Temu user, it would be prudent to enable two-factor authentication on your account, change the password to something new and unique, and stay vigilant for potential phishing attempts.
BleepingComputer contacted Temu again about these further claims, but no response was immediately available.
Source link
lol
Temu denies it was hacked or suffered a data breach after a threat actor claimed to be selling a stolen database containing 87 million records of customer information. The threat actor put the alleged data up for sale yesterday on the BreachForums hacking forum, along with a small sample to serve as proof of the stolen…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
