GitLab releases fix for critical SAML authentication bypass flaw
by nlqip

GitLab has released security updates to address a critical SAML authentication bypass vulnerability impacting self-managed installations of the GitLab Community Edition (CE) and Enterprise Edition (EE).
Security Assertion Markup Language (SAML) is a single sign-on (SSO) authentication protocol that allows users to log in across different services using the same credentials.
The flaw, tracked as CVE-2024-45409, arises from an issue in the OmniAuth-SAML and Ruby-SAML libraries, which GitLab uses to handle SAML-based authentication.
The vulnerability occurs when the SAML response sent by an identity provider (IdP) to GitLab contains a misconfiguration or is manipulated.
Specifically, the flaw involves insufficient validation of key elements in the SAML assertions, such as the extern_uid (external user ID), which is used to uniquely identify a user across different systems.
An attacker can craft a malicious SAML response that tricks GitLab into recognizing them as authenticated users, bypassing SAML authentication and gaining access to the GitLab instance.
The CVE-2024-45409 flaw impacts GitLab 17.3.3, 17.2.7, 17.1.8, 17.0.8, 16.11.10, and all prior releases of those branches.
The vulnerability is addressed in GitLab versions 17.3.3, 17.2.7, 17.1.8, 17.0.8, and 16.11.10, where OmniAuth SAML has been upgraded to version 2.2.1 and Ruby-SAML to 1.17.0.
“We strongly recommend that all installations running a version affected by the issues described below are upgraded to the latest version as soon as possible,” warns GitLab in the bulletin.
No action needs to be taken for users of GitLab Dedicated instances on GitLab.com, as the issue impacts only self-managed installations.
For those who cannot upgrade to a safe version immediately, GitLab suggests enabling two-factor authentication (2FA) for all accounts, and setting the SAML 2FA bypass option to “do not allow.”
Signs of exploitation
While GitLab has not stated that the flaw was previously exploited, they did provide signs of attempted or successful exploitation in the bulletin, suggesting that malicious actors might already be leveraging the flaw in attacks.
The signs of attempted or successful exploitation are:
- Errors related to RubySaml::ValidationError (unsuccessful attempts).
- New or unusual extern_uid values in authentication logs (successful attempts).
- Missing or incorrect information in SAML responses.
- Multiple extern_uid values for a single user (indicates potential account compromise).
- SAML authentication from an unfamiliar or suspicious IP address compared to the user’s usual access patterns.
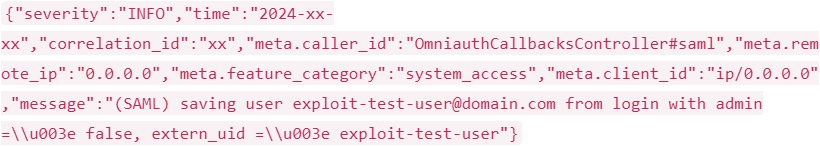
Source: GitLab
BleepingComputer contacted GitLab yesterday to ask about whether or not they have observed active exploitation of CVE-2024-45409 in the wild, but we are still awaiting a response.
Source link
lol
GitLab has released security updates to address a critical SAML authentication bypass vulnerability impacting self-managed installations of the GitLab Community Edition (CE) and Enterprise Edition (EE). Security Assertion Markup Language (SAML) is a single sign-on (SSO) authentication protocol that allows users to log in across different services using the same credentials. The flaw, tracked as…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
