Mysterious “LOVE” packet storms flood the internet since 2020
by nlqip

Internet intelligence firm GreyNoise reports that it has been tracking large waves of “Noise Storms” containing spoofed internet traffic since January 2020. However, despite extensive analysis, it has not concluded its origin and purpose.
These Noise Storms are suspected to be covert communications, DDoS attack coordination signals, clandestine command and control (C2) channels of malware operations, or the result of a misconfiguration.
A curious aspect is the presence of a “LOVE” ASCII string in the generated ICMP packets, which adds further speculation as to their purpose and makes the case more intriguing.
GreyNoise published this information hoping the cybersecurity researchers community can help solve the mystery and uncover what’s causing these strange noise storms.
Characteristics of the noise storms
GreyNoise observes large waves of spoofed internet traffic coming from millions of spoofed IP addresses from various sources such as QQ, WeChat, and WePay.
The “storms” create massive traffic directed to specific internet service providers like Cogent, Lumen, and Hurricane Electric but avoid others, most notably Amazon Web Services (AWS).
The traffic mainly focuses on TCP connections, particularly targeting port 443, but there’s also an abundance of ICMP packets, lately including an embedded ASCII string “LOVE” within them, as shown below.
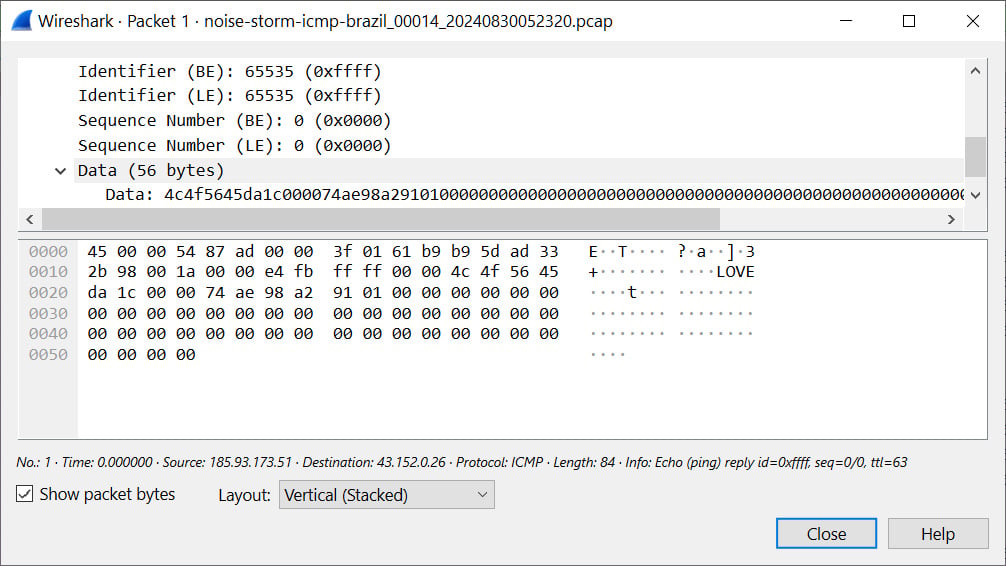
Source: BleepingComputer
The TCP traffic also adjusts parameters such as window sizes to emulate different operating systems, keeping the activity stealthy and difficult to pinpoint.
The Time to Live (TTL) values, which dictate how long a packet stays on the network before it’s discarded, are set between 120 and 200 to resemble realistic network hops.
All in all, the form and characteristics of these “noise storms” indicate a deliberate effort by a knowledgeable actor rather than a large-scale side effect of a misconfiguration.
GreyNoise calls for help
This strange traffic mimics legitimate data streams, and while it’s not known if it’s malicious, its true purpose remains a mystery.
GreyNoise published packet captures (PCAPs) for two recent noise storm events on GitHub, inviting cybersecurity researchers to join in the investigation and contribute their insights or independent discoveries that will help solve this mystery.
“Noise Storms are a reminder that threats can manifest in unusual and bizarre ways, highlighting the need for adaptive strategies and tools that go beyond traditional security measures,” underlines GreyNoise.
You can learn more about these Noise Storms in GreyNoise’s recent Storm Watch video, shown below.
Source link
lol
Internet intelligence firm GreyNoise reports that it has been tracking large waves of “Noise Storms” containing spoofed internet traffic since January 2020. However, despite extensive analysis, it has not concluded its origin and purpose. These Noise Storms are suspected to be covert communications, DDoS attack coordination signals, clandestine command and control (C2) channels of malware operations, or the result…
Recent Posts
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
