Critical Ivanti vTM auth bypass bug now exploited in attacks
by nlqip

CISA has tagged another critical Ivanti security vulnerability, which can let threat actors create rogue admin users on vulnerable Virtual Traffic Manager (vTM) appliances, as actively exploited in attacks.
Tracked as CVE-2024-7593, this auth bypass flaw is caused by an incorrect implementation of an authentication algorithm that lets remote unauthenticated attackers circumvent authentication on Internet-exposed vTM admin panels.
Ivanti vTM is a software-based application delivery controller (ADC) that provides load balancing and traffic management for hosting business-critical services.
“Successful exploitation could lead to authentication bypass and creation of an administrator user,” Ivanti warned when it released security updates to patch this critical vulnerability.
While the company said that proof-of-concept (PoC) exploit code was already available on August 13 when it released CVE-2024-7593 patches, it has yet to update the security advisory to confirm active exploitation.
However, it recommended checking Audit Logs Output for new ‘user1’ or ‘user2’ admin users added via the GUI or the publicly available exploit code to find compromise evidence.
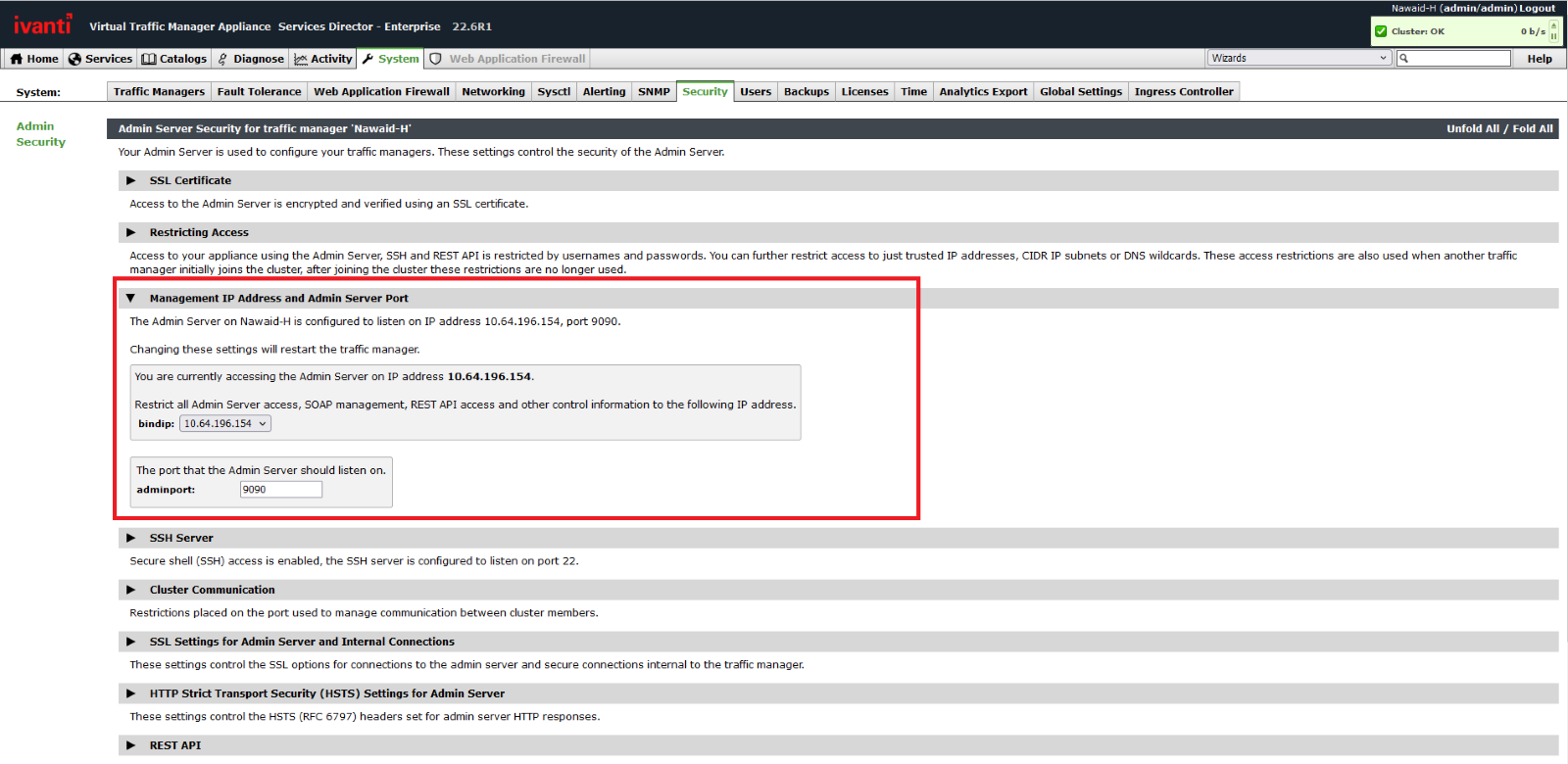
Ivanti also advised admins to restrict access to the vTM management interface by binding it to an internal network or a private IP address to block potential attack attempts and reduce the attack surface.
On Tuesday, CISA added the Ivanti vTM authentication bypass flaw to its Known Exploited Vulnerabilities catalog, tagging it as actively exploited. As Binding Operational Directive (BOD) 22-01) requires, federal agencies now must secure vulnerable appliances on their networks within three weeks by October 15.
CISA’s KEV catalog primarily alerts federal agencies about vulnerabilities they should patch as soon as possible, but private organizations worldwide are also advised to prioritize mitigating this security flaw to block ongoing attacks.
In recent months, several Ivanti flaws have been exploited as zero-days in widespread attacks targeting the company’s VPN appliances and ICS, IPS, and ZTA gateways. The company also warned earlier this month that threat actors are also chaining two recently patched Cloud Services Appliance (CSA) vulnerabilities in ongoing attacks.
Ivanti stated in September that it had enhanced its internal scanning and testing capabilities in response to these attacks and is currently working on improving its responsible disclosure process to address potential security issues even faster.
Ivanti has over 7,000 partners globally, and its products are used by over 40,000 companies for system and IT asset management.
Source link
lol
CISA has tagged another critical Ivanti security vulnerability, which can let threat actors create rogue admin users on vulnerable Virtual Traffic Manager (vTM) appliances, as actively exploited in attacks. Tracked as CVE-2024-7593, this auth bypass flaw is caused by an incorrect implementation of an authentication algorithm that lets remote unauthenticated attackers circumvent authentication on Internet-exposed…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
