Month: September 2024
Sep 23, 2024Ravie LakshmananIoT Security / Vulnerability A critical security flaw has been disclosed in the Microchip Advanced Software Framework (ASF) that, if successfully exploited, could lead to remote code execution. The vulnerability, tracked as CVE-2024-7490, carries a CVSS score of 9.5 out of a maximum of 10.0. It has been described as a stack-based…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/quantum-computing-and-cybersecurity-preparing-for-a-new-age-of-threats” on this server. Reference #18.c5d7ce17.1727085992.4eeaeecf https://errors.edgesuite.net/18.c5d7ce17.1727085992.4eeaeecf Source link lol
Read MoreSep 23, 2024Ravie LakshmananSoftware Security / Supply Chain Threat actors with ties to North Korea have been observed using poisoned Python packages as a way to deliver a new malware called PondRAT as part of an ongoing campaign. PondRAT, according to new findings from Palo Alto Networks Unit 42, is assessed to be a lighter…
Read MoreSep 23, 2024Ravie LakshmananCyber Espionage / Malware A suspected advanced persistent threat (APT) originating from China targeted a government organization in Taiwan, and possibly other countries in the Asia-Pacific (APAC) region, by exploiting a recently patched critical security flaw impacting OSGeo GeoServer GeoTools. The intrusion activity, which was detected by Trend Micro in July 2024,…
Read MoreData Exfiltration Extortion Now Averages $5.21 Million According to IBM’s Report | BlackFog
by nlqip
According to IBM’s 2024 Data Breach Report, the financial toll of data exfiltration extortion has surged, with the average cost now reaching $5.21 million per incident. This alarming trend highlights the growing sophistication of cybercriminals and the increasing financial risks organizations face when sensitive data is compromised. As data breaches continue to escalate, businesses must…
Read MoreA massive infostealer malware operation encompassing thirty campaigns targeting a broad spectrum of demographics and system platforms has been uncovered, attributed to a cybercriminal group named “Marko Polo.” The threat actors use a variety of distribution channels, including malvertising, spearphishing, and brand impersonation in online gaming, cryptocurrency, and software, to spread 50 malware payloads, including…
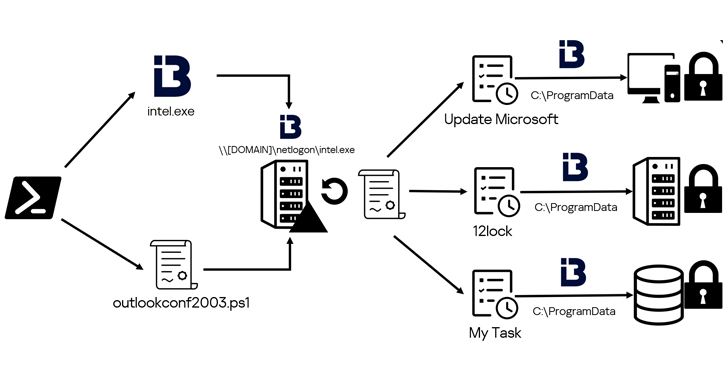
Read MoreA hacktivist group known as Twelve has been observed using an arsenal of publicly available tools to conduct destructive cyber attacks against Russian targets. “Rather than demand a ransom for decrypting data, Twelve prefers to encrypt victims’ data and then destroy their infrastructure with a wiper to prevent recovery,” Kaspersky said in a Friday analysis.…
Read MoreSep 21, 2024Ravie LakshmananNational Security / Cyber Attack Ukraine has restricted the use of the Telegram messaging app by government officials, military personnel, and other defense and critical infrastructure workers, citing national security concerns. The ban was announced by the National Coordination Centre for Cybersecurity (NCCC) in a post shared on Facebook. “I have always…
Read MoreSep 21, 2024Ravie LakshmananPrivacy / Artificial Intelligence The U.K. Information Commissioner’s Office (ICO) has confirmed that professional social networking platform LinkedIn has suspended processing users’ data in the country to train its artificial intelligence (AI) models. “We are pleased that LinkedIn has reflected on the concerns we raised about its approach to training generative AI…
Read MoreVideo With just weeks to go before the US presidential election, the FBI and the CISA are warning about attempts to sow distrust in the electoral process 20 Sep 2024 With just weeks to go before the US presidential election, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) are…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption