Month: September 2024
“This deal is a big accelerant for the NWN platform which is consistent with the approach we have taken over the last five years that has allowed us to quadruple the company from less than $300 million to more than $1 billion,” said NWN Senior Vice President of Corporate Development Matt Curran. NWN Carousel has…
Read MoreUnisys, Fusion Connect, Impact Networking, Tenable, Confluent and Thales are among the vendors to list open positions for channel-related roles. This month, Unisys, Fusion Connect and Impact Networking are among the solution providers to list open positions while Tenable, Confluent and Thales are among the vendors to list open positions for channel-related roles. CRN has…
Read MoreSep 16, 2024Ravie LakshmananFinancial Security / Malware Cybersecurity researchers are continuing to warn about North Korean threat actors’ attempts to target prospective victims on LinkedIn to deliver malware called RustDoor. The latest advisory comes from Jamf Threat Labs, which said it spotted an attack attempt in which a user was contacted on the professional social…
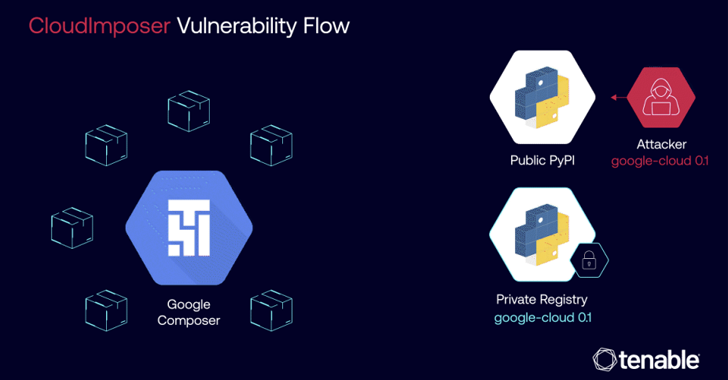
Read MoreSep 16, 2024Ravie LakshmananCloud Security / Vulnerability A now-patched critical security flaw impacting Google Cloud Platform (GCP) Composer could have been exploited to achieve remote code execution on cloud servers by means of a supply chain attack technique called dependency confusion. The vulnerability has been codenamed CloudImposer by Tenable Research. “The vulnerability could have allowed…
Read MoreTenable Research discovered a remote code execution (RCE) vulnerability in Google Cloud Platform (GCP) that is now fixed and that we dubbed CloudImposer. The vulnerability could have allowed an attacker to hijack an internal software dependency that Google pre-installs on each Google Cloud Composer pipeline-orchestration tool. Tenable Research also found risky guidance in GCP documentation…
Read MoreSep 16, 2024The Hacker NewsPayment Security / Data Protection The PCI DSS landscape is evolving rapidly. With the Q1 2025 deadline looming ever larger, businesses are scrambling to meet the stringent new requirements of PCI DSS v4.0. Two sections in particular, 6.4.3 and 11.6.1, are troublesome as they demand that organizations rigorously monitor and manage…
Read MoreSep 16, 2024The Hacker NewsIdentity Protection / Incident Response Imagine this… You arrive at work to a chaotic scene. Systems are down, panic is in the air. The culprit? Not a rogue virus, but a compromised identity. The attacker is inside your walls, masquerading as a trusted user. This isn’t a horror movie, it’s the…
Read MorePerfect Forward Secrecy (PFS) is an important mode of modern encryption that secures the former and future sessions. It remains functional even if the current keys have already been compromised. Its primary function is to safeguard sensitive information, which prevents potential future data breaches. PFS is frequently used in security and privacy protocols across various…
Read MoreUsing Anti Data Exfiltration (ADX) to Stop Ransomware and Other Threats to Data Dr. EDWARD AMOROSO, FOUNDER & CEO, TAG This series of blogs developed by TAG Infosphere highlights a powerful new cybersecurity solution known as Anti Data Exfiltration (ADX) which provides on-device data security and threat protection. Commercial vendor BlackFog pioneered ADX which is…
Read MoreSep 16, 2024Ravie LakshmananSpyware / Threat Intelligence Apple has filed a motion to “voluntarily” dismiss its lawsuit against commercial spyware vendor NSO Group, citing a shifting risk landscape that could lead to exposure of critical “threat intelligence” information. The development was first reported by The Washington Post on Friday. The iPhone maker said its efforts,…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA