Month: September 2024
Critical security vulnerabilities have been disclosed in six different Automatic Tank Gauge (ATG) systems from five manufacturers that could expose them to remote attacks. “These vulnerabilities pose significant real-world risks, as they could be exploited by malicious actors to cause widespread damage, including physical damage, environmental hazards, and economic losses,” Bitsight researcher Pedro Umbelino said…
Read MoreIn today’s digital landscape, website security is paramount. WordPress has become an attractive target for cybercriminals as it continues to dominate the content management system (CMS) market, powering over 40% of all websites. Website owners are constantly seeking robust security solutions to protect their online assets. One question that often arises is: can a SIEM…
Read MoreMicrosoft warns that some Windows 11 systems enter reboot loops or might freeze with blue screens after installing the September 2024 KB5043145 preview update. This month’s KB5043145 optional update was released on Thursday with fixes for multiple issues, including Edge and task manager freezes. One day after this cumulative update rolled out, Redmond added a…
Read MoreOrganizations face an ever-increasing array of sophisticated threats in today’s rapidly evolving cybersecurity landscape. As cyber-attacks become more complex and frequent, the need for robust and efficient security measures has never been more critical. Endpoint Detection and Response (EDR) solutions have emerged as a crucial component of modern cybersecurity strategies. However, the effectiveness of these…
Read MoreImagine a sophisticated cyberattack cripples your organization’s most critical productivity and collaboration tool — the platform you rely on for daily operations. In the blink of an eye, hackers encrypt your emails, files, and crucial business data stored in Microsoft 365, holding it hostage using ransomware. Productivity grinds to a halt and your IT team…
Read MoreUsing Anti Data Exfiltration (ADX) to Stop Ransomware and Other Threats to Data Dr. EDWARD AMOROSO, FOUNDER & CEO, TAG This series of blogs developed by TAG Infosphere highlights a powerful new cybersecurity solution known as Anti Data Exfiltration (ADX) which provides on-device data security and threat protection. Commercial vendor BlackFog pioneered ADX which is…
Read MoreMeta Fined €91 Million for Storing Millions of Facebook and Instagram Passwords in Plaintext
by nlqip
Sep 30, 2024Ravie LakshmananGDPR / Data Privacy The Irish Data Protection Commission (DPC) has fined Meta €91 million ($101.56 million) as part of a probe into a security lapse in March 2019, when the company disclosed that it had mistakenly stored users’ passwords in plaintext in its systems. The investigation, launched by the DPC the…
Read MoreVideo ESET research examines the group’s malicious wares as used to spy on targets in Ukraine in the past two years 27 Sep 2024 This week, ESET researchers published an extensive analysis of the tools and techniques of Gamaredon, a Russia-aligned threat actor that is currently the most active APT group in Ukraine. Their research…
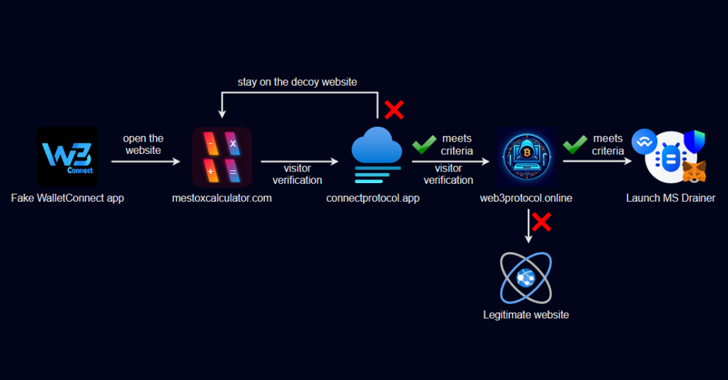
Read MoreSep 28, 2024Ravie LakshmananCryptocurrency / Mobile Security Cybersecurity researchers have discovered a malicious Android app on the Google Play Store that enabled the threat actors behind it to steal approximately $70,000 in cryptocurrency from victims over a period of nearly five months. The dodgy app, identified by Check Point, masqueraded as the legitimate WalletConnect open-source…
Read MoreU.S. federal prosecutors on Friday unsealed criminal charges against three Iranian nationals who are allegedly employed with the Islamic Revolutionary Guard Corps (IRGC) for their targeting of current and former officials to steal sensitive data. The Department of Justice (DoJ) accused Masoud Jalili, 36, Seyyed Ali Aghamiri, 34, and Yasar (Yaser) Balaghi, 37, of participating…
Read MoreRecent Posts
- Enhancing Cyber Resilience in US SLED Organizations
- Stories from the SOC: Registry Clues to PDF Blues: A Tale of…
- DSPM vs CSPM: Key Differences and Their Roles in Data…
- CISA and Partners Release Joint Guidance on PRC-Affiliated Threat Actor Compromising Networks of Global Telecommunications Providers | CISA
- Jack Rhysider Exposes our Digital Secrets