Month: September 2024
IP Infrastructure Analysis, Use of Hosting Infra or Corporate IP Ranges (Geo Location Matching) Scrapers have to distribute their traffic via proxy networks or bot nets so as to spread their traffic over a large number of IP addresses and avoid IP-based rate limits that are used to block unwanted scraping. Because of this, scrapers…
Read MoreHackers are targeting other hackers with a fake OnlyFans tool that claims to help steal accounts but instead infects threat actors with the Lumma stealer information-stealing malware. The operation, discovered by Veriti Research, constitutes a characteristic example of the blurred lines between being a predator or prey in the world of cybercrime, where ironic twists…
Read MoreSep 05, 2024The Hacker NewsThreat Detection / Vulnerability Management It’s been a decade since the National Institute of Standards and Technology (NIST) introduced its Cybersecurity Framework (CSF) 1.0. Created following a 2013 Executive Order, NIST was tasked with designing a voluntary cybersecurity framework that would help organizations manage cyber risk, providing guidance based on established…
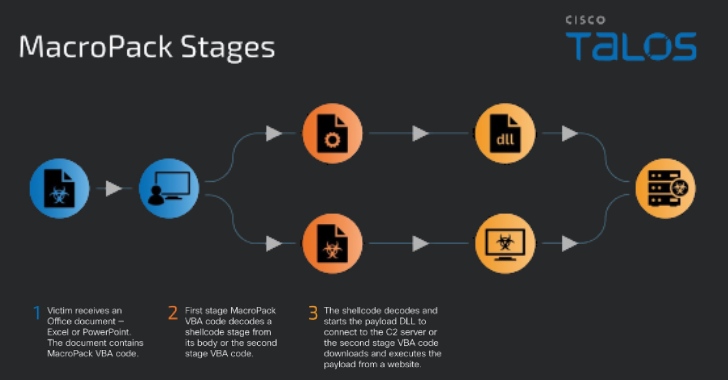
Read MoreThreat actors are likely employing a tool designated for red teaming exercises to serve malware, according to new findings from Cisco Talos. The program in question is a payload generation framework called MacroPack, which is used to generate Office documents, Visual Basic scripts, Windows shortcuts, and other formats for penetration testing and social engineering assessments.…
Read MoreSep 05, 2024Ravie LakshmananCyber Attack / Malware The Chinese-speaking threat actor known as Earth Lusca has been observed using a new backdoor dubbed KTLVdoor as part of a cyber attack targeting an unnamed trading company based in China. The previously unreported malware is written in Golang, and thus is a cross-platform weapon capable of targeting…
Read MorePlanned Parenthood has confirmed it suffered a cyberattack affecting its IT systems, forcing it to take parts of its infrastructure offline to contain the damage. Planned Parenthood is a New York-based nonprofit organization that provides a range of reproductive health care services, education, and advocacy for birth control. It is one of the largest providers…
Read MoreSep 05, 2024Ravie Lakshmanan Cisco has released security updates for two critical security flaws impacting its Smart Licensing Utility that could allow unauthenticated, remote attackers to elevate their privileges or access sensitive information. A brief description of the two vulnerabilities is below – CVE-2024-20439 (CVSS score: 9.8) – The presence of an undocumented static user…
Read MoreBusiness Security Would a more robust cybersecurity posture impact premium costs? Does the policy offer legal cover? These are some of the questions organizations should consider when reviewing their cyber insurance options 04 Sep 2024 • , 3 min. read There must be a consideration of the ethical question of contributing to the payment of…
Read MoreFrontier has a market capitalization of about $10 billion with its stock trading at about $39 a share after market hours Wednesday, up about 11 percent. Verizon is reportedly in talks to buy rival Frontier Communications to grow its fiber network and better compete with AT&T and other rivals. The Basking Ridge, N.J.-based telecommunications vendor…
Read MoreThe MacroPack framework, initially designed for Red Team exercises, is being abused by threat actors to deploy malicious payloads, including Havoc, Brute Ratel, and PhatomCore. Security researchers at Cisco Talos have analyzed malicious document submissions on VirusTotal from various countries, including the United States, Russia, China, and Pakistan. These documents varied in their lures, sophistication, and infection…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA