Month: September 2024
Three men have pleaded guilty to running OTP.Agency, an online platform that provided social engineering help to obtain one-time passcodes from customers of various banks and services in the U.K. The codes – temporary passwords also known as OTPs, were part of multi-factor authentication protections and criminals subscribing to the illegal service could use them to access…
Read MoreOil and gas giant Halliburton has confirmed in a filing today to the Securities and Exchange Commission (SEC) that data was stolen in the recent attack linked to the RansomHub ransomware gang. The form 8-K filing mentions that an unauthorized third party accessed and exfiltrated sensitive information from Halliburton systems, and the company is now…
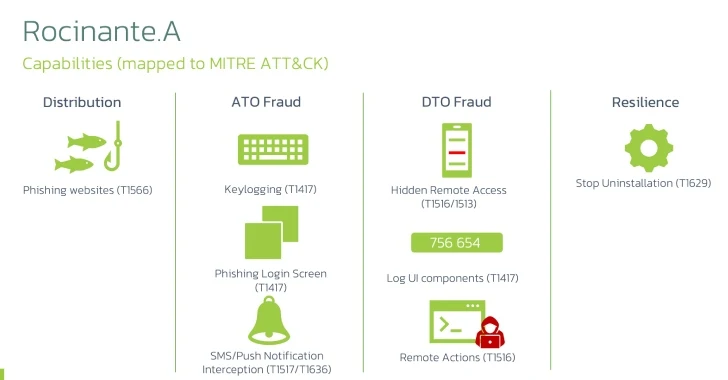
Read MoreRocinante Trojan Poses as Banking Apps to Steal Sensitive Data from Brazilian Android Users
by nlqip
Mobile users in Brazil are the target of a new malware campaign that delivers a new Android banking trojan named Rocinante. “This malware family is capable of performing keylogging using the Accessibility Service, and is also able to steal PII from its victims using phishing screens posing as different banks,” Dutch security company ThreatFabric said.…
Read MoreBackwards compatibility takes us … backwards Unfortunately, once you keep support for old, vulnerable versions of your software, people will continue to use old, vulnerable versions of your software. Vendors shrugged their shoulders, and pundits blamed software users for choosing to use a working-but-vulnerable version instead of a broken-but-patched version (as if that was a…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/the-human-factor-in-cybersecurity-behavioral-insights-and-mitigation-strategies” on this server. Reference #18.ead7ce17.1725358051.c5c0dfce https://errors.edgesuite.net/18.ead7ce17.1725358051.c5c0dfce Source link lol
Read MoreIn the digital realm, secrets (API keys, private keys, username and password combos, etc.) are the keys to the kingdom. But what if those keys were accidentally left out in the open in the very tools we use to collaborate every day? A Single Secret Can Wreak Havoc Imagine this: It’s a typical Tuesday in…
Read MoreOn the other hand, risk tolerance needs to be a guided discussion around a particular objective or a risk scenario, where a CISO can develop a hypothesis. “If you can be explicit, if you can describe it well, then you can really have a good conversation to get everyone on the same page as to…
Read MoreEight vulnerabilities have been uncovered in Microsoft applications for macOS that an adversary could exploit to gain elevated privileges or access sensitive data by circumventing the operating system’s permissions-based model, which revolves around the Transparency, Consent, and Control (TCC) framework. “If successful, the adversary could gain any privileges already granted to the affected Microsoft applications,”…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-094 DATE(S) ISSUED: 09/03/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read MoreSep 03, 2024Ravie LakshmananInsider Threat / Network Security A 57-year-old man from the U.S. state of Missouri has been arrested in connection with a failed data extortion campaign that targeted his former employer. Daniel Rhyne of Kansas City, Missouri, has been charged with one count of extortion in relation to a threat to cause damage…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA