Rackspace monitoring data stolen in ScienceLogic zero-day attack
by nlqip

Cloud hosting provider Rackspace suffered a data breach exposing “limited” customer monitoring data after threat actors exploited a zero-day vulnerability in a third-party tool used by the ScienceLogic SL1 platform.
ScienceLogic confirmed to BleepingComputer that they quickly developed a patch to address the risk and distributed it to all impacted customers while still providing assistance where needed.
“We identified a zero-day remote code execution vulnerability within a non-ScienceLogic third-party utility that is delivered with the SL1 package,” explained a statement from Jessica Lindberg, Vice President at ScienceLogic.
“Upon identification, we rapidly developed a patch to remediate the incident and have made it available to all customers globally.”
ScienceLogic declined to name the third-party utility to avoid providing hints to other hackers, as it might be used on several other products.
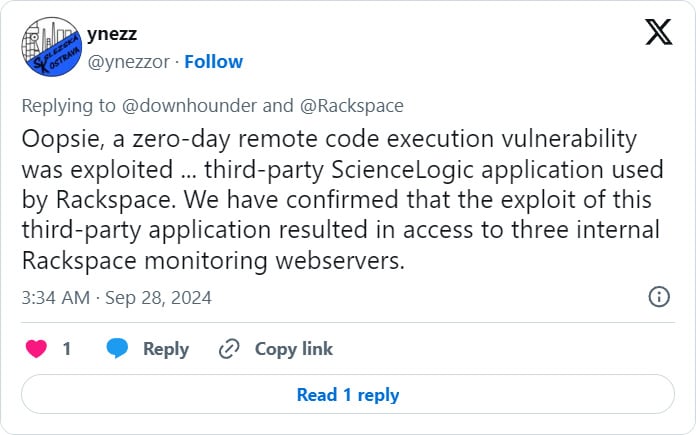
The attack was first disclosed by a user on X who warned that a Rackspace outage from September 24 was due to active exploitation in the hosting provider’s ScienceLogic EM7.
“Oopsie, a zero-day remote code execution vulnerability was exploited … third-party ScienceLogic application used by Rackspace,” an account named ynezz shared on X.
“We have confirmed that the exploit of this third-party application resulted in access to three internal Rackspace monitoring webservers.”
ScienceLogic SL1 (formerly EM7) is an IT operations platform for monitoring, analyzing, and automating an organization’s infrastructure, including cloud, networks, and applications.
It provides real-time visibility, event correlation, and automated workflows to help manage and optimize IT environments efficiently.
Rackspace, a managed cloud computing (hosting, storage, IT support) company, uses ScienceLogic SL1 to monitor its IT infrastructure and services.
In response to the discovery of the malicious activity, Rackspace disabled monitoring graphs on its MyRack portal until they could push an update to remediate the risk.
However, the situation was worse than what a short Rackspace service status update reflected.
As first reported by The Register, Rackspace’s SL1 solution was hacked via the zero-day and some customer information was stolen.
In an email sent to customers and seen by The Register, Rackspace warned that the hackers exploited the zero-day to gain access to web servers and steal limited customer monitoring data, including customer account names and numbers, customer usernames, Rackspace internally generated device IDs, device name and information, IP addresses, and AES256 encrypted Rackspace internal device agent credentials.
Rackspace rotated those credentials as a precaution, despite them being strongly encrypted, and informed customers they needed to take no further action to protect from the malicious activity, which had been stopped.
While the data is limited, it is common for companies to hide their devices’ IP addresses behind content delivery systems and DDoS mitigation platforms. Threat actors could use the exposed IP addresses to target company’s devices in DDoS attacks or further exploitation attempts.
It is unknown how many customers have been impacted by this breach.
BleepingComputer contacted RackSpace with further questions but did not receive a response.
Source link
lol
Cloud hosting provider Rackspace suffered a data breach exposing “limited” customer monitoring data after threat actors exploited a zero-day vulnerability in a third-party tool used by the ScienceLogic SL1 platform. ScienceLogic confirmed to BleepingComputer that they quickly developed a patch to address the risk and distributed it to all impacted customers while still providing assistance…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA