Launching critical severity in Acunetix Standard & Premium
by nlqip
With the release of Acunetix Standard and Acunetix Premium versions 23.8 and 23.9 comes the addition of critical severity as a new vulnerability classification.
Find out which vulnerabilities have changed to critical here.
What’s changing?
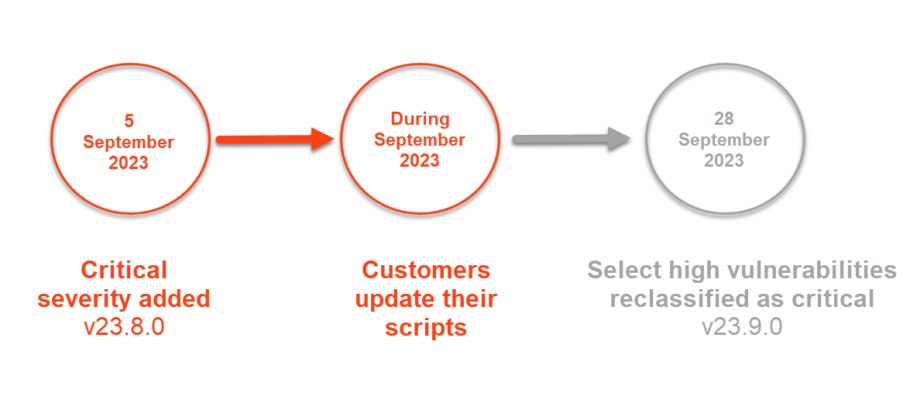
Our vulnerability classification system (High-Medium-Low) has expanded to include a fourth threat level — Critical Severity. On 5 September 2023, we added Critical Severity and Threat Level 4 throughout the products as part of the 23.8 release. At that time, there was no change in the product behavior. All critical vulnerabilities remained categorized as High.
The second stage of implementation came with the release of v23.9 at the end of September 2023. At this time, we reclassified selected vulnerabilities from High to Critical. We deliberately chose to implement these changes in two stages so that our customers who extract data via APIs had time to update their scripts before the reclassification came into effect.
We encouraged all customers using API integrations or workflows to prepare for the reclassification of select vulnerabilities from High to Critical by updating their scripts to account for the new critical severity threat level. More on this below.
You can find the current list of all vulnerabilities and their severity classification on our website.
Timeline
Why are we making this change?
Currently, Acunetix Standard and Acunetix Premium classify all critical level vulnerabilities as ‘high’. This differs from other IT industry security standards and frameworks, which include a ‘critical’ severity rating for security vulnerabilities. By adding a fourth ‘critical’ threat level, we are bringing both products in line with modern classification systems, such as the Common Vulnerability Scoring System (CVSS).
How do I prepare for this change?
If you leverage our API, we recommend obtaining the latest API documentation and updating your internal scripts that work with data from Acunetix. You can download the latest API documentation from the Acunetix user interface by clicking your name in the top-right corner and selecting Profile. Then click the Acunetix API Documentation link that is listed in the API Key section of your profile.
Shown below is a list of endpoints where the critical severity level has been added. For some endpoint responses (e.g. scan-related or vulnerability-related endpoints), critical severity is referred to as the criticality of a vulnerability. Other endpoint responses, such as target or target group-related endpoints, now include severity counts (e.g. criticality=30). Here is an example of how critical severity is now shown in the API documentation:
Endpoints with critical severity added
/config/agents
/reports
/scans
/scans/{scan_id}
/scans/{scan_id}/results/{result_id}/crawldata
/scans/{scan_id}/results/{result_id}/crawldata/{loc_id}
/scans/{scan_id}/results/{result_id}/crawldata/{loc_id}/vulnerabilities
/scans/{scan_id}/results/{result_id}/statistics
/scans/{scan_id}/results/{result_id}/technologies
/scans/{scan_id}/results/{result_id}/vulnerabilities
/scans/{scan_id}/results/{result_id}/vulnerability_types
/scans/{scan_id}/results/{result_id}/vulnerabilities/{vuln_id}
/targets
/targets/add
/targets/cvs_export
/targets/{target_id}
/targets/{target_id}/technologies/{tech_id}/vulnerabilities
/target_groups
/target_groups/{group_id}
/target_groups/{group_id}/scan
/vulnerabilities
/vulnerabilities/{vuln_id}
/vulnerability_types
/vulnerability_groups
/me/license/fqdns
/me/stats
/web_assets
/events
/notifications
/users
/user_groups
/rolesHere is an example of the new criticality parameter in practice:
Frequently asked questions
Your scan results prior to the 28 September 2023 release will remain, but you will notice that some previously ‘High’ vulnerabilities have been reclassified as ‘Critical’. Historical trend charts and reports won’t change.
Critical severity is used in other IT industry security standards and frameworks for rating vulnerabilities. Adding critical severity brings Acunetix in line with modern classification systems such as the Common Vulnerability Scoring System (CVSS).
Currently no vulnerabilities have changed to critical. The reclassification of selected vulnerabilities from high to critical will occur with the release of v23.9.0 on 28 September 2023.
The current list of vulnerabilities and their severity classification will be updated and published on the Acunetix website with the release of v23.9.0 at the end of September.
Some ‘High’ vulnerabilities from scans launched prior to updating to version 23.9 will change to ‘Critical’. For example: RCE (Remote Code Execution), SQLi (SQL injection), and XSS (Cross-site scripting) vulnerabilities will newly show as critical.
Vulnerabilities found by a newly launched scan after updating to v23.9.0 will be classified using the new threat levels – critical, high, medium, low, and informational.
Get the latest content on web security
in your inbox each week.
THE AUTHOR

Anna Wratislav
Senior Technical Writer
Source link
lol
With the release of Acunetix Standard and Acunetix Premium versions 23.8 and 23.9 comes the addition of critical severity as a new vulnerability classification. Find out which vulnerabilities have changed to critical here. What’s changing? Our vulnerability classification system (High-Medium-Low) has expanded to include a fourth threat level — Critical Severity. On 5 September 2023,…
Recent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher


