European govt air-gapped systems breached using custom malware
by nlqip

An APT hacking group known as GoldenJackal has successfully breached air-gapped government systems in Europe using two custom toolsets to steal sensitive data, like emails, encryption keys, images, archives, and documents.
According to an ESET report, this happened at least two times, one against the embassy of a South Asian country in Belarus in September 2019 and again in July 2021, and another against a European government organization between May 2022 and March 2024.
In May 2023, Kaspersky warned about GoldenJackal’s activities, noting that the threat actors focus on government and diplomatic entities for purposes of espionage.
Although their use of custom tools spread over USB pen drives, like the ‘JackalWorm,’ was known, cases of a successful compromise of air-gapped systems were not previously confirmed.
Air-gapped systems are used in critical operations, which often manage confidential information, and are isolated from open networks as a protection measure.
Entering through the (air)gap
The older attacks seen by ESET begin by infecting internet-connected systems, likely using trojanized software or malicious documents, with a malware called ‘GoldenDealer.’
GoldenDealer monitors for the insertion of USB drives on those systems, and when it happens, it automatically copies itself and other malicious components onto it.
Eventually, that same USB drive is inserted into an air-gapped computer, allowing GoldenDealer to install GoldenHowl (a backdoor) and GoldenRobo (a file stealer) onto these isolated systems.
During this phase, GoldenRobo scans the system for documents, images, certificates, encryption keys, archives, OpenVPN configuration files, and other valuable info and stores them in a hidden directory on the USB drive.
When the USB drive is removed from the air-gapped computer and re-connected to the original internet-connected system, GoldenDealer automatically sends the stolen data stored on the drive to the threat actor’s command and control (C2) server.
GoldenHowl is a multi-functional Python backdoor that can steal files, facilitate persistence, scan for vulnerabilities, and communicate directly with the C2. ESET says it appears designed to run on internet-connected machines.
.jpg)
Source: ESET
New modular toolset
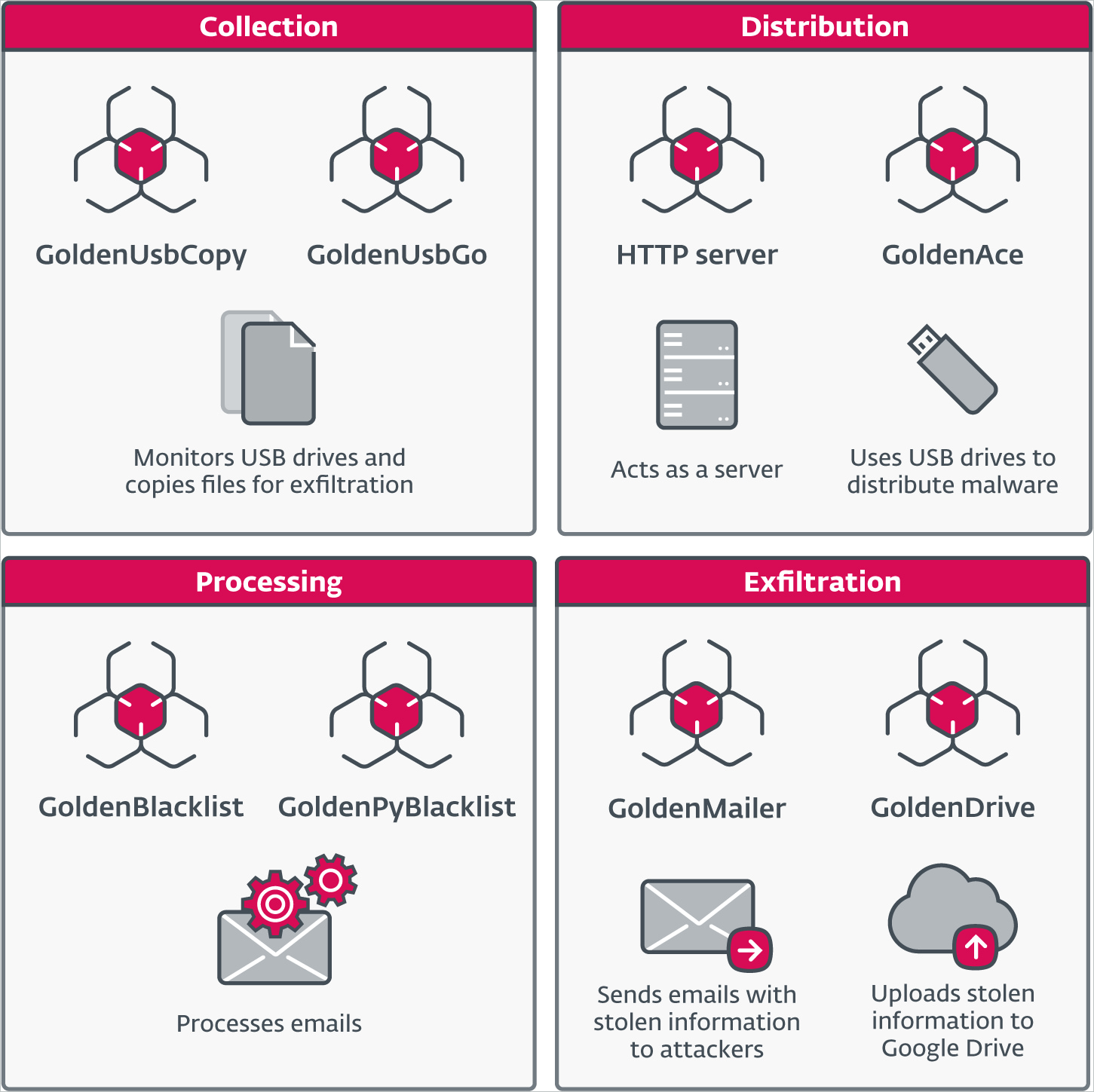
In 2022, GoldenJackal began using a new Go-based modular toolset that performed similar activities to those described in the previous section but allowed the attackers to task different machines with separate roles.
For example, some machines were used for file exfiltration while others acted as file stagers or configuration distribution points.
The new malware used for USB infection is named GoldenAce, and the tools that steal files and send them to the attackers are named ‘GoldenUsbCopy’ and ‘GoldenUsbGo,’ with the latter being a more recent variant of the former.
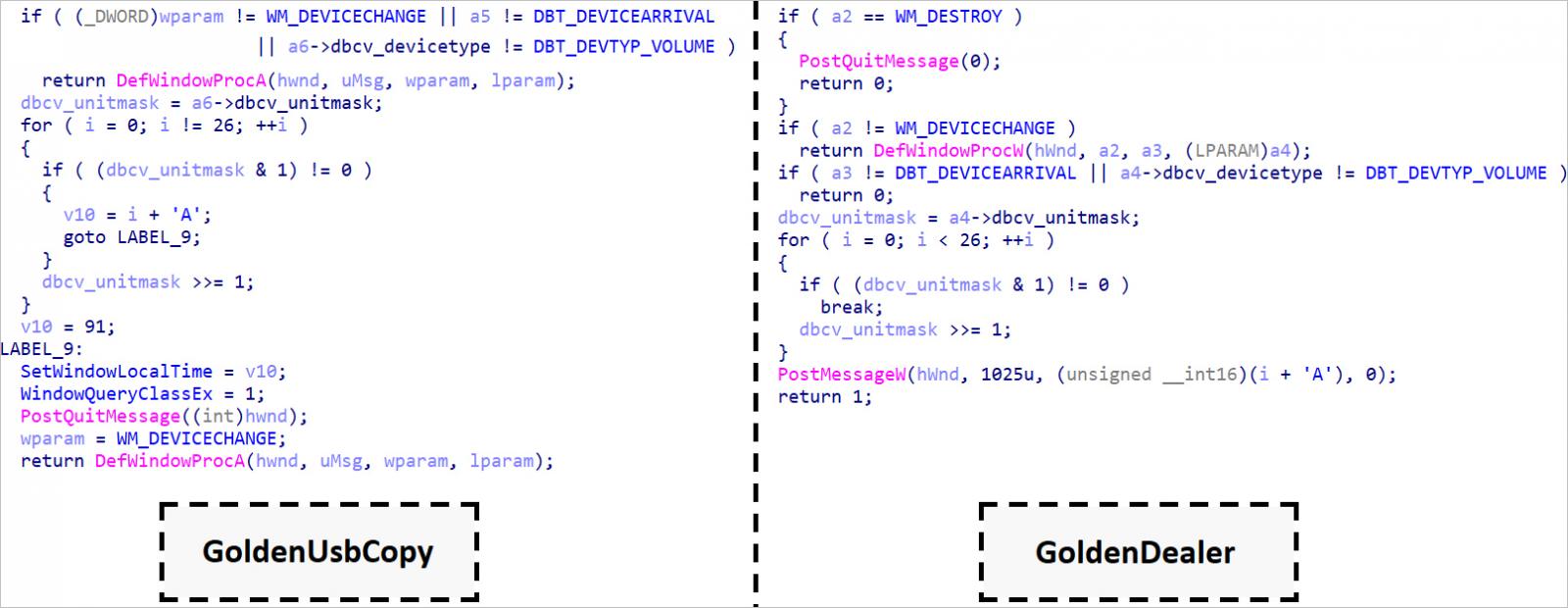
Source: ESET
GoldenUsbGo no longer uses AES-encrypted configuration but instead exfiltrates files based on hardcoded instructions, including recently (up to 14 days) modified files that are smaller than 20 MB and match specific types of content (keywords like “pass”, “login”, or “key”) or certain file types (.pdf, .doc/.docx, .sh, .bat).
Another interesting malware component is GoldenBlacklist (and its Python-based implementation GoldenPyBlacklist), which filters and archives specific email messages from compromised systems before exfiltration.
Finally, there’s GoldenMailer, which emails the stolen information to the attackers, and GoldenDrive, which uploads the data to Google Drive.
Source: ESET
The presence of two toolsets that also overlap with tools described in Kaspersky’s report demonstrates GoldenJackal’s capability to develop new custom malware and optimize it for covert espionage operations.
For a complete list of the indicators of compromise (IoCs) associated with all those tools, you can check out this GitHub page.
Source link
lol
An APT hacking group known as GoldenJackal has successfully breached air-gapped government systems in Europe using two custom toolsets to steal sensitive data, like emails, encryption keys, images, archives, and documents. According to an ESET report, this happened at least two times, one against the embassy of a South Asian country in Belarus in September…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
