How open source SIEM and XDR tackle evolving threats
by nlqip
In today’s cybersecurity landscape, evolving threats require security solutions that match the sophistication of modern threats. As businesses rapidly adopt emerging technologies, their exposure to cyberattacks increases. To mitigate these risks, cybersecurity teams need adaptable and comprehensive tools to protect their digital ecosystems effectively.
Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) platforms play a major role in many organizations’ cybersecurity strategies.
These tools provide robust visibility, real-time monitoring, threat hunting, and automated response capabilities designed to address emerging cyber threats effectively.
The role of SIEM and XDR in modern security
Security Information and Event Management (SIEM) and Extended Detection and Response (XDR) have become integral to comprehensive security strategies. These technologies work together to provide real-time visibility, threat detection, and incident response across an organization’s infrastructure, helping to adequately protect against increasingly sophisticated cyber threats.
SIEM solutions are an essential component of modern cybersecurity frameworks. They collect and analyze log data from various sources, including firewalls, servers, endpoints, and applications, to detect security incidents and suspicious behavior.
By aggregating and analyzing log data, security teams can identify patterns, anomalies, and potential threats, enabling them to address vulnerabilities before they disrupt operations.
XDR extends the capabilities of SIEM by delivering enhanced threat detection and response across multiple layers of an organization’s IT infrastructure, including endpoints, cloud environments, and networks. While SIEM primarily focuses on log data and events, XDR integrates telemetry from diverse sources to provide a more comprehensive view of potential threats.
This integration enables XDR to detect advanced threats and automate response actions, reducing the manual workload on security teams.
SIEM and XDR form a comprehensive cyber defense mechanism that enhances threat visibility, improves response times, and strengthens modern organizations’ overall security posture. Open source SIEM and XDR platforms leverage community-driven innovation to continuously improve their ability to detect emerging threats.
Benefits of leveraging open source SIEM and XDR
Although many organizations have traditionally used proprietary security solutions, open source SIEM and XDR tools have become increasingly prevalent in recent years. Here’s why:
- Cost-effectiveness: Open source SIEM and XDR tools typically have reduced or no licensing fees, providing advanced security capabilities at lower costs. This can make them suitable for organizations with varying budgets.
- Scalability: These tools are designed to scale, allowing organizations to manage increased workloads and monitor more endpoints as their IT environments grow.
- Flexibility and customization: Open source platforms allow for customization, enabling organizations to adapt features and integrations to their specific security requirements and infrastructure.
- Transparency: With access to the source code, open source tools enable organizations to conduct security audits and verify code integrity, supporting greater control over the software’s reliability and compliance.
Wazuh is a free, open source security platform that provides SIEM and XDR capabilities for cloud and on-premises environments.
It offers comprehensive capabilities, including log data analysis, file integrity monitoring, threat detection, real-time alerting, and automated incident response, enabling effective detection and response to evolving cybersecurity threats.
Here are some use cases where Wazuh detects and responds to emerging attacks:
Malware evasion strategies
Malware remains one of the most common threats attackers use to compromise systems and steal sensitive information. Wazuh provides defense against malware evasion by leveraging its out-of-the-box rulesets designed to detect and alert administrators to any signs of malicious activities.
Wazuh rulesets are pre-configured to monitor various indicators of compromise (IoCs) associated with different malware variants. It allows users to enhance detection capabilities by creating custom rules and decoders to target specific activities or threats unique to their IT environment.
These custom configurations enable organizations to fine-tune the Wazuh capability to detect more specialized or targeted attacks.
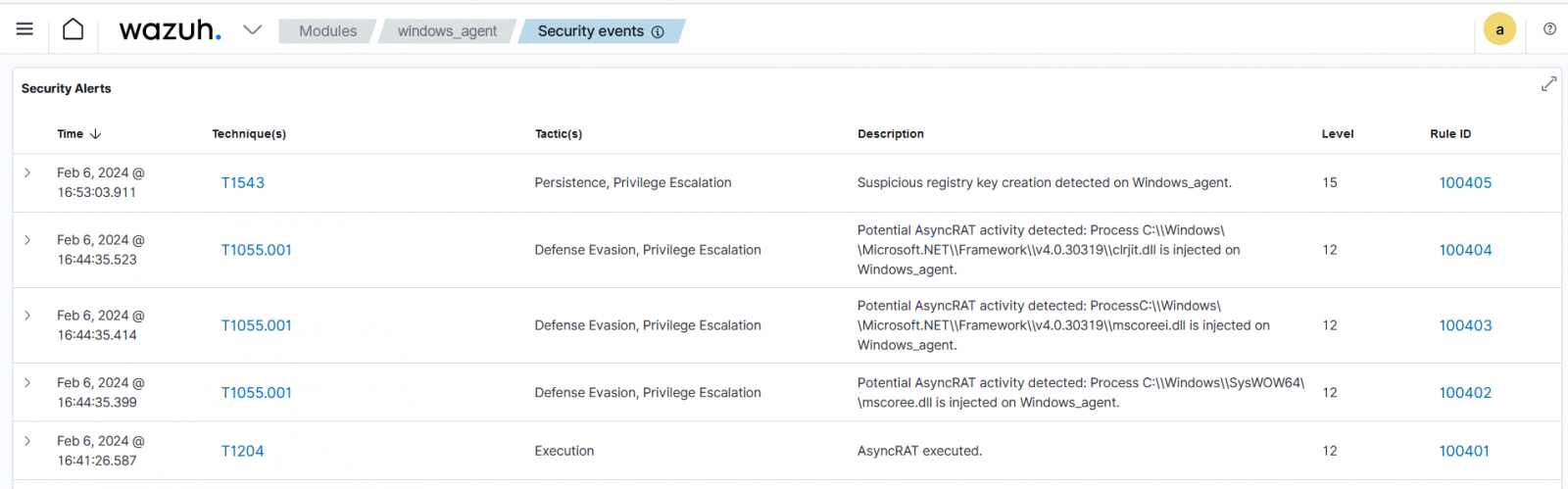
For example, you can configure Wazuh to detect AsyncRAT, an administrator remote access tool commonly used by attackers to gain unauthorized control over compromised systems.
The Wazuh agent gathers logs from the Windows event channel and sends them to the Wazuh server for analysis. The logs are filtered to detect AsyncRAT execution, related system registry modifications, and other suspicious activities that indicate the presence of this malware.
Ransomware attacks
Ransomware is a destructive and high-profile cyber threat. A successful ransomware attack can cause devastating damage, often leading to significant financial losses and downtime.
Wazuh offers capabilities for detecting early signs of ransomware attacks, enabling a quick response to minimize damage. Ransomware typically exhibits several telltale signs, such as unusual file access patterns, encryption of large numbers of files, or communication with known ransomware command and control (C2) servers.
Wazuh capabilities, such as file integrity monitoring (FIM), run periodic scans on specific paths and monitor specific directories within Wazuh agents for changes in real-time.
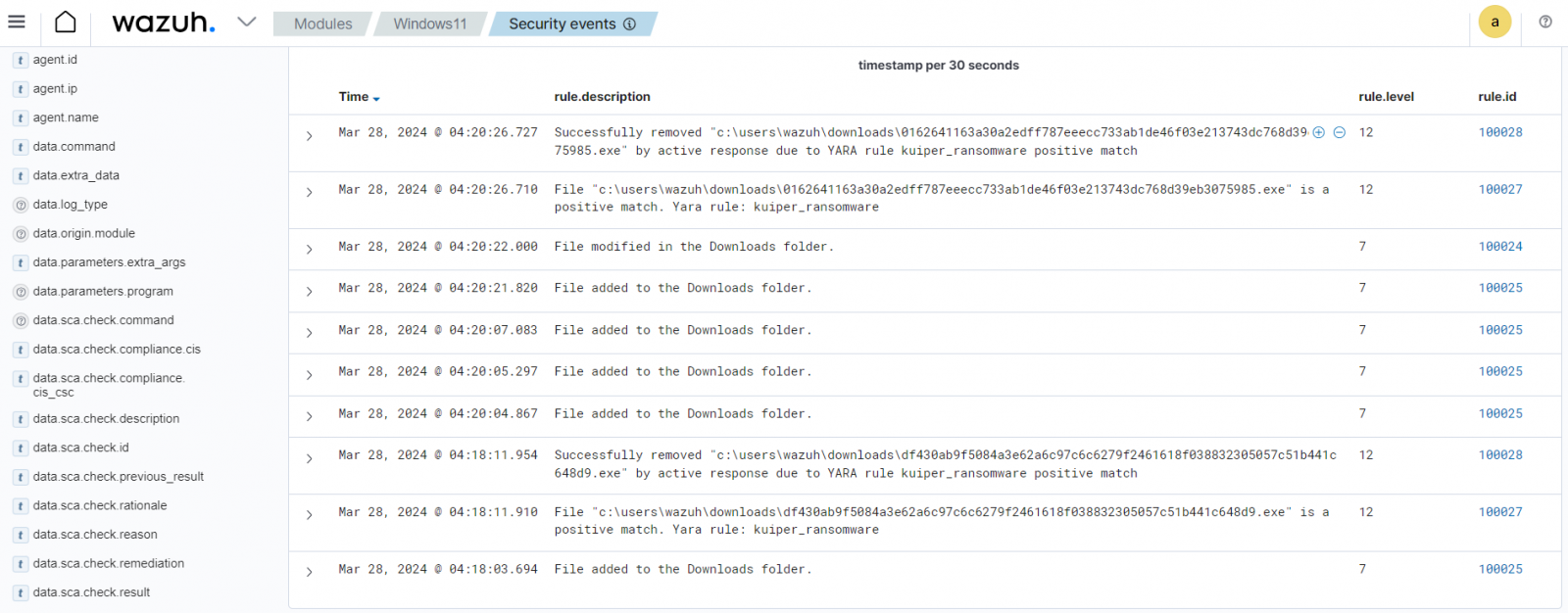
The blog post on Kuiper ransomware detection and response with Wazuh demonstrates how users can combine Wazuh and YARA to secure monitored endpoints against ransomware.
By leveraging Wazuh File Integrity Monitoring capability with YARA scan, users receive alerts when specific ransomware signatures are detected on monitored endpoints. This enables rapid identification and response to threats. An active response script on the monitored endpoint triggers YARA scans to check all added, modified, and deleted files for specific ransomware patterns.
If a malicious file is detected, the script automatically attempts to remove it.
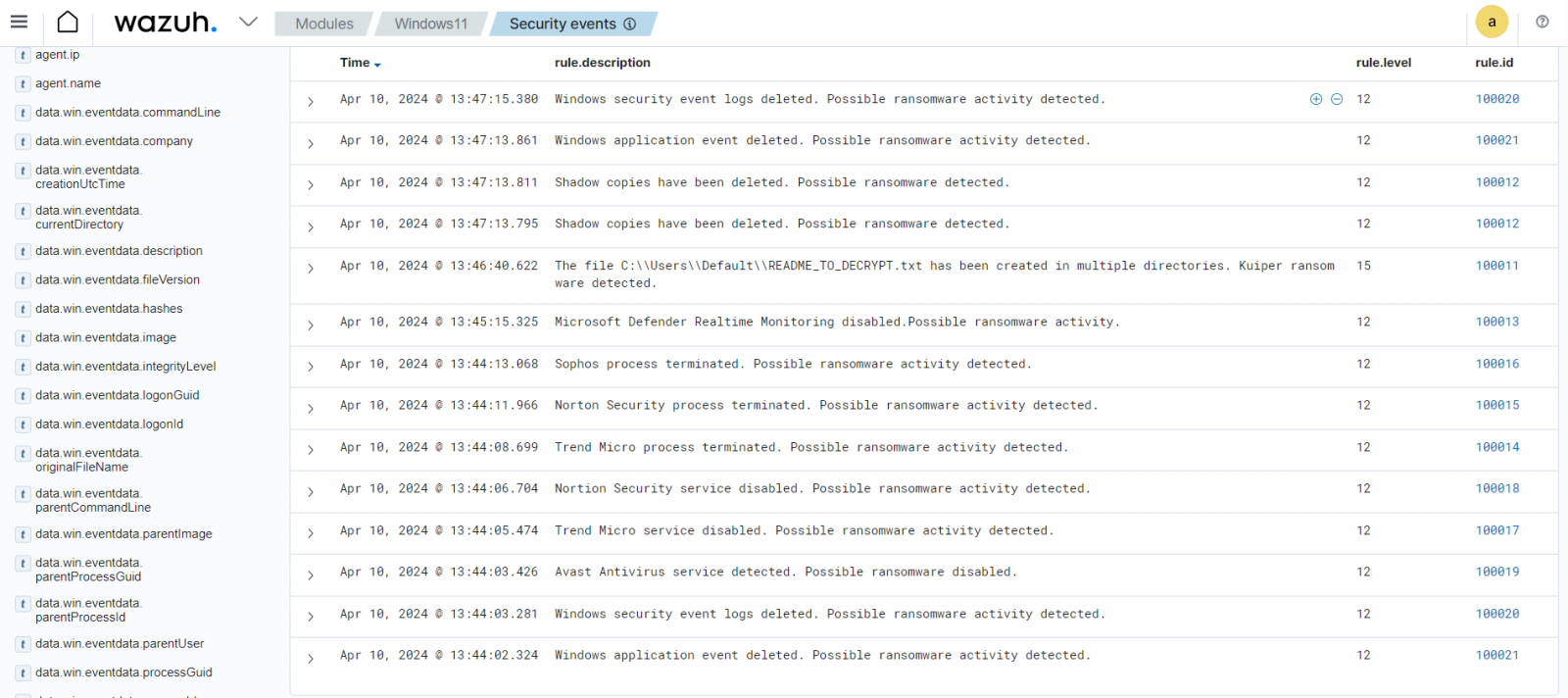
Ransomware attacks can be automatically mitigated with the Wazuh active response capability.
Living off the Land attacks
Living off the Land (LOTL) attacks involve attackers using legitimate tools on the victim’s endpoint to perform malicious actions, making detection more difficult.
Common examples include the use of PowerShell, Windows Management Instrumentation (WMI), or other native system utilities to execute malicious commands or scripts.
LOTL attacks often evade traditional detection methods as they typically avoid deploying malware. Wazuh tackles this emerging threat by monitoring system behavior and identifying unusual usage of legitimate tools, enabling the detection of these subtle activities.
Wazuh provides command monitoring capability which monitors the output of specific executed commands on monitored endpoints. Users can configure Wazuh to capture and log details about the output of specific commands, offering visibility into unusual resource usage by system processes.
In the blog post monitoring Windows resources with Performance Counters, users can leverage Wazuh to track system resources like CPU, RAM, disk, and network traffic on monitored endpoints. Using the Wazuh command monitoring capability, you can configure wodle commands to run the Get-Counter cmdlet on the monitored endpoints and send the output to the Wazuh server for analysis.
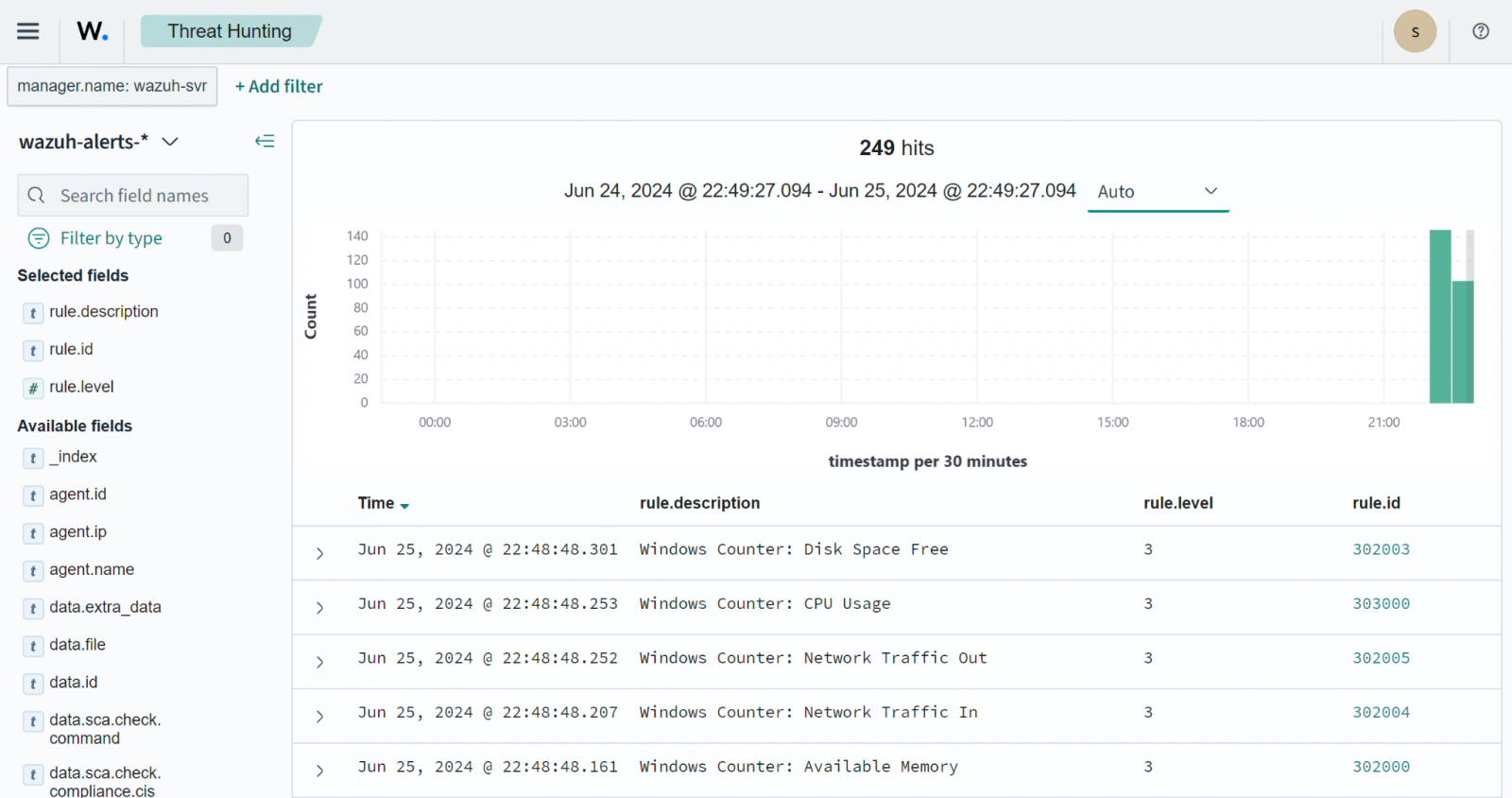
Vulnerability exploitation
Exploiting unpatched vulnerabilities remains a common attack vector for cybercriminals, who target outdated systems or software flaws to gain unauthorized access. These vulnerabilities often serve as the entry point for further attacks, such as remote code execution or malware installation.
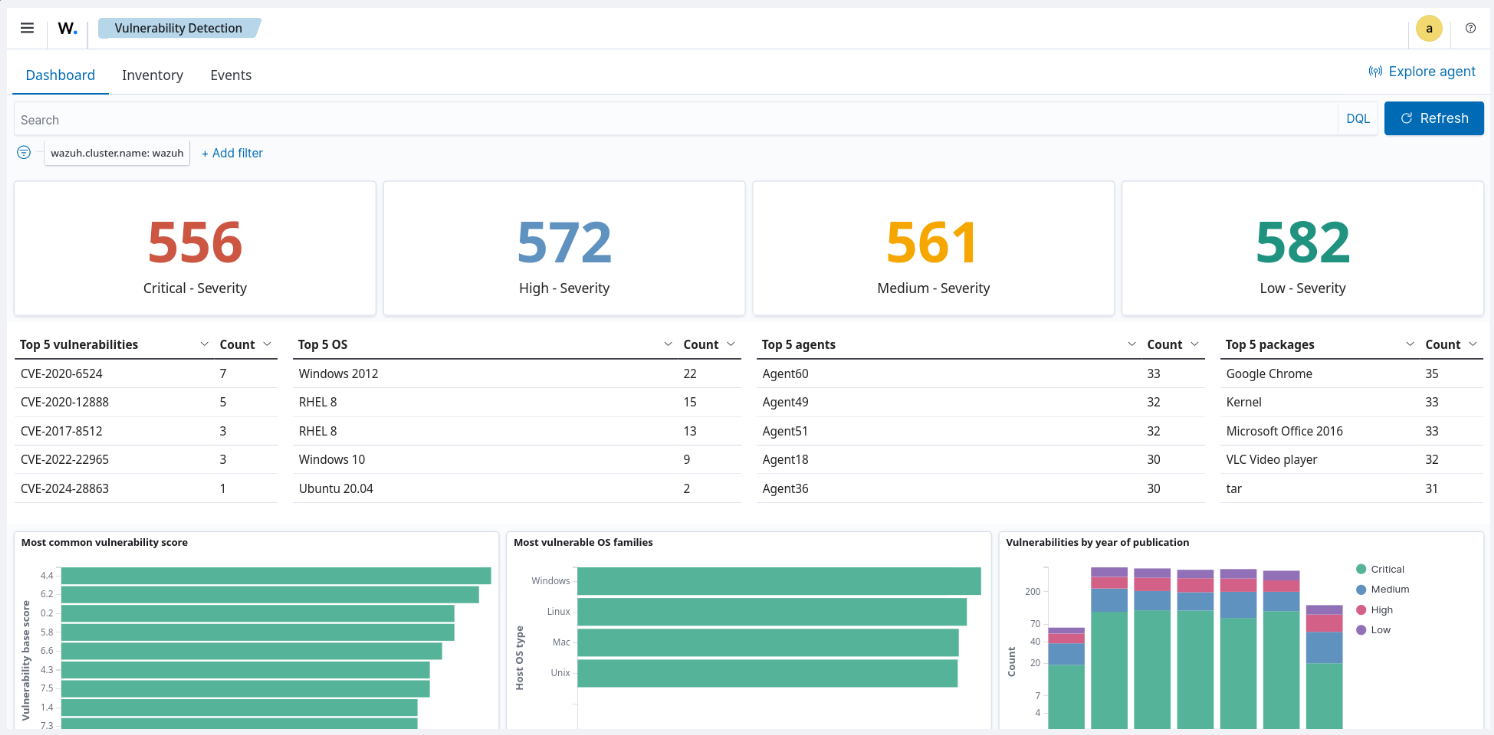
Wazuh offers a vulnerability detection capability that periodically scans operating systems and applications for vulnerabilities on monitored endpoints. It uses data from the Wazuh Cyber Threat Intelligence (CTI) platform, local repositories, and external sources like Canonical, Debian, Red Hat, ALAS, Microsoft, and the National Vulnerability Database (NVD).
This enables the detection of outdated software packages, with detailed vulnerability reports readily accessible on the Wazuh dashboard for easy monitoring and analysis.
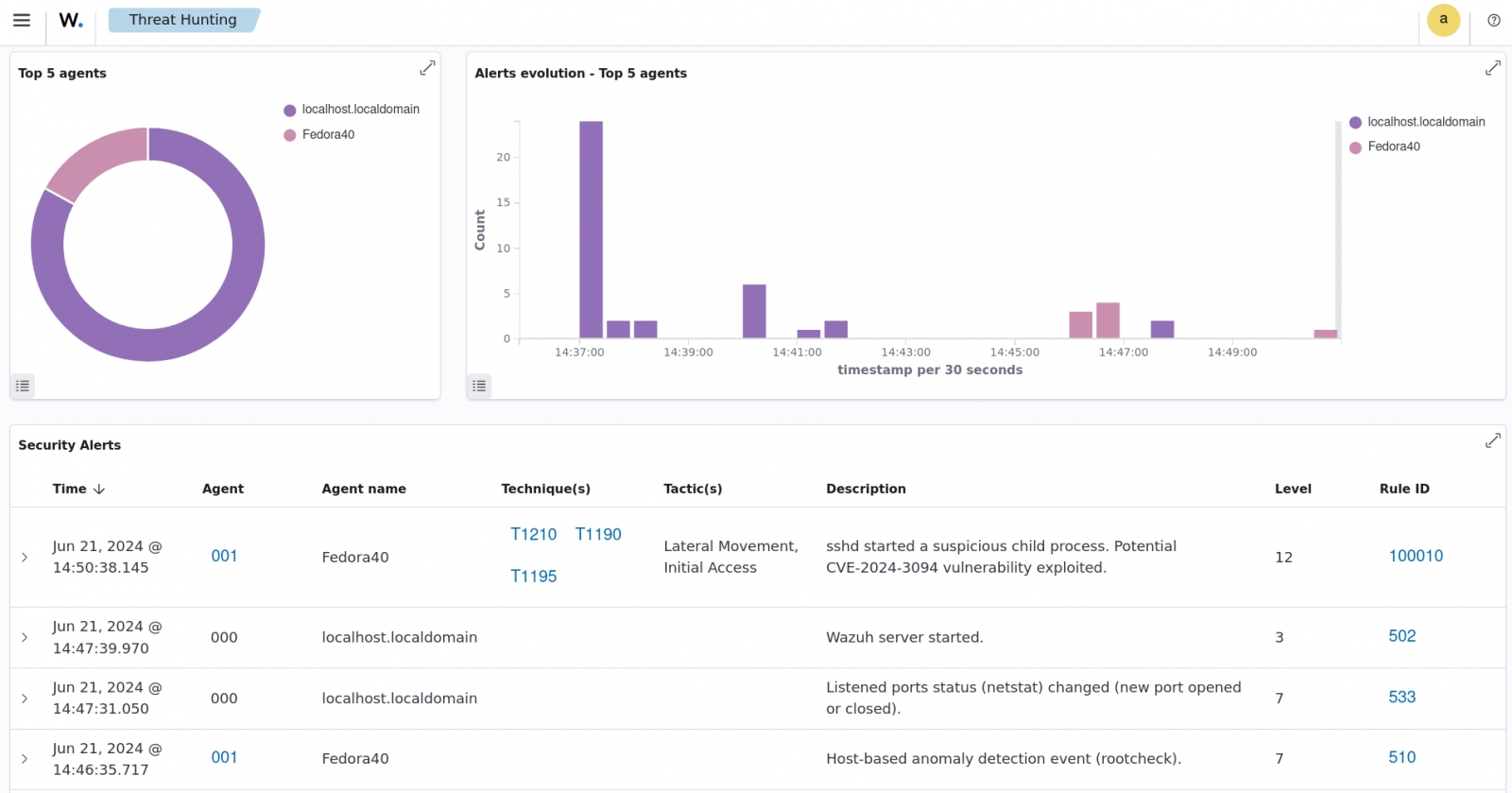
The blog post on detecting the XZ Utils vulnerability exploitation with Wazuh demonstrates how users can identify potential exploitation of CVE-2024-3094 on their monitored endpoints. Users can configure Wazuh agents to detect and send logs related to suspicious sshd child processes to the Wazuh server for further analysis.
Conclusion
Utilizing a robust security approach is essential in the face of emerging threats. Wazuh SIEM and XDR security platform provides this with centralized visibility, automated responses, real-time insights into potential threats, and other capabilities.
By leveraging Wazuh, organizations can be better prepared to identify and mitigate threats. Wazuh also supports integration with third-party solutions to fit your specific use case and address the unique aspects of your IT environment.
Discover more about Wazuh by exploring their documentation and joining their community for professional support.
Sponsored and written by Wazuh.
Source link
lol
In today’s cybersecurity landscape, evolving threats require security solutions that match the sophistication of modern threats. As businesses rapidly adopt emerging technologies, their exposure to cyberattacks increases. To mitigate these risks, cybersecurity teams need adaptable and comprehensive tools to protect their digital ecosystems effectively. Security Information and Event Management (SIEM) and Extended Detection and Response…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
