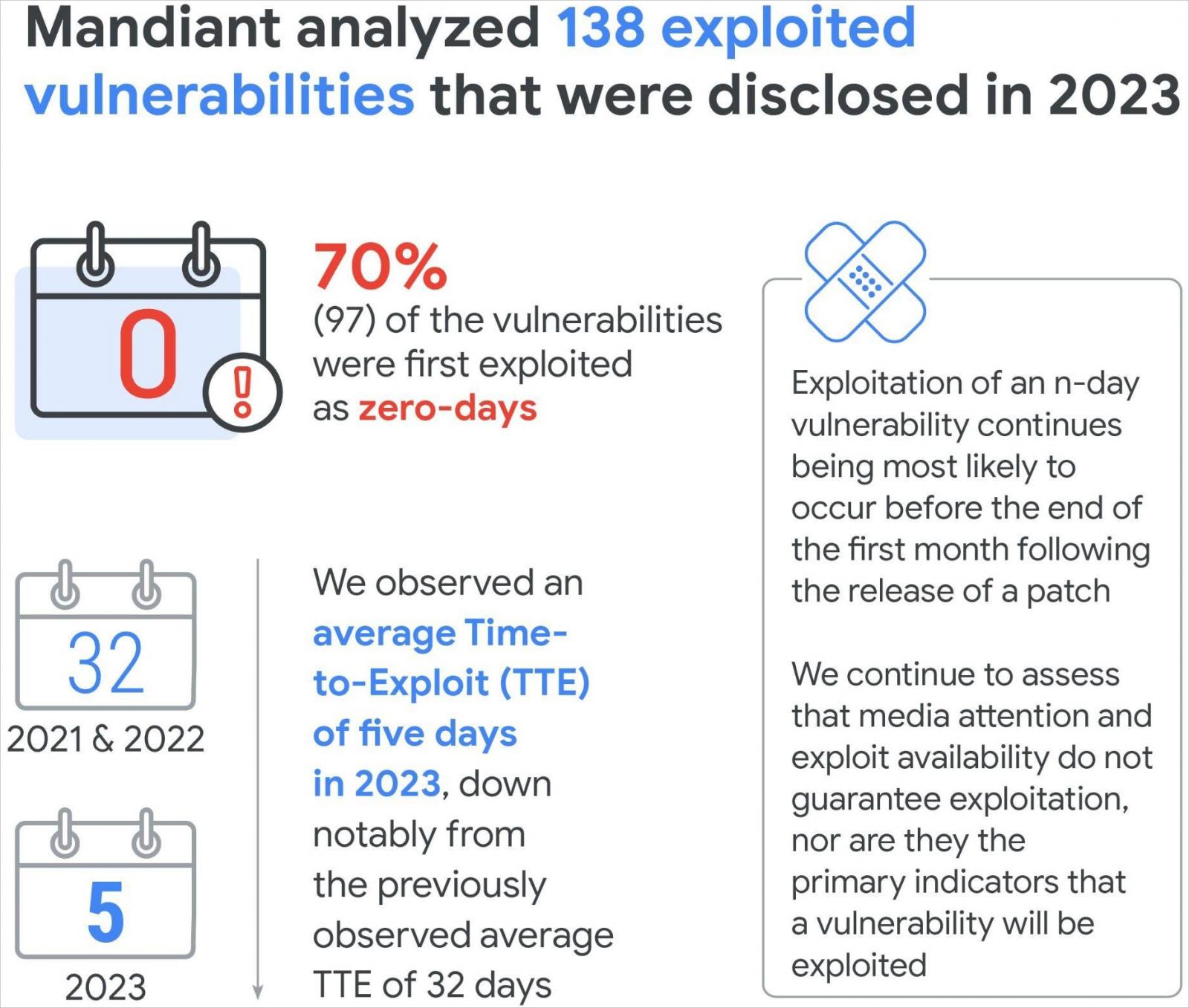
Google: 70% of exploited flaws disclosed in 2023 were zero-days
by nlqip

Mandiant security analysts warn of a worrying new trend of threat actors demonstrating a better capability to discover and exploit zero-day vulnerabilities in software.
Specifically, of the 138 vulnerabilities disclosed as actively exploited in 2023, Mandiant says 97 (70.3%) were leveraged as zero-days.
This means that threat actors exploited the flaws in attacks before the impacted vendors knew of the bugs existence or had been able to patch them.
From 2020 until 2022, the ratio between n-days (fixed flaws) and zero-days (no fix available) remained relatively steady at 4:6, but in 2023, the ratio shifted to 3:7.
Google explains that this is not due to a drop in the number of n-days exploited in the wild but rather an increase in zero-day exploitation and the improved ability of security vendors to detect it.
This increased malicious activity and diversification in targeted products is also reflected in the number of vendors impacted by actively exploited flaws, which has increased in 2023 to a record 56, up from 44 in 2022 and higher than the previous record of 48 vendors in 2021.
Response times getting tighter
Another significant trend was recorded regarding the time taken to exploit (TTE) a newly disclosed (n-day or 0-day) flaw, which has now dropped to just five days.
For comparison, in 2018-2019, TTE was 63 days, and in 2021-2022, TTE was 32 days. This gave system administrators plenty of time to plan the application of patches or implement mitigations to secure impacted systems.
However, with the TTE now falling to 5 days, strategies like network segmentation, real-time detection, and urgent patch prioritization become a lot more critical.
On a related note, Google does not see a correlation between the disclosure of exploits and TTE.
In 2023, 75% of exploits were made public before exploitation in the wild had started, and 25% were released after hackers were already leveraging the flaws.
Two examples highlighted in the report to showcase that there’s no consistent relationship between public exploit availability and malicious activity are CVE-2023-28121 (WordPress plugin) and CVE-2023-27997 (Fortinet FortiOS).
.jpg)
Source: Google
In the first case, exploitation started three months after disclosure and ten days after a proof-of-concept was published.
In the FortiOS case, the flaw was weaponized almost immediately in public exploits, but the first malicious exploitation event was recorded four months later.
Difficulty of exploitation, threat actor motivation, target value, and overall attack complexity all play a role in TTE, and a direct or isolated correlation with PoC availability is flawed according to Google.
Source link
lol
Mandiant security analysts warn of a worrying new trend of threat actors demonstrating a better capability to discover and exploit zero-day vulnerabilities in software. Specifically, of the 138 vulnerabilities disclosed as actively exploited in 2023, Mandiant says 97 (70.3%) were leveraged as zero-days. This means that threat actors exploited the flaws in attacks before the…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
