Undercover North Korean IT workers now steal data, extort employers
by nlqip

North Korean IT professionals who trick Western companies into hiring them are stealing data from the organization’s network and asking for a ransom to not leak it.
Dispatching IT workers to seek employment at companies in wealthier nations is a tactic that North Korea has been using for years as a means to obtain privileged access for cyberattacks or to generate revenue for the country’s weapons programs.
Researchers at cybersecurity company Secureworks uncovered the extortion component during multiple investigations of such fraudulent schemes.
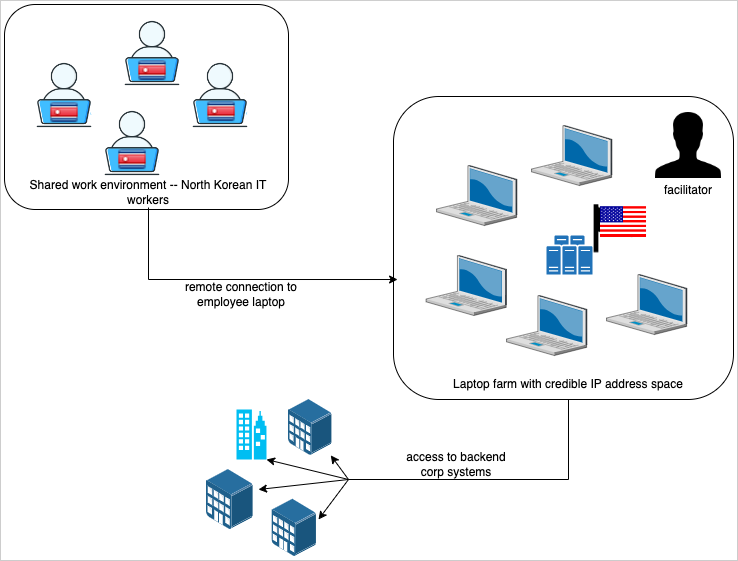
After the employment of a North Korean national with access to proprietary data (as part of their contractor role) terminated, the company would receive the first extortion email, the researchers explain.
To obtain the job and avoid raising suspicions afterwards, the fraudulent IT workers used a false or stolen identity and relied on laptop farms to route traffic between their real location and the company through a U.S.-based point.
They also avoided video during calls or resorted to various tricks while on the job to hide their face during video conferences, such as using artificial intelligence tools.
Source: Secureworks
In July, American cybersecurity company KnowBe4 revealed that they were among the hundreds of victimized companies, and in their case, the threat actor attempted to install an infostealer on the company’s computer.
Secureworks tracks the group organizing and coordinating North Korea’s IT worker army as “Nickel Tapestry,” while Mandiant uses the UNC5267 name.
One example of a Nickel Tapestry campaign in mid-2024 that Secureworks investigated is that of a company that had proprietary data stolen almost immediately after employing an external contractor
The data was transferred to a personal Google Drive cloud storage using the company’s virtual desktop infrastructure (VDI).
After terminating the employment due to poor performance, the company began receiving extortion emails from external Outlook and Gmail addresses containing samples of the stolen data in ZIP archives.
The threat actors demanded a six-figure ransom to be paid in cryptocurrency in exchange to not leaking the data publicly.
Secureworks’ investigation revealed that Nickel Tapestry had used Astrill VPN and residential proxies to mask their real IP address during the malicious activities, while AnyDesk was used for remote accessing the systems.
The researchers warn that North Korean IT workers often coordinate to refer one another to companies.
Organizations should be cautious when hiring remote workers or freelancers, and look for signs of fraud like changes in payment accounts and laptop shipment addresses, submission of generic-looking resumes, atypical correspondence hours, and unwillingness to enable camera during interviews.
Source link
lol
North Korean IT professionals who trick Western companies into hiring them are stealing data from the organization’s network and asking for a ransom to not leak it. Dispatching IT workers to seek employment at companies in wealthier nations is a tactic that North Korea has been using for years as a means to obtain privileged…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
