Severe flaws in E2EE cloud storage platforms used by millions
by nlqip

Several end-to-end encrypted (E2EE) cloud storage platforms are vulnerable to a set of security issues that could expose user data to malicious actors.
Cryptographic analysis from ETH Zurich researchers Jonas Hofmann and Kien Tuong Turong revealed issue with Sync, pCloud, Icedrive, Seafile, and Tresorit services, collectively used by more than 22 million people.
The analysis was based on the threat model of an attacker controlling a malicious server that can read, modify, and inject data at will, which is realistic for nation-state actors and sophisticated hackers.
The team comments that many of the discovered flaws directly oppose the marketing promises of the platforms, which create a deceptive and false premise for customers.
Findings
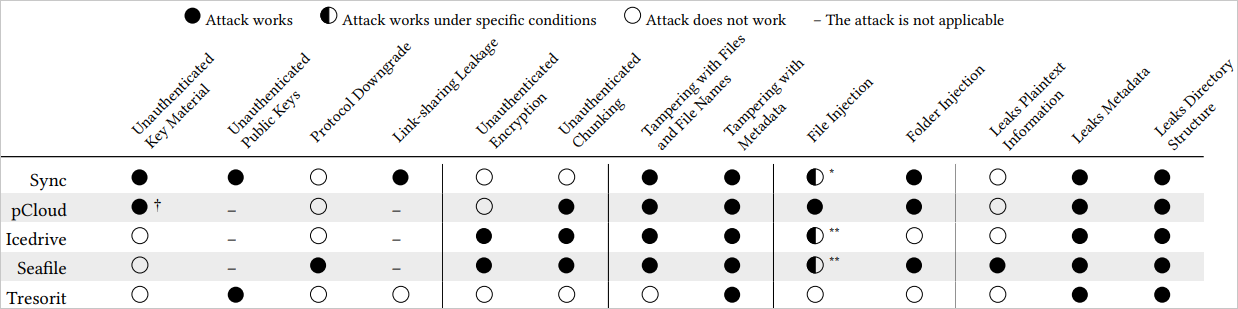
The ETH Zurich researchers found serious vulnerabilities in all five products, including implementations that allow a malicious actor to inject files, tamper with data, or gain access to user files. Here’s an overview of the discovered issues:
- Sync‘s vulnerabilities include unauthenticated key material, allowing attackers to inject their own encryption keys and compromise data. The lack of public key authentication in file sharing further enables attackers to decrypt shared files. Shared links expose passwords to the server, breaking confidentiality. Additionally, attackers can rename or move files undetected and even inject folders into user storage, making them appear as if the user uploaded them.
- pCloud‘s main issues stem from unauthenticated key material, allowing attackers to overwrite private keys and force encryption with attacker-controlled keys. Public keys are also unauthenticated, giving attackers access to encrypted files. Additionally, attackers can inject files, manipulate metadata like file size, and reorder or remove chunks due to the lack of authentication in the chunking process.
- Icedrive‘s use of unauthenticated CBC encryption makes it vulnerable to file tampering, allowing attackers to modify file contents. File names can also be truncated or altered. The chunking process lacks authentication, meaning attackers can reorder or remove file chunks, compromising file integrity.
- Seafile is vulnerable to protocol downgrades, making password brute-forcing easier. Its use of unauthenticated CBC encryption allows file tampering, and unauthenticated chunking lets attackers manipulate file chunks. File names and locations are also unsecured, and the server can inject files or folders into user storage.
- Tresorit‘s public key authentication relies on server-controlled certificates, which attackers can replace to access shared files. Metadata is also vulnerable to tampering, allowing attackers to alter file creation details and mislead users.
Out of the examined group of five, Tresorit fared relatively better, as the issues discovered do not directly expose file contents or allow for easy data manipulation.
Source: ETH Zurich
Disclosure and vendor responses
The researchers notified Sync, pCloud, Seafile, and Icedrive of their findings on April 23, 2024, and contacted Tresorit on September 27, 2024, to discuss potential improvements in their particular cryptographic designs.
Icedrive decided not to address the issues, Seafile promised to patch the protocol downgrade problem on a future upgrade, while Sync and pCloud had not responded as of October 10, 2024.
BleepingComputer contacted all five cloud service providers for a comment on Hofmann’s and Truong’s research, and we received the below statements.
Sync: Our security team became aware of these issues last week, and we’ve since taken swift action to address them. We’ve also reached out to the research team to share findings and collaborate on next steps.
The potential data leak issue on links (as reported) has already been fixed, and we are fast-tracking fixes for the remaining potential issues right now. As the research paper outlines, these vulnerabilities exist under the pretext of a compromised server. There is no evidence that these vulnerabilities have been exploited or that file data has been accessed.
We understand that by using Sync, trust is placed in us. But the promise of end-to-end encryption is that you don’t need to trust anyone, not even us. This concept is at the core of our encryption model and central to what we do.
We’re committed to getting these issues resolved.
Tresorit: The study of ETH Zürich’s world-class research team examined the possibility of ten classes of attacks on end-to-end-encrypted cloud storage systems, including confidentiality breaches and file injection vulnerabilities. The findings confirmed that Tresorit’s thoughtful design and cryptographic choices made our system largely unaffected by these attacks. While we are pleased with these results, we also recognize the untapped potential the research highlighted.
Presenting public key fingerprints to users when sharing folders is on our 2025 roadmap. This will completely prevent key replacement attacks by allowing out-of-band verification. We already do this for business invitations so the user can get cryptographic evidence about their future data administrator before joining. Our Common Criteria EAL4 + AVA_VAN.5 evaluated client software — a first among cloud storage services — requires out-of-band key authentication for folder sharing, too.
Even though some metadata, such as the file size, the time of last modification, and folder memberships are shared with the servers, these are also stored as cryptographically authenticated data to prevent tampering. This metadata is also needed to be known on the server side: for the proper bookkeeping of our customers’ storage quota, and to enforce server-side access rules as an additional layer of security.
At Tresorit, security is our top priority, and we are committed to continuous improvement, using these insights to strengthen our platform further. This research not only helps us evolve but also guides the broader industry toward more secure solutions. Security is the foundation of everything we build, and we are proud to collaborate with academic institutions like the Technical University in Budapest to ensure that we stay at the forefront of innovation in secure cloud storage.
Seafile: We don’t have anything to comment at the moment.
Icedrive and pCloud did not respond to BleepingComputer’s request for a statement.
Source link
lol
Several end-to-end encrypted (E2EE) cloud storage platforms are vulnerable to a set of security issues that could expose user data to malicious actors. Cryptographic analysis from ETH Zurich researchers Jonas Hofmann and Kien Tuong Turong revealed issue with Sync, pCloud, Icedrive, Seafile, and Tresorit services, collectively used by more than 22 million people. The analysis…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
