Bumblebee malware returns after recent law enforcement disruption
by nlqip

The Bumblebee malware loader has been spotted in new attacks recently, more than four months after Europol disrupted it during ‘Operation Endgame’ in May.
Believed to be the creation of TrickBot developers, the malware emerged in 2022 as a replacement for the BazarLoader backdoor to provide ransomware threat actors access to victim networks.
Bumblebee typically achieves infection via phishing, malvertising, and SEO poisoning that promoted various software (e.g. Zooom, Cisco AnyConnect, ChatGPT, and Citrix Workspace).
Among the payloads typically delivered by Bumblebee are Cobalt Strike beacons, information-stealing malware, and various ransomware strains.
In May, an international law enforcement operation codenamed ‘Operation Endgame’ seized over a hundred servers supporting the multiple malware loader operations, including IcedID, Pikabot, Trickbot, Bumblebee, Smokeloader, and SystemBC.
Ever since, Bumblebee went silent. However, researchers at cybersecurity company Netskope observed new Bumblebee activity tied to the malware, which could indicate a resurgence.
Latest Bumblebee attack chain
The most recent Bumblebee attack chain starts with a phishing email that lures the victim to download a malicious ZIP archive.
The compressed file contains a .LNK shortcut named Report-41952.lnk, which triggers PowerShell to download a malicious .MSI file (y.msi) disguised as a legitimate NVIDIA driver update or Midjourney installer from a remote server.
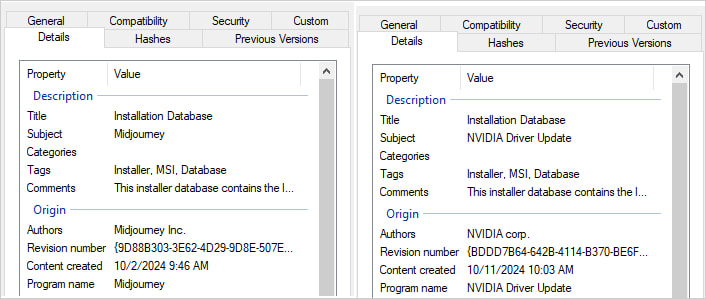
Source: Netskope
The MSI file is then executed silently using msiexec.exe with the /qn option, which ensures that the process runs without any user interaction.
To avoid spawning new processes, which is noisier, the malware uses the SelfReg table within the MSI structure, which instructs msiexec.exe to load the DLL into its own address space and to invoke its DllRegisterServer function.
Once the DLL is loaded and executed, the malware’s unpacking process begins, leading to the deployment of Bumblebee in memory.
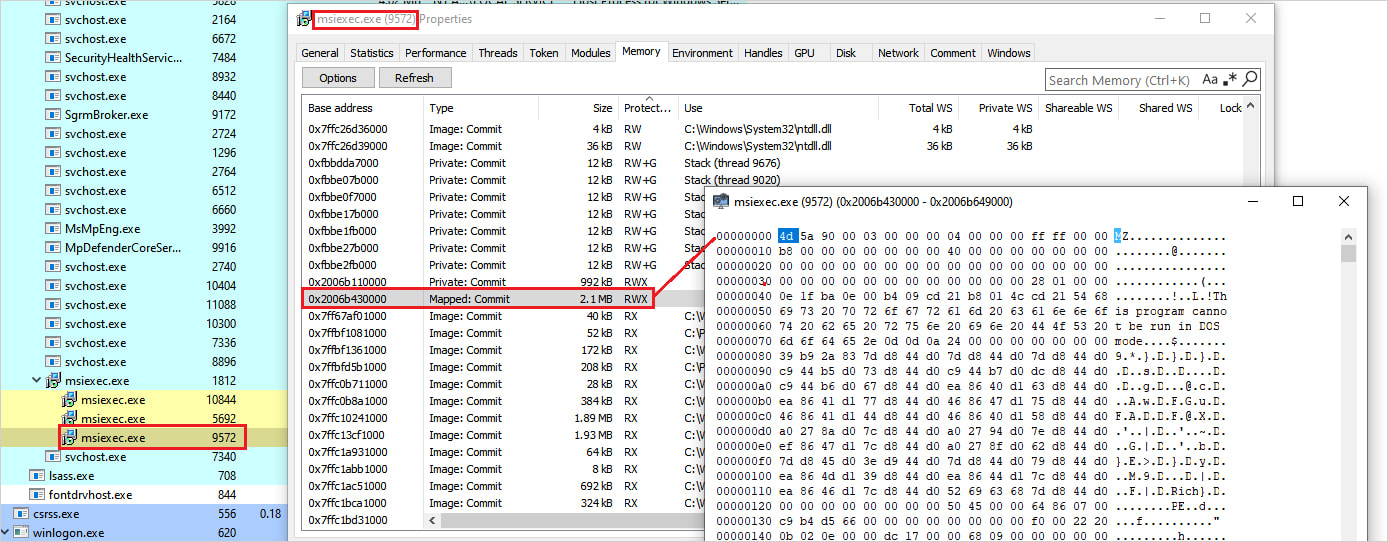
Source: Netskope
Netskope comments that the Bumblebee payload carries its signature internal DLL and exported functions naming scheme, as well as configuration extraction mechanisms seen in past variants.
The RC4 key that decrypts its configuration in the most recent attacks uses the “NEW_BLACK” string, while there are two campaign IDs, namely “msi” and “lnk001.”
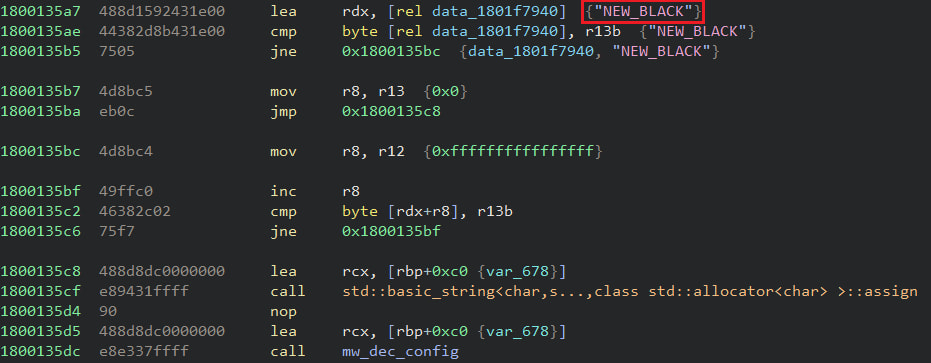
Source: Netskope
Netskope didn’t provide any info on the payloads that Bumblebee dropped or the scale of the campaign but the report serves as a warning of early signs of a possible resurgence.
The complete lists of the indicators of compromise is available on this GitHub repository.
Source link
lol
The Bumblebee malware loader has been spotted in new attacks recently, more than four months after Europol disrupted it during ‘Operation Endgame’ in May. Believed to be the creation of TrickBot developers, the malware emerged in 2022 as a replacement for the BazarLoader backdoor to provide ransomware threat actors access to victim networks. Bumblebee typically achieves…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
