Hackers exploit 52 zero-days on the first day of Pwn2Own Ireland
by nlqip

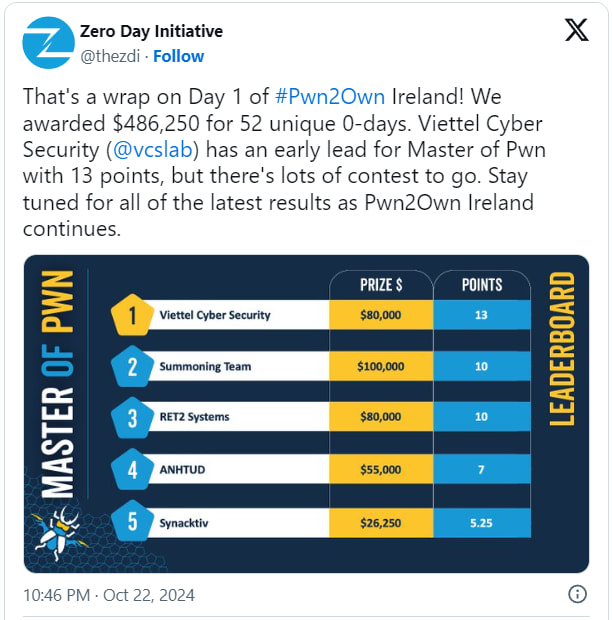
On the first day of Pwn2Own Ireland, participants demonstrated 52 zero-day vulnerabilities across a range of devices, earning a total of $486,250 in cash prizes.
Viettel Cyber Security took an early lead getting 13 points in their chase for the “Master of Pwn” title. The team’s phudq and namnp exploited a Lorex 2K WiFi camera through a stack-based buffer overflow vulnerability and got $30,000 and 3 points.
Sina Kheirkhah from Summoning Team stole the show with a chain of nine vulnerabilities to go from QNAP QHora-322 router to TrueNAS Mini X device, which brought a $100,000 payout and 10 Master of Pwn points.
RET2 Systems’ Jack Dates followed with a successful out-of-bounds (OOB) write exploit on the Sonos Era 300 smart speaker, securing $60,000 and 6 points. His exploit allowed full control over the device.
A second Viettel Cyber Security attempt combined four new bugs to pivot from the QNAP QHora-322 router to the TrueNAS Mini X, earning them another $50,000 and 10 points.
Other notable attempts from Pwn2Own day one include:
- Team Neodyme leveraged a stack-based buffer overflow to target the HP Color LaserJet Pro MFP 3301fdw printer. Their success was rewarded with $20,000 and 2 points.
- PHP Hooligans / Midnight Blue earned $20,000 for exploiting a Canon imageCLASS MF656Cdw printer using a single bug.
- ExLuck of ANHTUD joined the leaderboard with four new bugs, including improper certificate verification and a hardcoded cryptographic key, to exploit the QNAP TS-464 NAS device. This effort earned $40,000 and 4 Master of Pwn points.
- On the surveillance front, Rapid7’s Ryan Emmons and Stephen Fewer successfully exploited the Synology DiskStation DS1823xs+ via an improper neutralization of argument delimiters bug, earning $40,000 and 4 points.
The first day wasn’t without challenges and partial failures though. Summoning Team struggled to execute their QNAP TS-464 and Synology BeeStation BST150-4T exploits in time, while Synacktiv experienced a bug collision in their Lorex 2K camera exploit, earning a reduced payout of $11,250.
Despite a few setbacks, the first day of Pwn2Own Ireland 2024 was packed with high-stakes hacks and matching rewards.
There are three more days left in the competition and participants will try to exploit security issues found in fully patched SOHO devices, including printers, NAS systems, WiFi cameras, routers, smart speakers, mobile phones (Samsung Galaxy S24), for a portion of the $1 million pool prize.
Source link
lol
On the first day of Pwn2Own Ireland, participants demonstrated 52 zero-day vulnerabilities across a range of devices, earning a total of $486,250 in cash prizes. Viettel Cyber Security took an early lead getting 13 points in their chase for the “Master of Pwn” title. The team’s phudq and namnp exploited a Lorex 2K WiFi camera through a stack-based…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA