Microsoft Entra “security defaults” to make MFA setup mandatory
by nlqip

Microsoft says it will improve security across Entra tenants where security defaults are enabled by making multifactor authentication (MFA) registration mandatory.
This move is part of the company’s Secure Future Initiative, launched in November 2023, to boost cybersecurity protection across its products.
“We’re removing the option to skip multifactor authentication (MFA) registration for 14 days when security defaults are enabled. This means all users will be required to register for MFA on their first login after security defaults are turned on,” said Microsoft’s Nitika Gupta on Wednesday.
“This will help reduce the risk of account compromise during the 14-day window, as MFA can block over 99.2% of identity-based attacks.”
This change will affect all newly created tenants starting on December 2nd, 2024, and will begin rolling out to existing tenants starting in January 2025.
Microsoft Entra security defaults is a setting that automatically enables various security features to protect organizations from common attacks, such as password sprays, replay, and phishing.
Since October 22, 2019, new tenants have automatically had security defaults enabled, and older tenants have had it automatically enabled over time if they are not using conditional access, have premium licenses, or are using legacy authentication clients.
To enable security defaults, you must sign in to the Microsoft Entra admin center (at least as a Security Administrator), browse to Identity > Overview > Properties, and select Manage security defaults. From there, set “Security defaults” to Enabled and click Save.
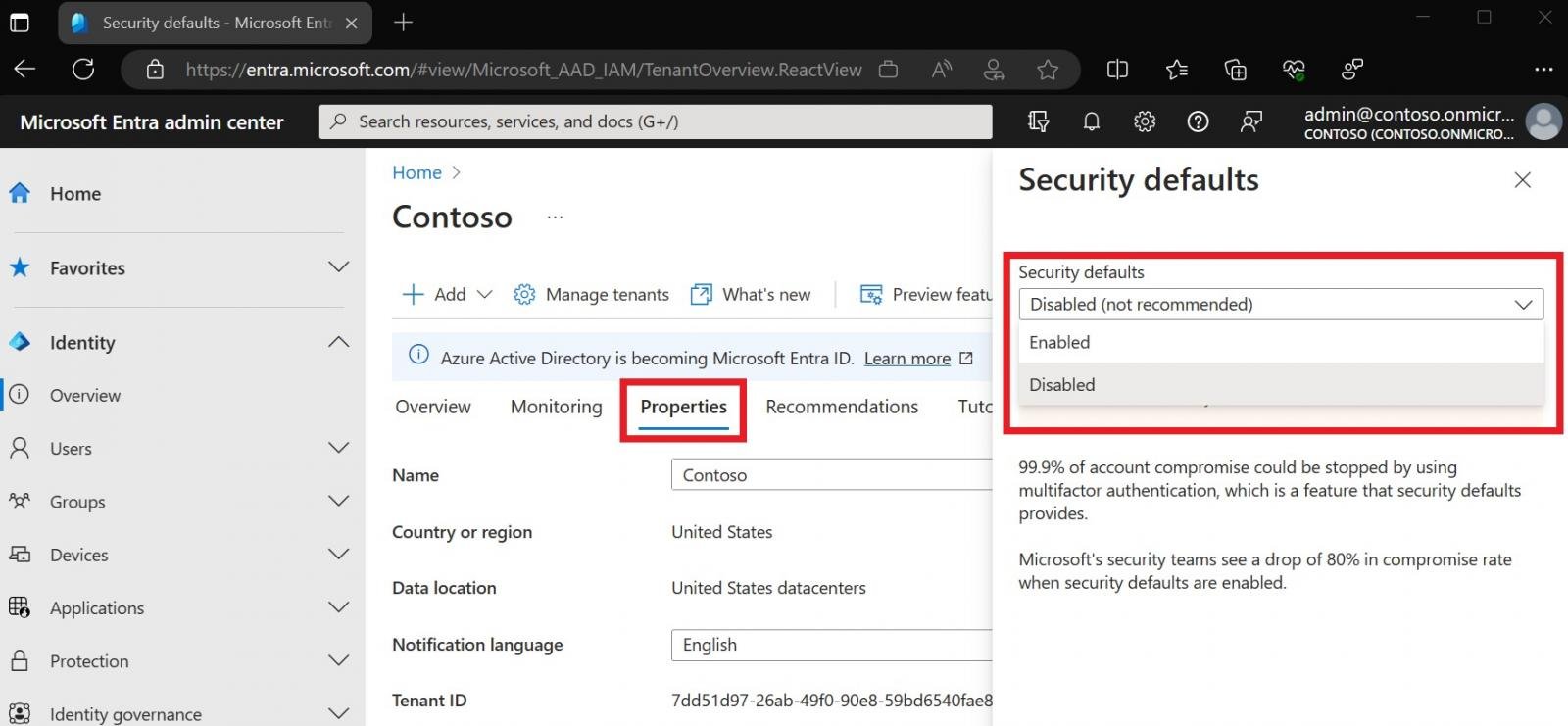
Admins not using Conditional Access are advised to enable security defaults for their organization because they provide a simple and effective way to protect users and resources from common threats.
However, even though security defaults offer a good security posture baseline, they don’t allow for the customization provided by Conditional Access policies that complex organizations require.
In August, Microsoft also warned Entra global admins to enable MFA for their tenants until October 15th to ensure users don’t lose access to admin portals. By enforcing mandatory MFA for all Azure sign-in attempts, Microsoft aims to protect Azure accounts against hijacking and phishing attempts.
The company also announced in November that it would roll out Conditional Access policies requiring MFA for all admins signing into Microsoft admin portals (e.g., Entra, Microsoft 365, Exchange, and Azure), for users on all cloud apps, and high-risk sign-ins.
In January, Microsoft-owned GitHub also began enforcing two-factor authentication (2FA) for all active developers as part of the company’s ongoing effort to boost MFA adoption.
Source link
lol
Microsoft says it will improve security across Entra tenants where security defaults are enabled by making multifactor authentication (MFA) registration mandatory. This move is part of the company’s Secure Future Initiative, launched in November 2023, to boost cybersecurity protection across its products. “We’re removing the option to skip multifactor authentication (MFA) registration for 14 days…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
