QNAP patches second zero-day exploited at Pwn2Own to get root
by nlqip

QNAP has released security patches for a second zero-day bug exploited by security researchers during last week’s Pwn2Own hacking contest.
This critical SQL injection (SQLi) vulnerability, tracked as CVE-2024-50387, was found in QNAP’s SMB Service and is now fixed in versions 4.15.002 or later and h4.15.002 and later.
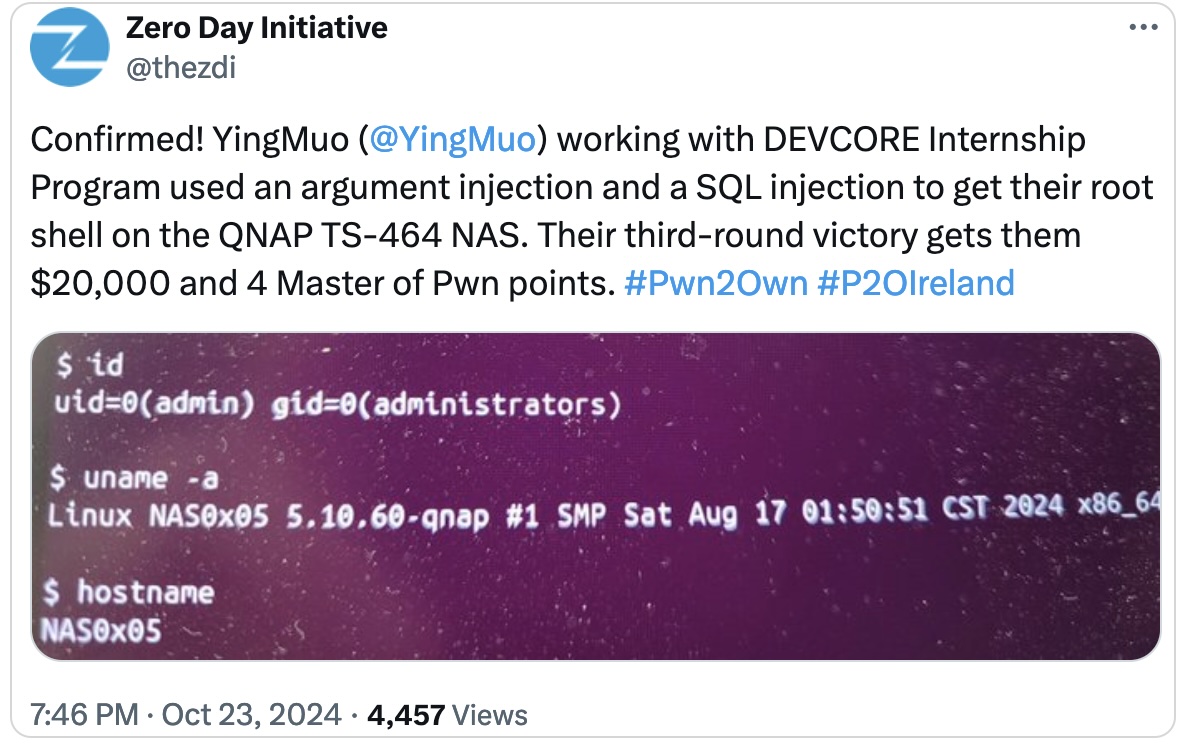
The zero-day flaw was patched one week after allowing YingMuo (working with the DEVCORE Internship Program) to get a root shell and take over a QNAP TS-464 NAS device at Pwn2Own Ireland 2024.
On Tuesday, the company fixed another zero-day in its HBS 3 Hybrid Backup Sync disaster recovery and data backup solution, exploited by Viettel Cyber Security’s team at Pwn2Own to execute arbitrary commands and hack a TS-464 NAS device.
Team Viettel won Pwn2Own Ireland 2024 after four days of competition, during which more than $1 million in prizes were awarded to hackers who demonstrated over 70 unique zero-day vulnerabilities.
While QNAP patched both vulnerabilities within a week, vendors usually take their time to release security patches after the Pwn2Own contest, given that they have 90 days until Trend Micro’s Zero Day Initiative releases details on bugs disclosed during the contest.
To update the software on your NAS device, log in to QuTS hero or QTS as an administrator, go to the App Center, search for “SMB Service,” and click “Update.” This button will not be available if the software is already up-to-date.
Patching quickly is highly recommended, as QNAP devices are popular targets for cybercriminals because they’re commonly used for backing up and storing sensitive personal files. This makes them easy targets for installing information-stealing malware and the perfect leverage for forcing victims to pay a ransom to get back their data.
For instance, in June 2020, QNAP warned of eCh0raix ransomware attacks, which exploited Photo Station app vulnerabilities to hack into and encrypt QNAP NAS devices.
QNAP also alerted customers in September 2020 of AgeLocker ransomware attacks targeting publicly exposed NAS devices running older and vulnerable Photo Station versions. In June 2021, eCh0raix (QNAPCrypt) returned with new attacks exploiting known vulnerabilities and brute-forcing NAS accounts using weak passwords.
Other recent attacks targeting QNAP devices include DeadBolt, Checkmate, and eCh0raix ransomware campaigns, which abused various security vulnerabilities to encrypt data on Internet-exposed NAS devices.
Source link
lol
QNAP has released security patches for a second zero-day bug exploited by security researchers during last week’s Pwn2Own hacking contest. This critical SQL injection (SQLi) vulnerability, tracked as CVE-2024-50387, was found in QNAP’s SMB Service and is now fixed in versions 4.15.002 or later and h4.15.002 and later. The zero-day flaw was patched one week…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA