LottieFiles hit in npm supply chain attack targeting users’ crypto
by nlqip

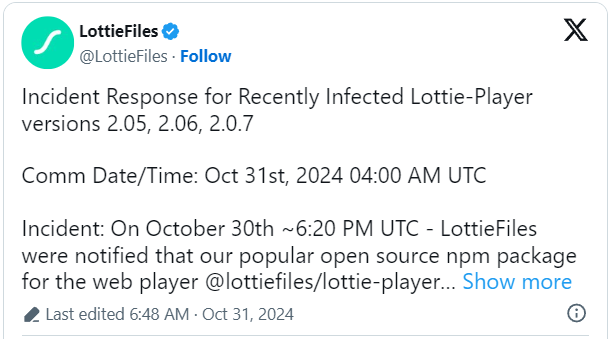
LottieFiles announced that specific versions of its npm package carry malicious code that prompts users to connect their cryptocurrency wallets so they can be emptied.
As discovered yesterday, following multiple user reports about strange code injections, the affected versions are Lottie Web Player (“lottie-player”) 2.0.5, 2.0.6, and 2.0.7, all published yesterday.
LottieFiles quickly released a new version, 2.0.8, which is based on the clean 2.0.4, advising users to upgrade to it as soon as possible.
“A large number of users using the library via third-party CDNs without a pinned version were automatically served the compromised version as the latest release,” explains LottieFiles.
“With the publishing of the safe version, those users would have automatically received the fix.”
Those unable to upgrade to the latest release should communicate the risk to Lottie-player end users and warn them about fraudulent cryptocurrency wallet connection requests. Staying on version 2.0.4 is also an option.
LottieFiles is a software-as-a-service (SaaS) platform for creating and sharing lightweight vector-based (scalable) animations that can be embedded in apps and websites.
It’s popular for allowing high-quality visuals at a minimal performance impact on less powerful devices, mobile, and web apps.
Earlier today, LottieFiles released an announcement about the supply chain compromise, noting that it only impacts the npm package and not its SaaS services.
Apparently, apps and sites incorporating a malicious version of the Lottie Web Player served users wallet connection prompts, which then enables threat actors to transfer digital assets to wallets under their control.
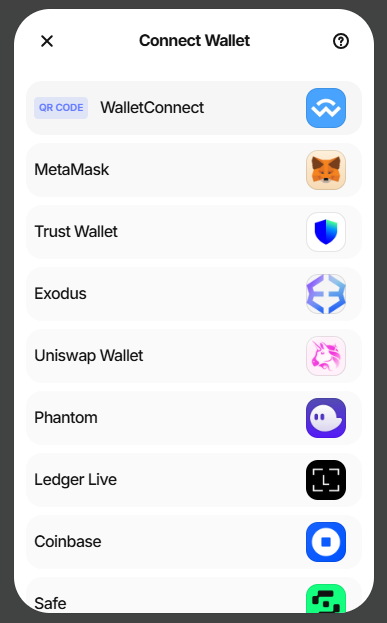
Source: GitHub
The developer account that was used for uploading the tampered versions of the npm package has been stripped of all access, and associated tokens were revoked to block the malicious activity.
“We have confirmed that our other open source libraries, open source code, Github repositories, and our SaaS were not affected,” assures LottieFiles.
The platform continues its internal investigation of the compromise with the help of external experts, and more details about the incident might be made available in the future.
It is unknown if there have been any victims of this scheme, how many, and how much money was lost from the fraudulent cryptocurrency wallet connections.
Source link
lol
LottieFiles announced that specific versions of its npm package carry malicious code that prompts users to connect their cryptocurrency wallets so they can be emptied. As discovered yesterday, following multiple user reports about strange code injections, the affected versions are Lottie Web Player (“lottie-player”) 2.0.5, 2.0.6, and 2.0.7, all published yesterday. LottieFiles quickly released a…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
