Solving the painful password problem with better policies
by nlqip

The password problem — weak, reused credentials that are easy to compromise yet hard to remember and manage — plagues users and organizations. But despite technological advances, passwords still guard 88% of the world’s online services.
So how can IT leaders overcome this challenge?
In this post, we explore why passwords are so easy to hack and discuss things you can do to fortify your organization’s security efforts.
Why passwords are so easy to hack — and how hackers do it
When it comes to hacking passwords, it’s a relatively easy process. Why? It comes down to human predictability.
Consider this: most users choose from a limited set of 94 characters on a standard US keyboard — which includes lowercase and uppercase letters, symbols, and numbers. And while ostensibly, this should lead to six quadrillion potential combinations of 8-character passwords, the reality is that user-created passwords are rarely this complex.
The truth is humans are creatures of habit. And with a full 55% of users relying solely on their memory to keep track of passwords, it’s easy to see why it’s so tempting to reuse passwords.
And that’s where the bad guys come in. Understanding the human tendency to reuse passwords, many focus their energies on obtaining user credentials. They know that if they can compromise one site and get a username and password, there’s a good chance they can use that same username and password at other sites — including corporate websites as well as online banks, online retailers, and social media sites.
Crafting a secure, risk-focused password security policy
There are a number of tools available to help you determine the effectiveness of your password security policy, including:
Specialized spreadsheets: Some organizations use specialized spreadsheets to analyze the effectiveness of their password policies. These kinds of spreadsheets allow you to input specific parameters like minimum password length, complexity requirements, and even expiration periods. Then, the spreadsheet formula calculates how many guesses an attacker could make before being forced to change a password, effectively quantifying a password policy’s strength.
Online password strength checkers: Another option for testing your password policy’s strength is to take advantage of one of the many online password strength testers. Like specialized spreadsheets, these tools review passwords to determine how easy or difficult they would be for hackers to crack. You should remember, however, to never input your real passwords into these tools. Instead, use similar but not identical passwords for testing purposes.
Password auditors: A password auditor like Specops Password Auditor can help you identify and resolve any potential password-related vulnerabilities.
A free, read-only tool, Specops Password Auditor quickly scans your Active Directory, checking for weak or compromised passwords. It can also identify stale or inactive privileged administrator accounts, helping further enhance your security.
Passwords still matter
Despite the ever-present talk of a “passwordless society,” passwords aren’t going anywhere anytime soon—they’re the primary authentication method for 88% of the world’s websites and services.
To enhance your organization’s security, consider implementing a password security management solution like Specops Password Policy to help you strengthen passwords and enforce stringent password policies.
With Specops Password Policy, you can create custom password rules, ensure compliance with industry regulations are met, enforce passphrases, and create custom dictionaries.
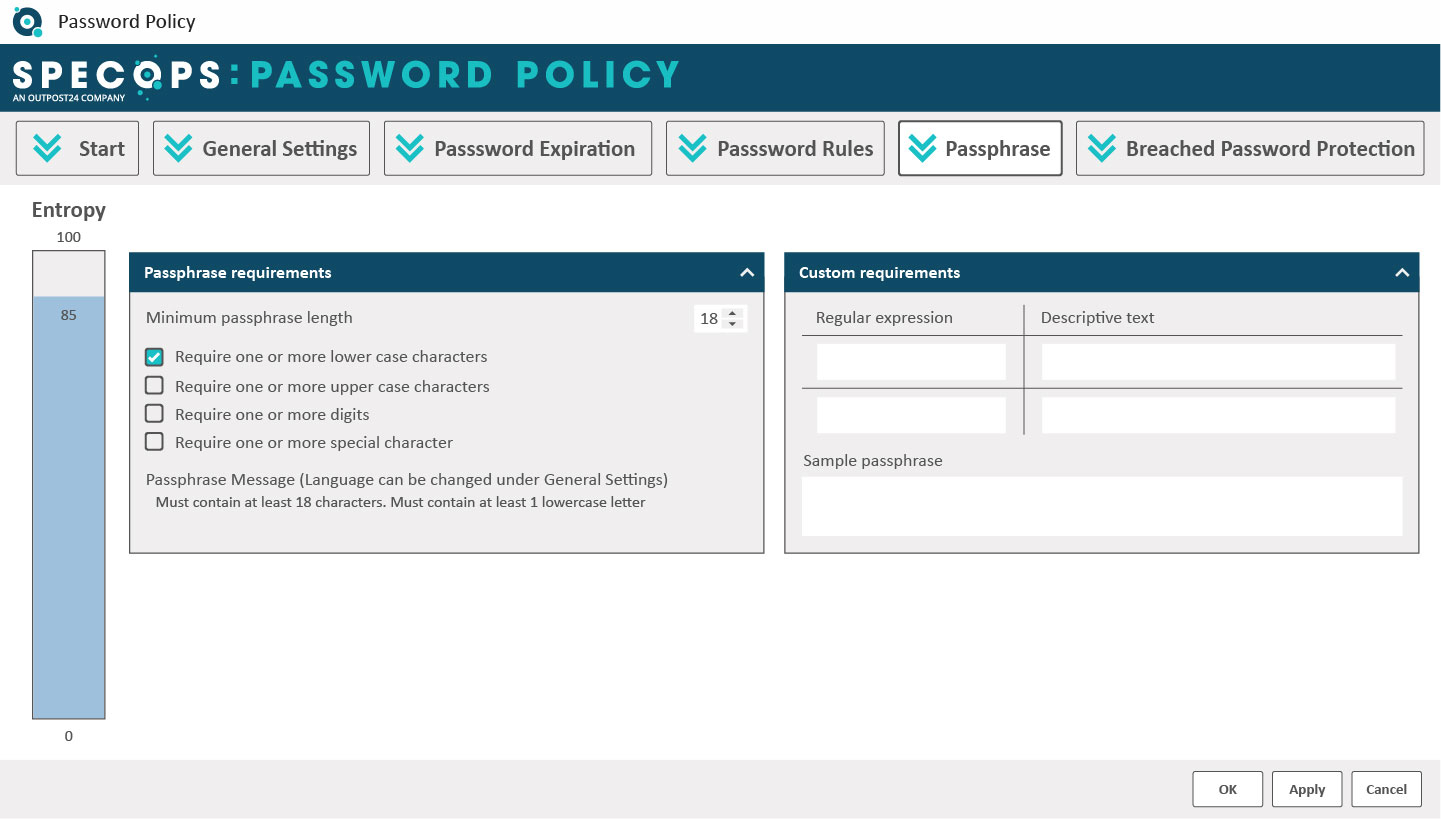
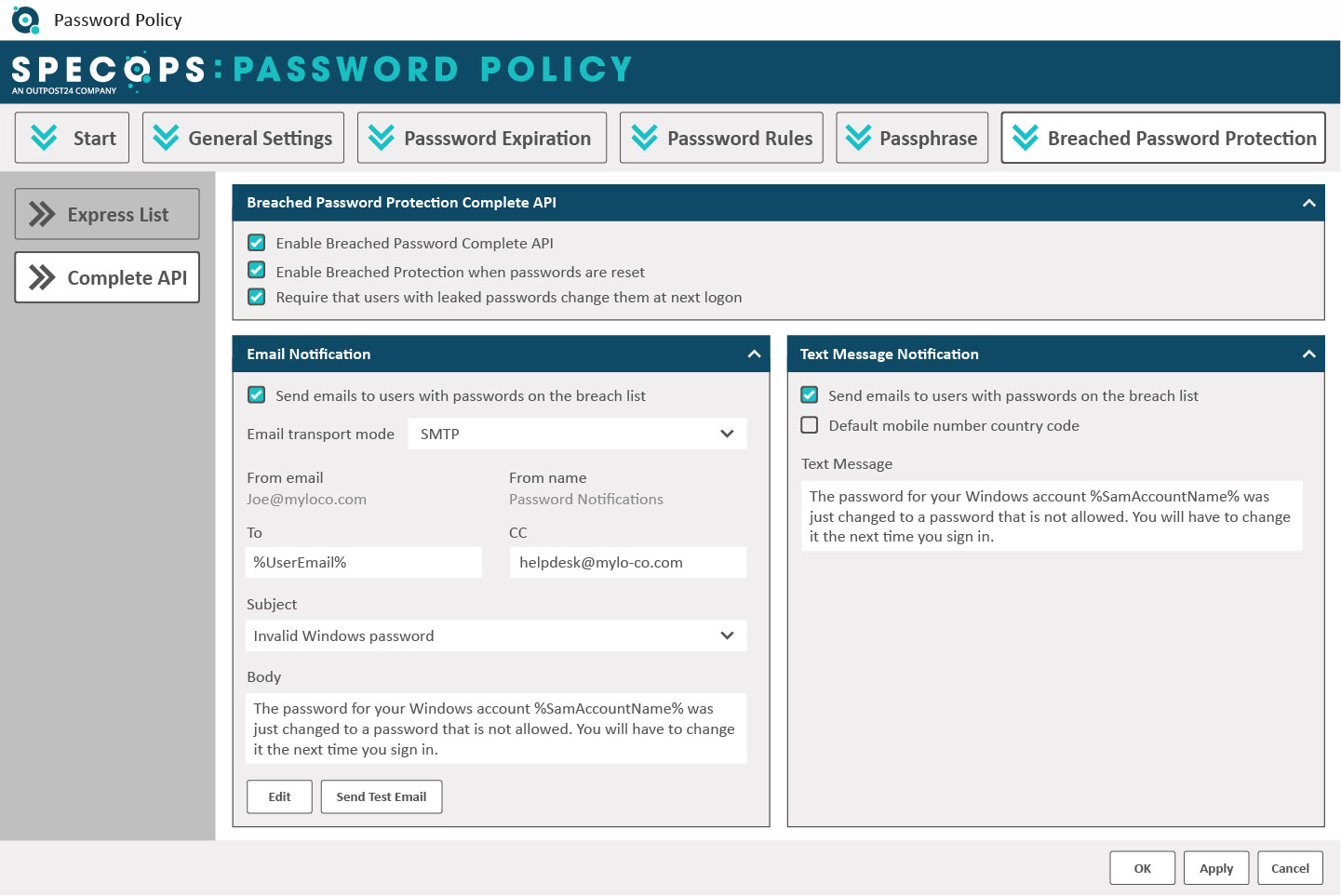
On top of that you can clock the use of breached passwords by continuously scanning your Active Directory against our database of over 4 billion compromised passwords. This occurs 24/7 and not just at password change.
How MFA and password managers impact your risk
Implementing multi-factor authentication adds a layer of security to your password policy, helping to block the progress of hackers who have obtained end-user credentials. And while, like every other security technology it isn’t infallible, it does make a huge impact; Microsoft identified that 99% of compromised enterprise accounts lacked MFA.
Password managers can help further minimize your exposure. Because they can generate and store a nearly endless combination of user credentials, you’re effectively boosting your users’ (and your organization’s) security.
Tools like this also prevent users from using compromised passwords, further enhancing security.
Empowering your end-users to become your best front line of defense
While robust password policies and technical solutions are important to your security strategy, you should consider your users as your best and front line of defense. By educating and empowering your employees, they can help actively defend your organization’s cybersecurity.
Implement strategies like:
- Hosting regular security awareness training: Cover things like password best practices, spotting and avoiding phishing and social engineering attacks.
- Encouraging the use of password managers: Educate users about how password managers work and their benefits.
- Promote a security-conscious culture: Recognize and reward employees who identify and report potential security threats.
- Conduct simulated phishing exercises: Regularly test employee awareness by sending faux phishing emails, providing immediate feedback and training for any staffers who fall victim.
Ready to strengthen your password security today? Try Specops Password policy now.
Sponsored and written by Specops Software.
Source link
lol
The password problem — weak, reused credentials that are easy to compromise yet hard to remember and manage — plagues users and organizations. But despite technological advances, passwords still guard 88% of the world’s online services. So how can IT leaders overcome this challenge? In this post, we explore why passwords are so easy to…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
