D-Link won’t fix critical bug in 60,000 exposed EoL modems
by nlqip

Tens of thousands of exposed D-Link routers that have reached their end-of-life are vulnerable to a critical security issue that allows an unauthenticated remote attacker to change any user’s password and take complete control of the device.
The vulnerability was discovered in the D-Link DSL6740C modem by security researcher Chaio-Lin Yu (Steven Meow), who reported it to Taiwan’s computer and response center (TWCERTCC).
It is worth noting that the device was not available in the U.S. and reached end-of-service (EoS) phase at the beginning of the year.
In an advisory today, D-Link announced that it won’t fix the issue and recommends “retiring and replacing D-Link devices that have reached EOL/EOS.”
Chaio-Lin Yu reported to TWCERTCC two other vulnerabilities, an OS command injection and a path traversal issue:
The three flaws issues are summarized as follows:
- CVE-2024-11068: Flaw that allows unauthenticated attackers to modify any user’s password through privileged API access, granting them access to the modem’s Web, SSH, and Telnet services. (CVSS v3 score: 9.8 “critical”).
- CVE-2024-11067: Path traversal vulnerability allowing unauthenticated attackers to read arbitrary system files, retrieve the device’s MAC address, and attempt login using the default credentials. (CVSS v3 score: 7.5 “high”)
- CVE-2024-11066: Bug enabling attackers with admin privileges to execute arbitrary commands on the host operating system through a specific web page. (CVSS v3 score: 7.2 “high”)
A quick search on the FOFA search engine for publicly exposed devices and software shows that there are close to 60,000 D-Link DSL6740C modems reachable over the internet, most of them in Taiwan.
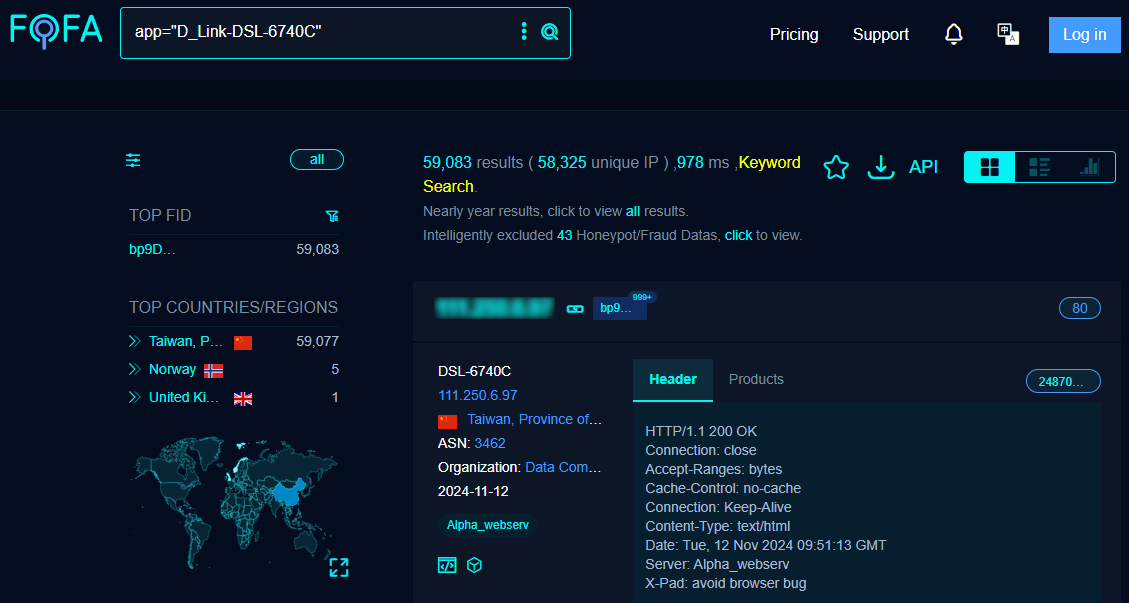
Source: BleepingComputer
TWCERTCC has published advisories for four more high-severity OS command injection vulnerabilities that impact the same D-Link device. The bugs are tracked as CVE-2024-11062, CVE-2024-11063, CVE-2024-11064, and CVE-2024-11065.
Although the number of vulnerable devices exposed on the public web is significant, D-Link has made it clear in the past [1, 2] that end-of-life (EoL) devices are not covered by updates, even when critical bugs are concerned.
If users can’t replace the affected device with a variant that the vendor still supports, they should at least restrict remote access and set secure access passwords.
Source link
lol
Tens of thousands of exposed D-Link routers that have reached their end-of-life are vulnerable to a critical security issue that allows an unauthenticated remote attacker to change any user’s password and take complete control of the device. The vulnerability was discovered in the D-Link DSL6740C modem by security researcher Chaio-Lin Yu (Steven Meow), who reported it to Taiwan’s…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
