North Korean hackers create Flutter apps to bypass macOS security
by nlqip

North Korean threat actors target Apple macOS systems using trojanized Notepad apps and minesweeper games created with Flutter, which are signed and notarized by a legitimate Apple developer ID.
This means that the malicious apps, even if temporarily, passed Apple’s security checks, so macOS systems treat them as verified and allow them to execute without restrictions.
The app names are centered around cryptocurrency themes, which aligns with North Korean hackers’ interests in financial theft.
According to Jamf Threat Labs, which discovered the activity, the campaign appears more like an experiment on how to bypass macOS security rather than a fully-fledged and highly targeted operation.
Notarized apps connecting to DPRK servers
Starting in November 2024, Jamf discovered multiple apps on VirusTotal that appeared completely innocuous to all AV scans yet showcased “stage one” functionality, connecting to servers associated with North Korean actors.
All apps were built for macOS using Google’s Flutter framework, which enables developers to create natively compiled apps for different operating systems using a single codebase written in the Dart programming language.
“It is not unheard of for actors to embed malware within a Flutter based application, however, this is the first we’ve seen of this attacker using it to go after macOS devices,” explains Jamf researchers Ferdous Saljooki and Jaron Bradley.
This approach not only gives the malware authors versatility but also makes malicious code harder to detect because it’s embedded within a dynamic library (dylib), which is loaded by the Flutter engine at runtime.
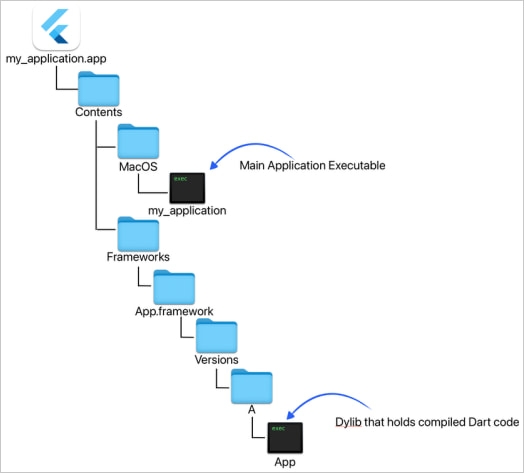
Source: Jamf
Upon further analysis of one of the Flutter-based apps, named ‘New Updates in Crypto Exchange (2024-08-28).app’, Jamf discovered that the obfuscated code in dylib supported AppleScript execution, enabling it to execute scripts sent from a command and control (C2) server.
The app opens a Minesweeper game for macOS, the code of which is freely available on GitHub.
Five of the six malicious applications Jamf discovered were signed using a legitimate developer ID, and the malware had passed notarization, meaning the apps were scanned by Apple’s automated systems and deemed safe.
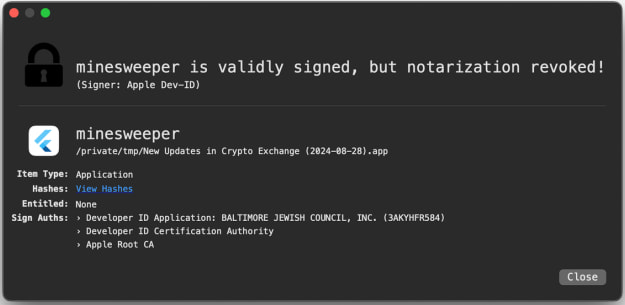
Source: Jamf
Jamf also discovered Golang and Python-based variants, named ‘New Era for Stablecoins and DeFi, CeFi (Protected).app’ and ‘Runner.app,’ with the latter presented as a simple Notepad app.
Both made network requests to a known DPRK-linked domain, ‘mbupdate.linkpc[.]net,’ and featured script execution capabilities.
Apple has since revoked the signatures of the apps Jamf discovered, so they won’t bypass Gatekeeper defenses if they’re loaded on an up-to-date macOS system.
However, it is unclear if those apps were ever used in actual operations or only in “in-the-wild” testing to evaluate techniques to bypass security software.
The fact that there are multiple variants of the same underlying apps supports this theory, but for now, the specifics of this operation remain unknown.
Source link
lol
North Korean threat actors target Apple macOS systems using trojanized Notepad apps and minesweeper games created with Flutter, which are signed and notarized by a legitimate Apple developer ID. This means that the malicious apps, even if temporarily, passed Apple’s security checks, so macOS systems treat them as verified and allow them to execute without…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
