Volt Typhoon rebuilds malware botnet following FBI disruption
by nlqip
The Chinese state-sponsored hacking group Volt Typhoon has begun to rebuild its “KV-Botnet” malware botnet after it was disrupted by law enforcement in January, according to researchers from SecurityScorecard.
Volt Typhoon is a Chinese state-sponsored cyberespionage threat group that is believed to have infiltrated critical U.S. infrastructure, among other networks worldwide, since at least five years ago.
Their primary strategy involves hacking SOHO routers and networking devices, such as Netgear ProSAFE firewalls, Cisco RV320s, DrayTek Vigor routers, and Axis IP cameras, to install custom malware that establishes covert communication and proxy channels and maintain persistent access to targeted networks.
In January 2024, the U.S. authorities announced the disruption of Volt Typhoon’s botnet, which involved wiping malware from infected routers.
Although Volt Typhoon’s initial revival attempt in February failed, reports of the threat actors exploiting a zero-day vulnerability in August indicated that the threat group remained very much alive.
According to a report by SecurityScorecard, Volt Typhoon has started to rebuild its botnet by targeting outdated Cisco and Netgear routers and has compromised a significant number of devices in just over a month.
Those routers are compromised using MIPS-based malware and webshells that communicate over non-standard ports, making detection more challenging.
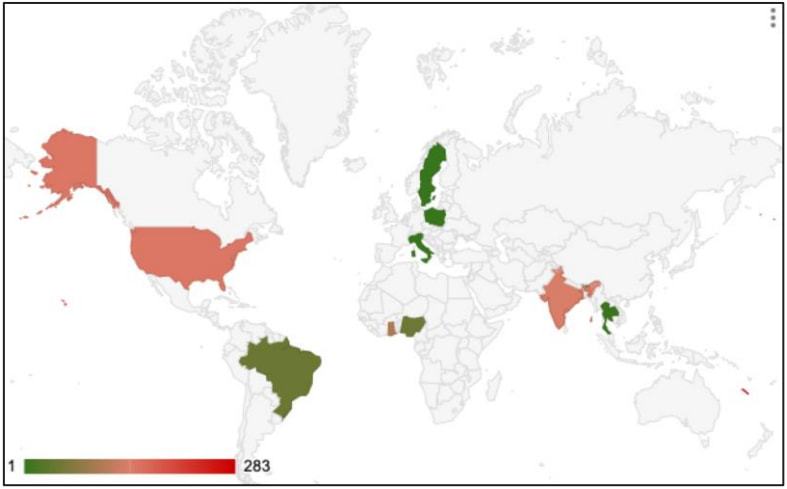
Source: SecurityScorecard
Volt Typhoon is back in action
SecurityScorecard reports that, since September, Volt Typhoon has returned through a new network of compromised devices primarily located in Asia.
The KV-Botnet, also dubbed ‘JDYFJ Botnet’ by SecurityScorecard due to the self-signed SSL certificate seen in the compromised devices, attempts to mainly compromise Cisco RV320/325 and Netgear ProSafe series devices.
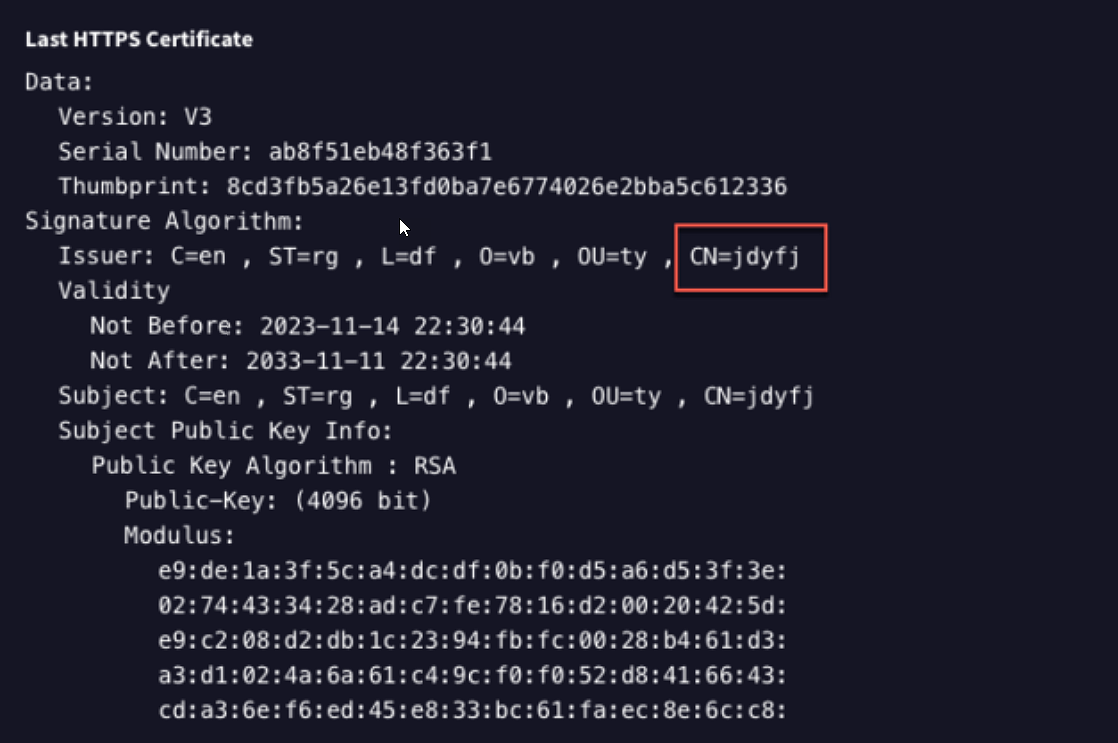
Source: SecurityScorecard
SecurityScorecard’s STRIKE Team researchers say that, in just 37 days, Volt Typhoon has compromised roughly 30% of all internet-exposed Cisco RV320/325 devices. However, it is not known at this time how the devices are breached.
“We don’t know specifically what weakness or flaw is being exploited. However with the devices being end of life, updates are no longer provided,” the researchers told BleepingComputer.
Also, the researchers told BleepingComputer that they don’t have any insight into what malware is used in the revived botnet. However, they noted that some of the same devices that were infected before the crackdown joined the cluster again.
The main operation of the KV-Botnet appears to be obfuscating malicious activities by routing traffic through the compromised legitimate infrastructure.
The botnet’s command servers are registered on Digital Ocean, Quadranet, and Vultr, to achieve a more diverse and resilient network.
Interestingly, Volt Typhoon uses a compromised VPN device located in the Pacific island of New Caledonia as a bridge that routes traffic between Asia-Pacific and America, acting as a stealthy hub.
Commenting on this choice, SecurityScorecard told BleepingComputer that it’s likely a geography-based decision from the threat actors.
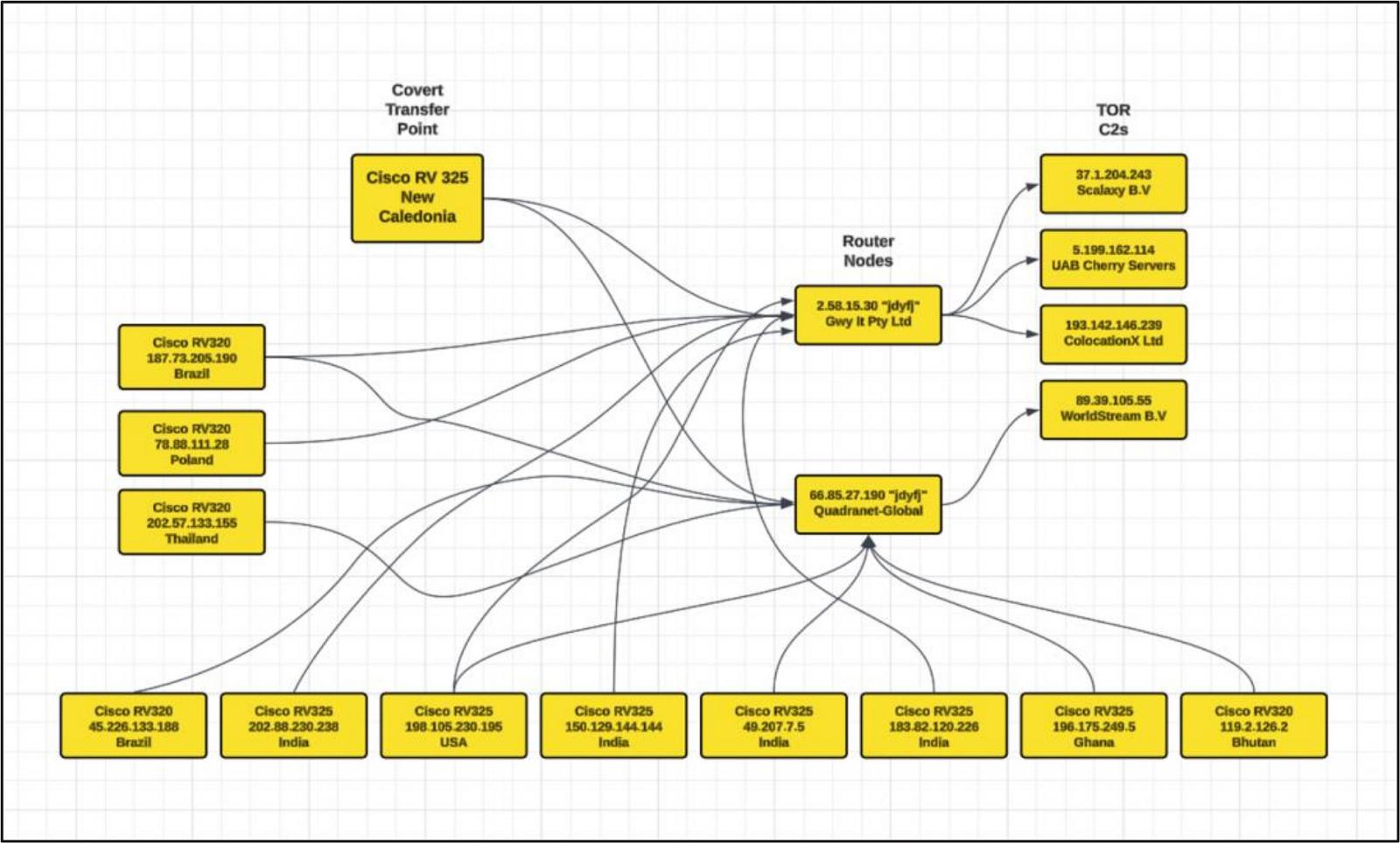
Source: SecurityScorecard
The observed activity signifies Volt Typhoon’s return to global operations, and although the scale of the botnet is nowhere near previous iterations, the Chinese hackers are bound to push forward with continued persistence.
To protect against this threat, older and unsupported router devices should be replaced with newer models, placed behind firewalls, remote access to admin panels should not be exposed to the internet, and default admin account credentials should be changed.
If you are using newer SOHO routers, be sure to install the latest firmware as it becomes available to fix known vulnerabilities.
Source link
lol
The Chinese state-sponsored hacking group Volt Typhoon has begun to rebuild its “KV-Botnet” malware botnet after it was disrupted by law enforcement in January, according to researchers from SecurityScorecard. Volt Typhoon is a Chinese state-sponsored cyberespionage threat group that is believed to have infiltrated critical U.S. infrastructure, among other networks worldwide, since at least five years…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
