Microsoft patches Windows zero-day exploited in attacks on Ukraine
by nlqip

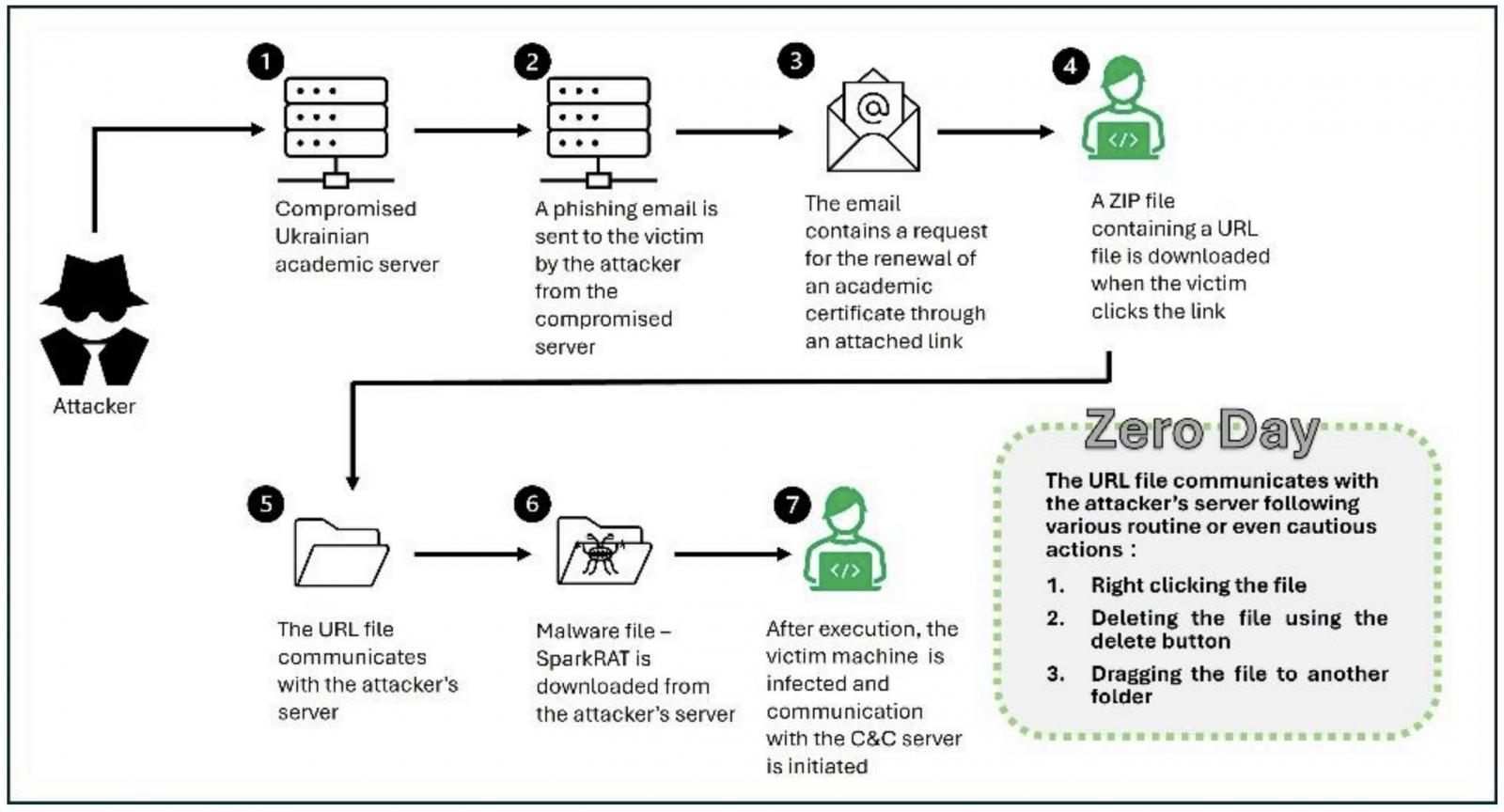
Suspected Russian hackers were caught exploiting a recently patched Windows vulnerability as a zero-day in ongoing attacks targeting Ukrainian entities.
The security flaw (CVE-2024-43451) is an NTLM Hash Disclosure spoofing vulnerability reported by ClearSky security researchers, which can be exploited to steal the logged-in user’s NTLMv2 hash by forcing connections to a remote attacker-controlled server.
ClearSky spotted this campaign in June after observing phishing emails designed to exploit it. These emails contained hyperlinks that would download an Internet shortcut file hosted on a previously compromised server (osvita-kp.gov[.]ua) belonging to the Kamianets-Podilskyi City Council’s Department of Education and Science.
“When the user interacts with the URL file by right-clicking, deleting, or moving it, the vulnerability is triggered,” ClearSky said.
When this happens, a connection to a remote server is created to download malware payloads, including the SparkRAT open-source and multi-platform remote access tool that enables attackers to control compromised systems remotely.
While investigating the incident, the researchers were also alerted of an attempt to steal an NTLM hash via the Server Message Block (SMB) protocol. These password hashes can be used in “pass-the-hash” attacks or cracked to get a user’s plaintext password.
ClearSky shared this information with Ukraine’s Computer Emergency Response Team (CERT-UA), which linked the attacks to hackers part of a threat group believed to be Russian and tracked as UAC-0194.
Yesterday, Microsoft patched the vulnerability as part of the November 2024 Patch Tuesday and confirmed ClearSky’s findings, saying that user interaction is required for successful exploitation.
“This vulnerability discloses a user’s NTLMv2 hash to the attacker who could use this to authenticate as the user,” Redmond’s advisory explained.
“Minimal interaction with a malicious file by a user such as selecting (single-click), inspecting (right-click), or performing an action other than opening or executing could trigger this vulnerability.”
The company says CVE-2024-43451 affects all supported Windows versions, including Windows 10 or later and Windows Server 2008 and up.
CISA also added the vulnerability to its Known Exploited Vulnerabilities Catalog on Tuesday, ordering them to secure vulnerable systems on their networks by December 3, as mandated by the Binding Operational Directive (BOD) 22-01.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” the cybersecurity agency warned.
Source link
lol
Suspected Russian hackers were caught exploiting a recently patched Windows vulnerability as a zero-day in ongoing attacks targeting Ukrainian entities. The security flaw (CVE-2024-43451) is an NTLM Hash Disclosure spoofing vulnerability reported by ClearSky security researchers, which can be exploited to steal the logged-in user’s NTLMv2 hash by forcing connections to a remote attacker-controlled server.…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
