Chinese hackers exploit Fortinet VPN zero-day to steal credentials
by nlqip

Chinese threat actors use a custom post-exploitation toolkit named ‘DeepData’ to exploit a zero-day vulnerability in Fortinet’s FortiClient Windows VPN client that steal credentials.
The zero-day allows the threat actors to dump the credentials from memory after the user authenticated with the VPN device
Volexity researchers report that they discovered this flaw earlier this summer and reported it to Fortinet, but the issue remains unfixed, and no CVE has been assigned to it.
“Volexity reported this vulnerability to Fortinet on July 18, 2024, and Fortinet acknowledged the issue on July 24, 2024,” explains the report.
“At the time of writing, this issue remains unresolved and Volexity is not aware of an assigned CVE number.”
Targeting VPN credentials
The attacks are conducted by Chinese hackers named “BrazenBamboo,” known for developing and deploying advanced malware families targeting Windows, macOS, iOS, and Android systems in surveillance operations.
Volexity explains that the threat actors utilize numerous malware as part of their attacks, including the LightSpy and DeepPost malware.
LightSpy is a multi-platform spyware for data collection, keylogging, browser credential theft, and the monitoring of communications. The DeepPost malware is used to steal data from compromised devices.
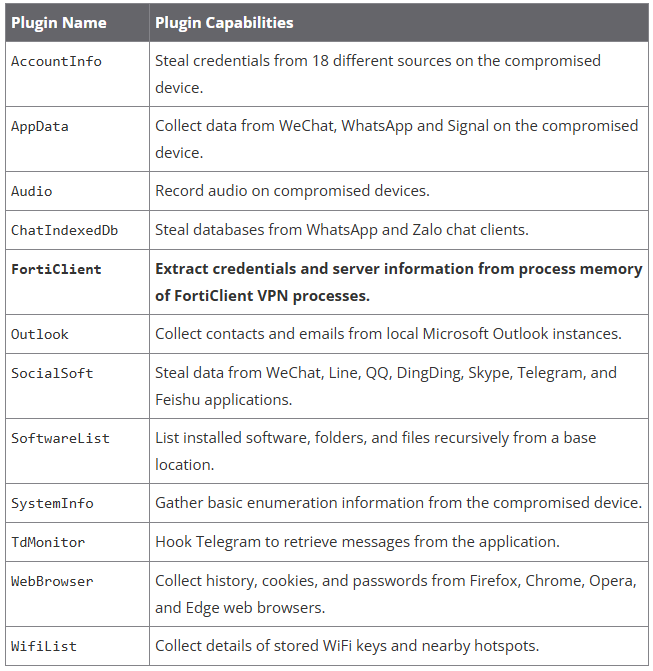
Volexity’s report focuses on DeepData, a modular post-exploitation tool for Windows, which employs multiple plugins for targeted data theft.
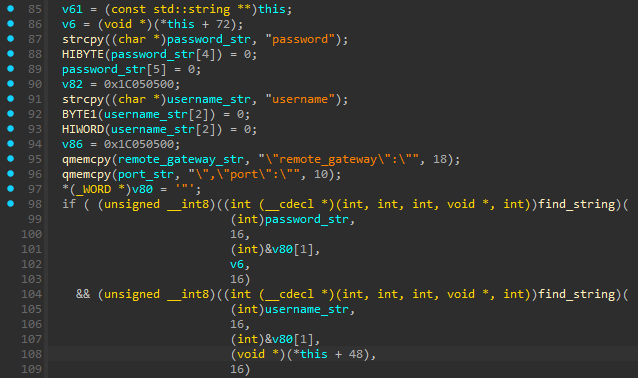
Its latest version, spotted last summer, DeepData includes a FortiClient plugin that exploits a zero-day vulnerability in the product to extract credentials (usernames, passwords) and VPN server information.
DeepData locates and decrypts JSON objects in FortiClient’s process memory where the credentials persist, and exfiltrates them to the attacker’s server using DeepPost.
Source: Volexity
By compromising VPN accounts, BrazenBamboo can gain initial access to corporate networks, where they can then spread laterally, gain access to sensitive systems, and generally expand espionage campaigns.
Source: Volexity
FortiClient zero-day
Volexity discovered that DeepData leverages the FortiClient zero in mid-July 2024 and found that it’s similar to a 2016 flaw (also without a CVE), where hardcoded memory offsets exposed credentials.
However, the 2024 vulnerability is new and distinct and works only on recent releases, including the latest, v7.4.0, indicating that it’s likely tied to recent changes in the software.
Volexity explains that the problem is FortiClient’s failure to clear sensitive information from its memory, including username, password, VPN gateway, and port, which remain in JSON objects in memory.
Until Fortinet confirms the flaw and releases a fixing patch, it is recommended to restrict VPN access and monitor for unusual login activity.
Indicators of compromise associated with the latest BrazenBamboo campaign are available here.
BleepingComputer contacted Fortinet to ask about the reported zero-day vulnerability and whether they plan to issue a security update soon, but we are still waiting for their response.
Source link
lol
Chinese threat actors use a custom post-exploitation toolkit named ‘DeepData’ to exploit a zero-day vulnerability in Fortinet’s FortiClient Windows VPN client that steal credentials. The zero-day allows the threat actors to dump the credentials from memory after the user authenticated with the VPN device Volexity researchers report that they discovered this flaw earlier this summer and…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
