McLaren hospitals disruption linked to INC ransomware attack
by nlqip

On Tuesday, IT and phone systems at McLaren Health Care hospitals were disrupted following an attack linked to the INC Ransom ransomware operation.
McLaren is a non-profit healthcare system with annual revenues of over $6.5 billion, which operates a network of 13 hospitals across Michigan supported by a team of 640 physicians. It also has over 28,000 employees and works with 113,000 network providers throughout Michigan, Indiana, and Ohio.
“While McLaren Health Care continues to investigate a disruption to our information technology system, we want to ensure our teams are as prepared as possible to care for patients when they arrive,” a statement on the health system’s website reads.
“Patients with scheduled appointments should plan to attend those appointments unless they are contacted by a member of our care team.
McLaren hinted the hospitals had lost access to patient information databases when advising patients to bring detailed information about their current medications to appointments, including physician orders and printed results of recent lab tests. The health system also said it may have to reschedule some appointments and non-emergent or elective procedures “out of an abundance of caution.”
“We understand this situation may be frustrating to our patients – and to our team members – and we deeply and sincerely apologize for any inconvenience this may cause,” McLaren added. “We kindly ask for your patience while our caregivers and support teams work as diligently as ever to provide our communities the care they need and deserve.”
Even though McLaren has yet to disclose the nature of the incident, employees at McLaren Bay Region Hospital in Bay City have shared a ransom note warning that the hospital’s systems have been encrypted and stolen data will be published on INC RANSOM ransomware gang’s leak site if a ransom is not paid.
INC Ransom is a ransomware-as-a-service (RaaS) operation that surfaced in July 2023 and has since targeted organizations in both the public and private sectors.
The list of victims includes education, healthcare, government, and industrial entities like Yamaha Motor Philippines, the U.S. division of Xerox Business Solutions (XBS), and Scotland’s National Health Service (NHS).
In May, a threat actor known as “salfetka” claimed to be selling source code of INC Ransom’s Windows and Linux/ESXi encrypter versions for $300,000 on the Exploit and XSS hacking forums.
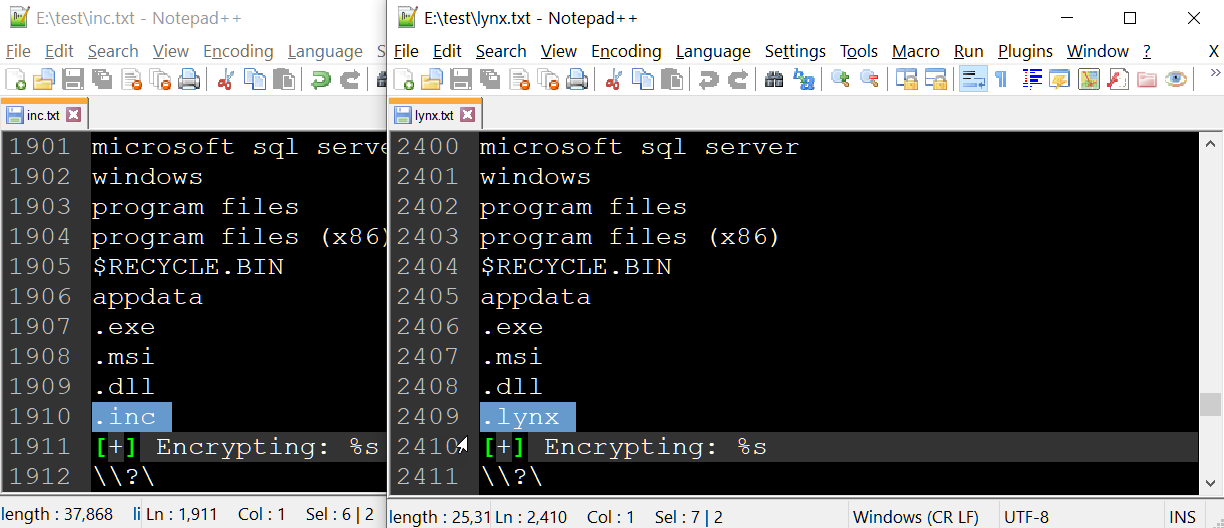
Two months later, in July, malware analysts stated that the source code might have been purchased by a newly emerged ransomware group called Lynx ransomware. However, this could also be a rebranding effort, potentially allowing INC RANSOM to continue operations with less scrutiny from law enforcement.
BleepingComputer did an analysis of strings between the new Lynx ransomware encryptors and recent INC encryptors, and other than small changes, can confirm they are mostly the same.
In November 2023, McLaren notified almost 2.2 million people of a data breach that exposed their personal and health information between late July and August 2023.
Compromised data included names, Social Security numbers, health insurance and physician information, as well as Medicare/Medicaid, prescription/medication, and diagnostic results and treatment information.
The ALPHV/BlackCat ransomware group claimed the July 2023 attack behind the data breach on October 4.
Source link
lol
Image: MidjourneyOn Tuesday, IT and phone systems at McLaren Health Care hospitals were disrupted following an attack linked to the INC Ransom ransomware operation. McLaren is a non-profit healthcare system with annual revenues of over $6.5 billion, which operates a network of 13 hospitals across Michigan supported by a team of 640 physicians. It also…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
