Ransom Cartel, Reveton ransomware owner arrested, charged in US
by nlqip

Belarusian-Ukrainian national Maksim Silnikau was arrested in Spain and extradited to the USA to face charges for creating the Ransom Cartel ransomware operation in 2021 and for running a malvertising operation from 2013 to 2022.
The threat actor operated under the aliases “J.P. Morgan,” “xxx,” and “lansky” on Russian-speaking hacking forum, where he allegedly promoted the cybercrime operations.
The authorities unsealed two separate indictments, one on the District of New Jersey concerning the malvertising operation and one on the Eastern District of Virginia for the Ransom Cartel operation.
Co-conspirators Volodymyr Kadariya, a Belarussian and Ukrainian national, 38, and Andrei Tarasov, a Russian national, 33, were also charged for their role in the malvertising operation.
“These conspirators are alleged to have operated a multiyear scheme to distribute malware onto the computers of millions of unsuspecting internet users around the globe,” said U.S. Attorney Philip R. Sellinger for the District of New Jersey. “To carry out the scheme, they used malicious advertising, or ‘malvertising’, to trick victims into clicking on legitimate-seeming internet ads.”
The UK’s National Crime Agency shared a video of Silnikau’s arrest on Twitter.
An international operation coordinated by the NCA has resulted in the arrest and extradition of a man believed to be one of the world’s most prolific Russian-speaking cybercrime actors.
FULL STORY https://t.co/kgPdMAwqPZ pic.twitter.com/MVjRLco55R
— National Crime Agency (NCA) (@NCA_UK) August 13, 2024
The Ransom Cartel operation
Ransom Cartel is a ransomware operation launched in December 2021, with its encryptor featuring extensive code similarities to the REvil family.
The lack of strong obfuscation prompted analysts to assume that it was the creation of a core member who was missing the obfuscation engine found in REvil rather than a reboot/rebrand from the same team of cybercriminals.
According to the indictment, Silnikau created and administrated Ransom Cartel, managing the “ransomware-as-a-service” operation and recruiting other cybercriminals from Russian-speaking forums to participate in attacks.
He also negotiated with “initial access brokers” (IABs) who provided access to compromised corporate networks, managed communications with victims, and handled ransom payments.
Silnikau also transferred ransom payments through cryptocurrency mixers to obscure the money trail and complicate law enforcement efforts, clearly holding a central role in the operation.
.png)
Source: BleepingComputer
Reveton ransomware
The NCA also states that Silnikau was behind the notorious Reveton trojan, a Windows malware that locked users out of the operating system until a ransom was paid.
The malware launched in 2011 and pretended to be law enforcement locking a computer because child pornography and copyrighted material was detected.
To gain access to the computer, victims were required to send a ransom in the form of a MoneyPak, PaySafeCard, or other online payment.
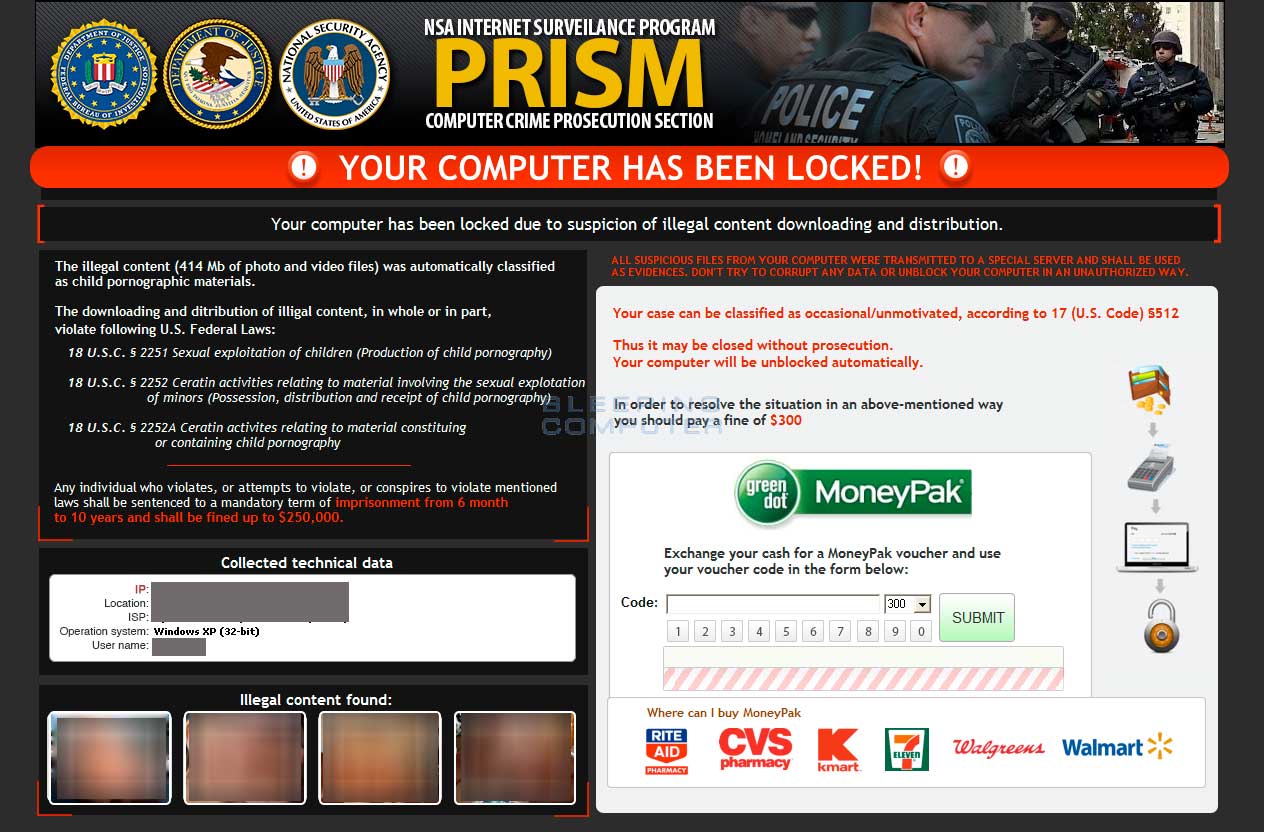
Source: BleepingComputer
Between 2012 and 2014, Reveton, that was sold to various cybercriminals for profit, generated $400,000 daily.
Malvertising operation
The defendant also played a leading role in orchestrating and executing a large-scale malvertising scheme from October 2013 to March 2022.
His primary responsibilities included developing and distributing malicious advertisements that appeared legitimate but redirected users to sites containing malware, scareware, and online scams.
Specifically, the operation distributed the following:
- Angler Exploit Kit (AEK): Designed to exploit flaws in web browsers and plugins installed on them, to deliver additional payloads on the compromised devices.
- Locker malware: A kind of ‘lite’ ransomware tool that prevents the victim from accessing their data, often demanding a payment to restore access.
- Scareware: Deception tools that alleged infections on the victims’ computers via forged alerts, prompting them to download harmful software or provide personal information to the cybercriminals.
Silnikau used various online aliases and fake companies to deceive the abused advertising platforms and was directly involved in selling access to devices compromised via this scheme.
Additionally, he collaborated on the development and maintenance of technical infrastructure, such as Traffic Distribution Systems (TDSes), to manage and target their malicious campaigns more effectively.
At its peak, Angler represented 40% of all exploit kit infections, having targeted around 100,000 devices and with an estimated annual turnover of around $34 million. – NCA
Maksim Silnikau is facing serious legal consequences based on the charges in both indictments, including imprisonment sentences for wire fraud, computer fraud, computer fraud and abuse, aggravated identity theft, and access device fraud.
If convicted on all charges, Silnikau could potentially face a sentence exceeding 100 years in prison, though the sentencing time is typically much shorter due to the sentences being served concurrently.
Source link
lol
Belarusian-Ukrainian national Maksim Silnikau was arrested in Spain and extradited to the USA to face charges for creating the Ransom Cartel ransomware operation in 2021 and for running a malvertising operation from 2013 to 2022. The threat actor operated under the aliases “J.P. Morgan,” “xxx,” and “lansky” on Russian-speaking hacking forum, where he allegedly promoted the cybercrime operations.…
Recent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
