Ivanti warns of critical vTM auth bypass with public exploit
by nlqip

Today, Ivanti urged customers to patch a critical authentication bypass vulnerability impacting Virtual Traffic Manager (vTM) appliances that can let attackers create rogue administrator accounts.
Ivanti vTM is a software-based application delivery controller (ADC) that provides app-centric traffic management and load balancing for hosting business-critical services.
Tracked as CVE-2024-7593, this auth bypass vulnerability is due to an incorrect implementation of an authentication algorithm that allows remote unauthenticated attackers to bypass authentication on Internet-exposed vTM admin panels.
“Ivanti released updates for Ivanti Virtual Traffic Manager (vTM) which addressed a critical vulnerability. Successful exploitation could lead to authentication bypass and creation of an administrator user,” the company warned on Tuesday.
“We are not aware of any customers being exploited by this vulnerability at the time of disclosure. However, a Proof of Concept is publicly available, and we urge customers to upgrade to the latest patched version. “
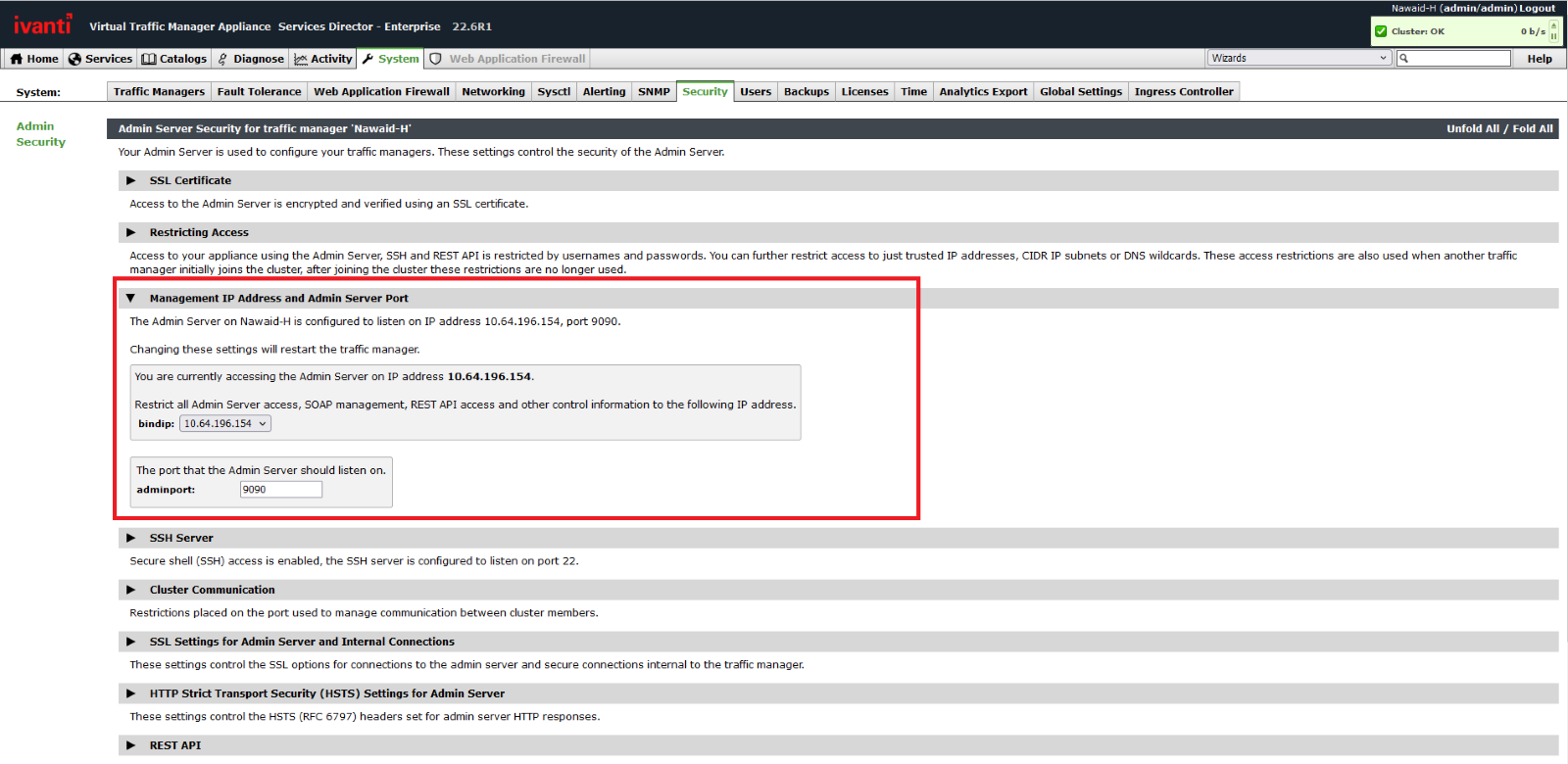
Ivanti advises admins to restrict access to the vTM management interface by binding it to an internal network or private IP address to reduce the attack surface and block potential exploitation attempts.
To limit admin access to the management interface through the private/corporate network, admins have to:
- Navigate to System > Security, then click the drop-down for the Management IP Address and Admin Server Port section of the page.
- In the ‘bindip’ drop-down, select the Management Interface IP Address or use the setting directly above the “bindip” setting to restrict access to trusted IP addresses, further limiting who can access the interface.
The security flaw has been fixed in Ivanti vTM 22.2R1 and 22.7R2, with patches to be released for the remaining supported versions over the coming weeks.
Ivanti says it has no evidence that the CVE-2024-7593 auth bypass has been exploited in attacks but advised admins to check the Audit Logs Output for new ‘user1’ or ‘user2’ admin users added via the GUI or using the publicly available exploit code.
Today, Ivanti also warned admins to immediately patch an information disclosure vulnerability (CVE-2024-7569) in Ivanti ITSM on-prem and Neurons for ITSM versions 2023.4 and earlier. This vulnerability can let unauthenticated attackers obtain the OIDC client secret via debug information.
The company patched another authentication bypass flaw (CVE-2024-22024) impacting Ivanti Connect Secure, Policy Secure, and ZTA gateways in February when it urged admins to secure vulnerable appliances immediately.
Ivanti VPN appliances have been under attack since December 2023 using exploits chaining the CVE-2023-46805 authentication bypass and the CVE-2024-21887 command injection flaws as zero days.
The company also warned of a third zero-day (a server-side request forgery bug tracked as CVE-2024-21893) under mass exploitation in February, allowing threat actors to bypass authentication on unpatched ICS, IPS, and ZTA gateways.
Source link
lol
Today, Ivanti urged customers to patch a critical authentication bypass vulnerability impacting Virtual Traffic Manager (vTM) appliances that can let attackers create rogue administrator accounts. Ivanti vTM is a software-based application delivery controller (ADC) that provides app-centric traffic management and load balancing for hosting business-critical services. Tracked as CVE-2024-7593, this auth bypass vulnerability is due…
Recent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
