CISA warns of Jenkins RCE bug exploited in ransomware attacks
by nlqip

CISA has added a critical Jenkins vulnerability that can be exploited to gain remote code execution to its catalog of security bugs, warning that it’s actively exploited in attacks.
Jenkins is a widely used open-source automation server that helps developers automate the process of building, testing, and deploying software through continuous integration (CI) and continuous delivery (CD).
Tracked as CVE-2024-23897, this flaw is caused by a weakness in the args4j command parser that unauthenticated attackers can exploit to read arbitrary files on the Jenkins controller file system through the built-in command line interface (CLI).
“This command parser has a feature that replaces an @ character followed by a file path in an argument with the file’s contents (expandAtFiles),” the Jenkins team explained. “This feature is enabled by default and Jenkins 2.441 and earlier, LTS 2.426.2 and earlier does not disable it.”
Multiple proof-of-concept (PoC) exploits were published online days after Jenkins devs released security updates on January 24, with some honeypots reportedly catching exploitation attempts just one day later.
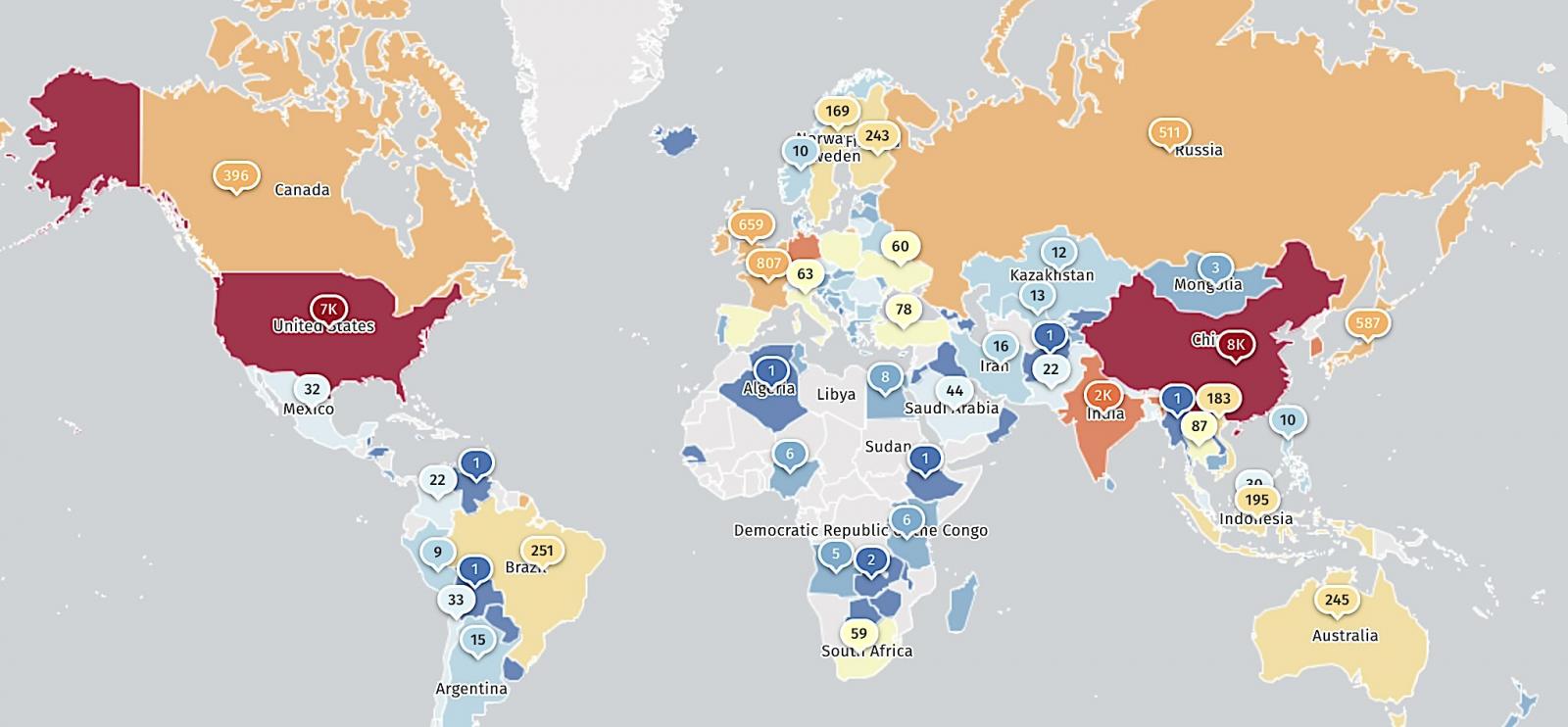
Threat monitoring service Shadowserver currently tracks over 28,000 Jenkins instances exposed to CVE-2024-23897—most of them from China (7,700) and the United States (7,368)—indicating a massive attack surface that has slowly reduced from more than 45,000 unpatched servers found in January.
According to a Trend Micro report, CVE-2024-23897 in the wild exploitation started in March, while CloudSEK claimed earlier this month that a threat actor known as IntelBroker had exploited it to breach IT service provider BORN Group.
More recently, Juniper Networks said last week the RansomEXX gang exploited the vulnerability to breach the systems of Brontoo Technology Solutions, which provides technology services to Indian banks, in late July. This ransomware attack caused widespread disruptions to retail payment systems throughout the country.
Following these reports, CISA added the security vulnerability to its Known Exploited Vulnerabilities catalog on Monday, warning that threat actors are actively exploiting it in attacks.
As mandated by the binding operational directive (BOD 22-01) issued in November 2021, Federal Civilian Executive Branch Agencies (FCEB) agencies now have three weeks until September 9 to secure Jenkins servers on their networks against ongoing CVE-2024-23897 exploitation,
Even though BOD 22-01 only applies to federal agencies, CISA strongly urged all organizations to prioritize fixing this flaw and thwart potential ransomware attacks that could target their systems.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” the cybersecurity agency warned today.
Source link
lol
CISA has added a critical Jenkins vulnerability that can be exploited to gain remote code execution to its catalog of security bugs, warning that it’s actively exploited in attacks. Jenkins is a widely used open-source automation server that helps developers automate the process of building, testing, and deploying software through continuous integration (CI) and continuous delivery…
Recent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
