Halliburton cyberattack linked to RansomHub ransomware gang
by nlqip

The RansomHub ransomware gang is behind the recent cyberattack on oil and gas services giant Halliburton, which disrupted the company’s IT systems and business operations.
The attack caused widespread disruption, and BleepingComputer was told that customers couldn’t generate invoices or purchase orders because the required systems were down.
Halliburton disclosed the attack last Friday in an SEC filing, stating they suffered a cyberattack on August 21, 2024, by an unauthorized party.
“On August 21, 2024, Halliburton Company (the “Company”) became aware that an unauthorized third party gained access to certain of its systems,” read Halliburton’s SEC filing.
“When the Company learned of the issue, the Company activated its cybersecurity response plan and launched an investigation internally with the support of external advisors to assess and remediate the unauthorized activity.”
The company provides a numerous services to oil and gas companies, including well construction, drilling, hydraulic fracturing (fracking), and IT software and services. Due to the company’s wide range of services, there is a great deal of connectivity between them and their customers.
However, the company has not shared many details about the attack, with a customer in the oil and gas industry telling BleepingComputer that they have been left in the dark about determining if the attack impacted them and how to protect themselves.
This has caused other customers to disconnect from Halliburton due to the lack of information being shared.
BleepingComputer has also been told that some companies are working with ONG-ISAC—an agency that acts as a central point of coordination and communication for physical and cybersecurity threats against the oil and gas industry—to receive technical information about the attack to determine if they were breached as well.
RansomHub ransomware behind the attack
For days, there have been rumors that Halliburton suffered a RansomHub ransomware attack, with users claiming this on Reddit and on the job layoff discussion site, TheLayoff, where a partial RansomHub ransom note was published.
When BleepingComputer contacted Halliburton about these claims, Halliburton said they were not making any further comments.
“We are not commenting beyond what was included in our filing. Any subsequent communications will be in the form of an 8-K,” Halliburton told BleepingComputer.
However, in an August 26 email sent to suppliers and shared with BleepingComputer, Halliburton provided additional information stating that the company took systems offline to protect them and is working with Mandiant to investigate the incident.
“We are reaching out to update you about a cybersecurity issue affecting Halliburton,” reads the letter seen by BleepingComputer.
“As soon as we learned of the issue, we activated our cybersecurity response plan and took steps to address it, including (1) proactively taking certain systems offline to help protect them, (2) engaging the support of leading external advisors, including Mandiant, and (3) notifying law enforcement.”
They also stated that their email systems continue to operate as they’re hosted on Microsoft Azure infrastructure. A workaround is also available for transacting and issuing purchase orders.
This email includes a list of IOCs containing file names and IP addresses associated with the attack that customers can use to detect similar activity on their network.
One of these IOCs is for a Windows executable named maintenance.exe, which BleepingComputer has confirmed to be a RansomHub ransomware encryptor.
After analyzing the sample, it appears to be a newer version than previously analyzed, as it contains a new “-cmd string” command-line argument, which will execute a command on the device before encrypting files.
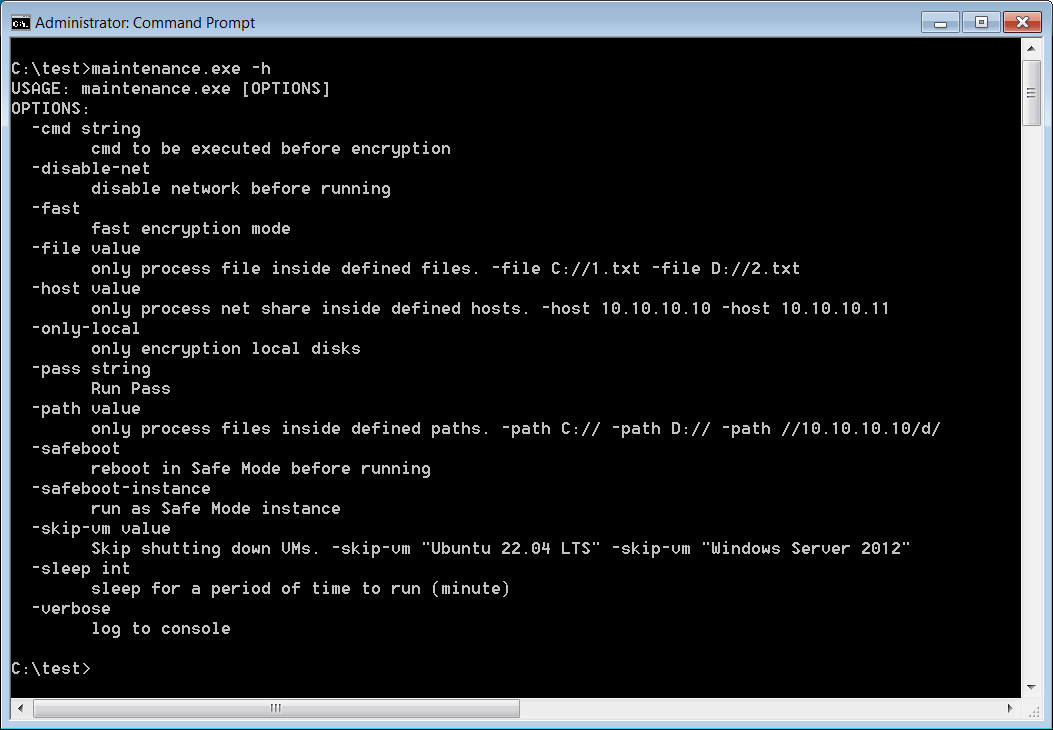
Source: BleepingComputer
RansomHub
The RansomHub ransomware operation launched in February 2024, claiming it was a data theft extortion and extortion group that sold stolen files to the highest bidder.
However, soon after, it was discovered that the operation also utilized ransomware encryptors in its double-extortion attacks, where the threat actors breached networks, stole data, and then encrypted files.
The encrypted files and the threat to leak stolen data were then used as leverage to scare companies into paying a ransom.
Symantec analyzed the ransomware encryptors and reported that they were based on the Knight ransomware encryptors, formerly known as Cyclops.
The Knight operation claimed they sold their source code in February 2024 and shut down just as RansomHub launched. This has made many researchers believe that RansomHub is a rebrand of the Knight ransomware operation.
Today, the FBI released an advisory about RansomHub, sharing the threat actor’s tactics and warning that they breached at least 210 victims since February.
It is common for the FBI and CISA to publish coordinated advisories on threat actors soon after they conduct a highly impactful attack on critical infrastructure, such as Halliburton. However, it is not known if the advisory and the attack are linked.
Since the start of the year, RansomHub has been responsible for numerous high-profile attacks, including those on American not-for-profit credit union Patelco, the Rite Aid drugstore chain, the Christie’s auction house, and U.S. telecom provider Frontier Communications.
The ransomware operation’s data leak site was also utilized to leak stolen data belonging to Change Healthcare following the shutdown of the BlackCat and ALPHV ransomware operation.
It is believed that after BlackCat shut down, some of its affiliates moved to RansomHub, allowing them to quickly escalate their attacks with experienced ransomware threat actors.
Source link
lol
The RansomHub ransomware gang is behind the recent cyberattack on oil and gas services giant Halliburton, which disrupted the company’s IT systems and business operations. The attack caused widespread disruption, and BleepingComputer was told that customers couldn’t generate invoices or purchase orders because the required systems were down. Halliburton disclosed the attack last Friday in…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
