Sextortion scam now use your “cheating” spouse’s name as a lure
by nlqip

A new variant of the ongoing sextortion email scams is now targeting spouses, saying that their husband or wife is cheating on them, with links to the alleged proof.
In sextortion emails, scammers pretend to have hacked your computer to steal images or videos of you performing sexual acts and demand that you send a payment of $500 to $5,000 not to have them sent to family and friends.
While you may think that no one would fall for these scams, they were very profitable when they first appeared in 2018, generating over $50,000 in a week.
Since then, scammers have created a wide variety of extortion email scams, including ones that pretend to be hitman contracts, bomb threats, CIA investigations, and threats of installing ransomware.
“Cheating” spouses
Threat actors first began sending this new sextortion email variant about three weeks ago, with both wives and husbands reporting on Reddit that they received the email.
“I received this email addressed to my partner (in blue), saying that they have “proof i am cheating”. My name is red. It’s coming from community@3bigs.com. I also have the option to opt-out of communications if I wish,” a recipient of the email posted to Reddit.
“They have used our full names (even my second last name that I barely use anywhere) and I am not sure how they found this information. I am pretty sure it’s a scam but I couldn’t find any information on this online…. anyone had this happen to them? It’s so creepy tf.”
Recipients reported receiving emails from different domains, including 3bigs[.]com and the domain savkar[.]ai with subjects of “Hi [name] please check this report.”
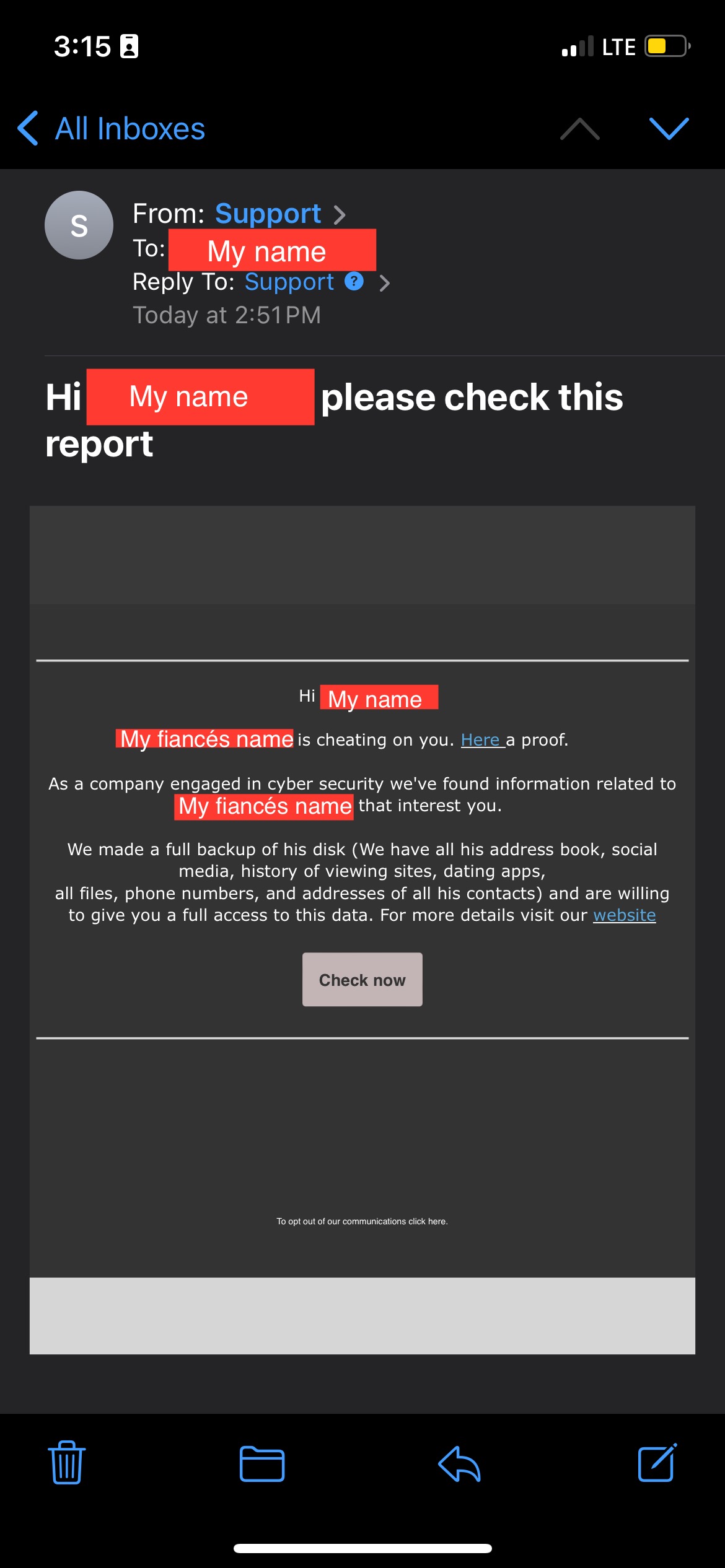
Source: BleepingComputer
The emails claim that the recipient’s spouse was hacked and the threat actors stole data from his devices that shows that he/she was cheating on them.
The full text of this email is below:
“[Spouse’s name] is cheating on your. Here a proof.
As a company engaged in cyber security we’ve found information to [Spouse’s name] that interest you.
We made a full backup of his disk (We have all his address book, social media, history of viewing sites, dating apps, all files, phone numbers, and addresses of all his contacts) and are willing to give you full access to this data. For more details visit our website.”
What made most email recipients concerned was the use of names that are not generally associated with them or used online, such as maiden names, second last names, or even their pet’s name.
While it is unclear where the information comes from, many Reddit users claim they only shared it on a wedding planning site called The Knot. This includes the person who said they received the email about their “cheating” dog, Mr. Wiggles, whose name was also shared on the site.
BleepingComputer contacted The Knot last week to see if they suffered a data breach but never received a reply to our email.
As for the extortion links, BleepingComputer attempted to obtain the emails to see where they led but could not do so.
However, we spoke to different people who received the emails, and one stated that the link led to a page asking them to log in, while another believed it was trying to distribute malware.
Thankfully, sextortion scams have become so abundant over the past six years that most people recognized it for what it was and deleted the emails.
However, it still distressed many of those who received it. Therefore, it is important to stress that these emails are scams, they are not telling the truth, and you should not visit the links in these emails.
If you received this email, just delete it.
Source link
lol
A new variant of the ongoing sextortion email scams is now targeting spouses, saying that their husband or wife is cheating on them, with links to the alleged proof. In sextortion emails, scammers pretend to have hacked your computer to steal images or videos of you performing sexual acts and demand that you send a…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
