NoName ransomware gang deploying RansomHub malware in recent attacks
by nlqip

The NoName ransomware gang has been trying to build a reputation for more than three years targeting small and medium-sized businesses worldwide with its encryptors and may now be working as a RansomHub affiliate.
The gang uses custom tools known as the Spacecolon malware family, and deploys them after gaining access to a network through brute-force methods as well as exploiting older vulnerabilities like EternalBlue (CVE-2017-0144) or ZeroLogon (CVE-2020-1472).
In more recent attacks NoName uses the ScRansom ransomware, which replaced the Scarab encryptor. Additionally, the threat actor tried to make a name by experimenting with the leaked LockBit 3.0 ransomware builder, creating a similar data leak site, and using similar ransom notes.
ScRansom ransomware
Cybersecurity company ESET tracks the NoName gang as CosmicBeetle and has been tracking its activities since 2023, with the emergence of the ScRansom, a Delphi-based file-encrypting malware.
In a report today, the researchers note that although ScRansom (part of the Spacecolon malware family) is not as sophisticated as other threats on the ransomware scene, it is a threat that continues to evolve.
The malware supports partial encryption with different speed modes to allow attackers some versatility, and also features an ‘ERASE’ mode that replaces file contents with a constant value, making them unrecoverable.
ScRansom can encrypt files across all drives, including fixed, remote, and removable media, and allows the operator to determine what file extensions to target through a customizable list.
Before launching the encryptor, ScRansom kills a list of processes and services on the Windows host, including Windows Defender, the Volume Shadow Copy, SVCHost, RDPclip, LSASS, and processes associated with VMware tools.
ESET notes that ScRansom’s encryption scheme is rather complicated, using a combo of AES-CTR-128 and RSA-1024, and an extra AES key generated to protect the public key.
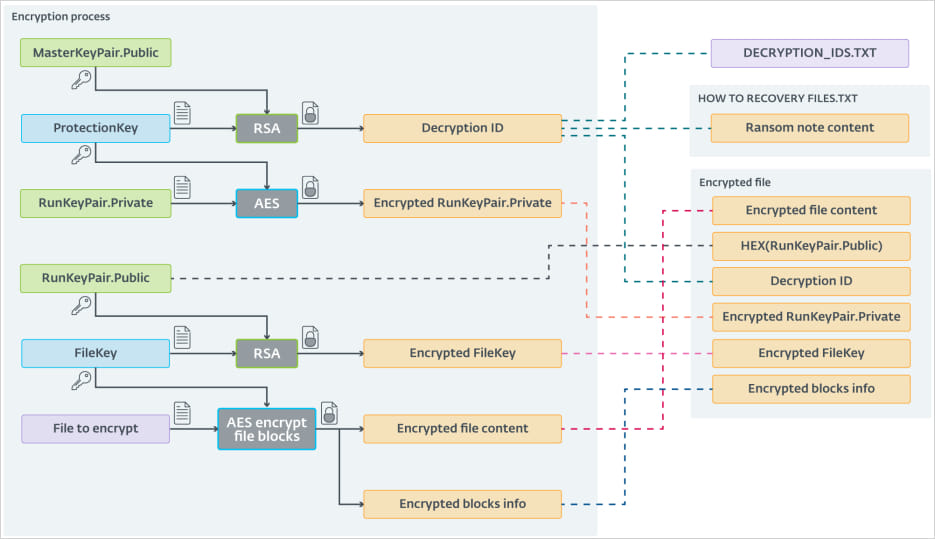
Source: ESET
However, the multi-step process that involves multiple key exchanges sometimes introduces errors that may lead to failure to decrypt the files even when using the correct keys.
Also, if the ransomware is executed a second time on the same device, or in a network of multiple distinct systems, new sets of unique keys and victim IDs will be generated, making the decryption process rather complex.
One case that ESET highlights is of a victim that received 31 decryption IDs and AES ProtectionKeys after paying ScRansom, and they were still unable to recover all the encrypted files.
NoName has been using brute force to gain access to networks but the threat actor also exploits several vulnerabilities that are more likely to be present in SMB environments:
• CVE-2017-0144 (aka EternalBlue),
• CVE-2023-27532 (a vulnerability in a Veeam Backup & Replication component)
• CVE-2021-42278 and CVE-2021-42287 (AD privilege escalation vulnerabilities) through noPac
• CVE-2022-42475 (a vulnerability in FortiOS SSL-VPN)
• CVE-2020-1472 (aka Zerologon)
A recent report from Pure7, a cybersecurity company in Turkey, also mentions that CVE-2017-0290 has also been exploited in NoName attacks through a batch file (DEF1.bat) that makes changes in Windows Registry to disable Windows Defender features, services, or tasks.
NoName deploying RansomHub tools
NoName’s ascension to the status of RansomHub affiliate was preceded by a set of moves showing the gang’s dedication to the ransomware business. Since ScRansom was not an established name on the scene, the gang decided to take a different approach to increase its visibility.
In September 2023, CosmicBeetle set up an extortion site on the dark web branded ‘NONAME,’ which was a modified copy of the LockBit data leak site (DLS) that included victims actually compromised by LockBit, not ScRansom, the researchers discovered after checking on multiple DLS-tracking services.
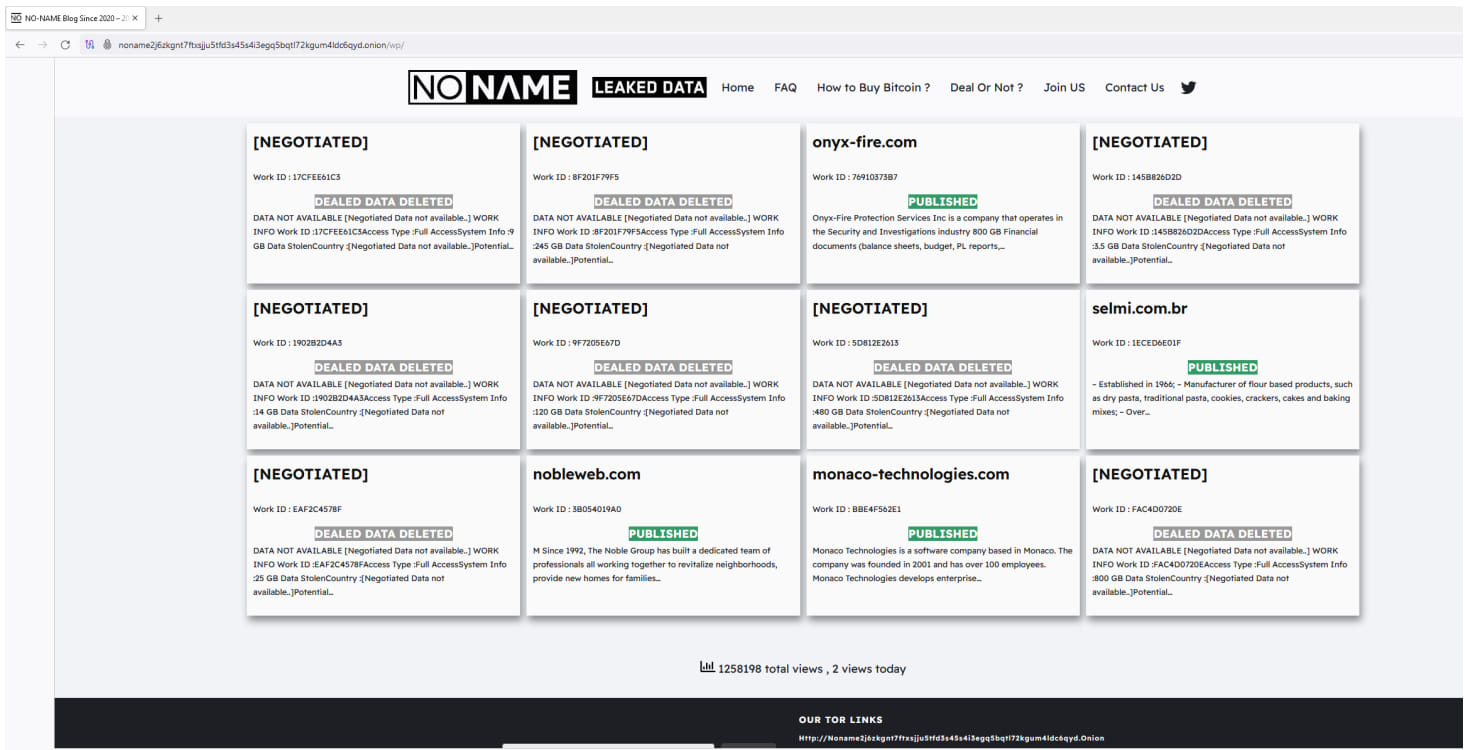
Source: ESET
In November 2023, the threat actor stepped up its impersonation effort by registering the domain lockbitblog[.]info and branding the DLS with the LockBit theme and logo.
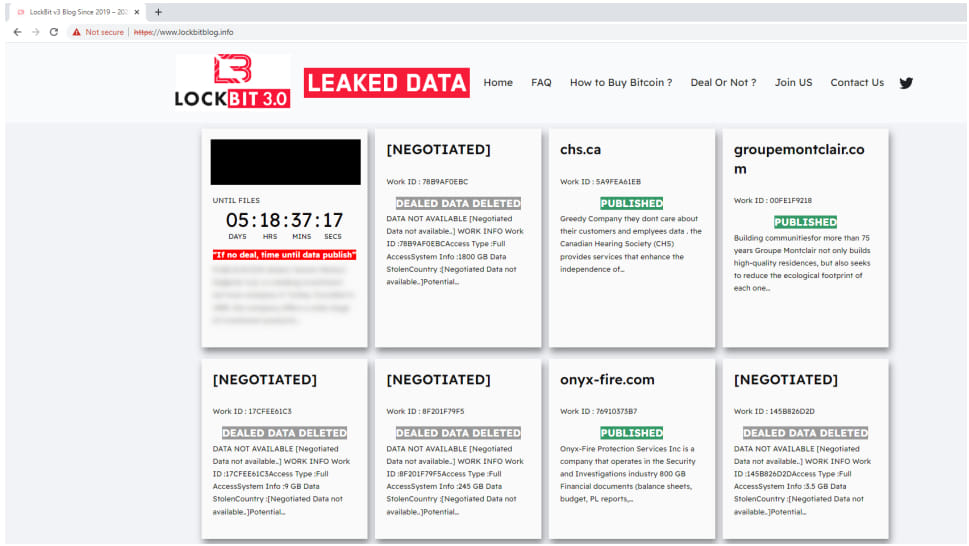
Source: ESET
The researchers also discovered some recent attacks where a LockBit sample was deployed but the ransom note had a victim ID that they had already linked to CosmicBeetle. Furthermore, the toolset in the incident overlapped with the malware attributed to the CosmicBeetle/NoName threat actor.
While investigating a ransomware incident that started in early June with a failed ScRansom deployment, ESET researchers found that the threat actor executed on the same machine less than a week later RansomHub’s EDR killer, a tool that allows privilege escalation and disabling security agents by deploying a legitimate, vulnerable driver on targeted devices.
Two days later, on June 10, the hackers executed the RansomHub ransomware on the compromised machine.
The researchers note the method for extracting the EDR killer, which was typical of CosmicBeetle and not a RansomHub affiliate.
Since there are no public leaks of the RansomHub code or its builder, ESET researchers “believe with medium confidence that CosmicBeetle enrolled itself as a new RansomHub affiliate.”
Although the affiliation with RanssomHub is not certain, ESET says that the ScRansom encrypter is under active development. Combined with the switch from ScRansom to LockBit, it indicates that CosmicBeetle is not showing any signs of giving up.
Source link
lol
The NoName ransomware gang has been trying to build a reputation for more than three years targeting small and medium-sized businesses worldwide with its encryptors and may now be working as a RansomHub affiliate. The gang uses custom tools known as the Spacecolon malware family, and deploys them after gaining access to a network through brute-force methods…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
