CISA warns of Windows flaw used in infostealer malware attacks
by nlqip

CISA has ordered U.S. federal agencies to secure their systems against a recently patched Windows MSHTML spoofing zero-day bug exploited by the Void Banshee APT hacking group.
The vulnerability (CVE-2024-43461) was disclosed during this month’s Patch Tuesday, and Microsoft initially classified it as not exploited in attacks. However, Microsoft updated the advisory on Friday to confirm that it had been exploited in attacks before being fixed.
Microsoft revealed that attackers exploited CVE-2024-43461 before July 2024 as a part of an exploit chain with CVE-2024-38112, another MSHTML spoofing bug.
“We released a fix for CVE-2024-38112 in our July 2024 security updates which broke this attack chain,” it said. “Customers should both the July 2024 and September 2024 security update to fully protect themselves.”
Peter Girnus, the Trend Micro Zero Day Initiative (ZDI) threat researcher who reported the security flaw, told BleepingComputer that Void Banshee hackers exploited it in zero-day attacks to install information-stealing malware.
The vulnerability enables remote attackers to execute arbitrary code on unpatched Windows systems by tricking the targets into visiting a maliciously crafted webpage or opening a malicious file.
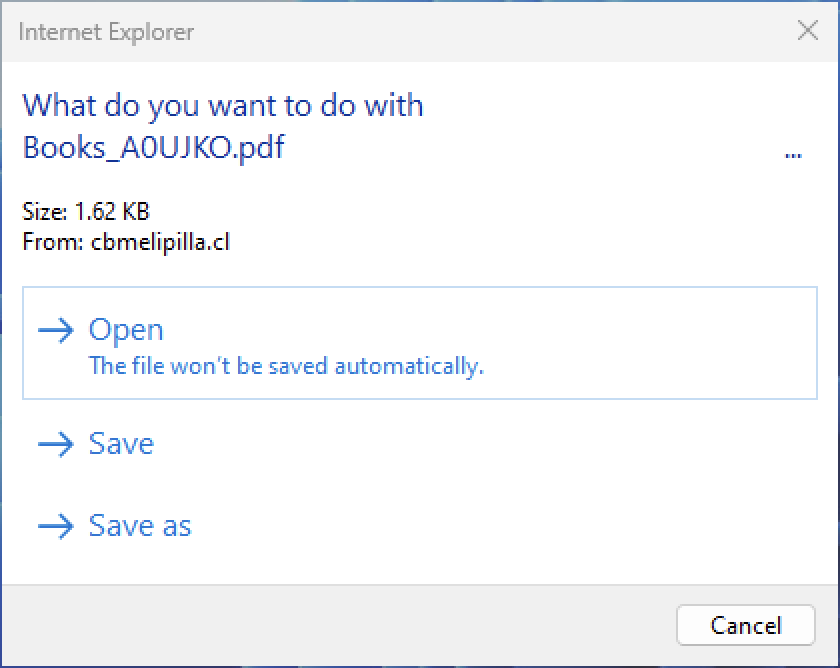
“The specific flaw exists within the way Internet Explorer prompts the user after a file is downloaded,” the ZDI advisory explains. “A crafted file name can cause the true file extension to be hidden, misleading the user into believing that the file type is harmless. An attacker can leverage this vulnerability to execute code in the context of the current user.”
They used CVE-2024-43461 exploits to deliver malicious HTA files camouflaged as PDF documents. To hide the .hta extension, they used 26 encoded braille whitespace characters (%E2%A0%80).
As revealed in July by Check Point Research and Trend Micro, the Atlantida information-stealing malware deployed in these attacks can help steal passwords, authentication cookies, and cryptocurrency wallets from infected devices.
Void Banshee is an APT hacking group first identified by Trend Micro and known for targeting organizations across North America, Europe, and Southeast Asia for financial gain and to steal data.
Federal agencies given three weeks to patch
Today, CISA has added the MSHTML spoofing vulnerability to its Known Exploited Vulnerabilities catalog, tagging it as actively exploited and ordering federal agencies to secure vulnerable systems within three weeks by October 7, as mandated by Binding Operational Directive (BOD) 22-01.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” the cybersecurity agency said.
Although CISA’s KEV catalog primarily focuses on alerting federal agencies about security flaws they should patch as soon as possible, private organizations worldwide are also advised to prioritize mitigating this vulnerability to block ongoing attacks.
Microsoft has patched three other actively exploited zero-days in the September 2024 Patch Tuesday. This includes CVE-2024-38217, a vulnerability exploited in LNK stomping attacks since at least 2018 to bypass the Smart App Control and the Mark of the Web (MotW) security feature.
Source link
lol
CISA has ordered U.S. federal agencies to secure their systems against a recently patched Windows MSHTML spoofing zero-day bug exploited by the Void Banshee APT hacking group. The vulnerability (CVE-2024-43461) was disclosed during this month’s Patch Tuesday, and Microsoft initially classified it as not exploited in attacks. However, Microsoft updated the advisory on Friday to confirm that…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
