Construction firms breached in brute force attacks on accounting software
by nlqip

Hackers are brute-forcing passwords for highly privileged accounts on exposed Foundation accounting servers, widely used in the construction industry, to breach corporate networks.
The malicious activity was first spotted by Huntress, whose researchers detected the attacks on September 14, 2024.
Huntress has already seen active breaches through these attacks at plumbing, HVAC, concrete, and other sub-industry companies.
Open ports and weak passwords
In these attacks, the attackers are taking advantage of a combination of exposed services amplified by users not changing default credentials on privileged accounts.
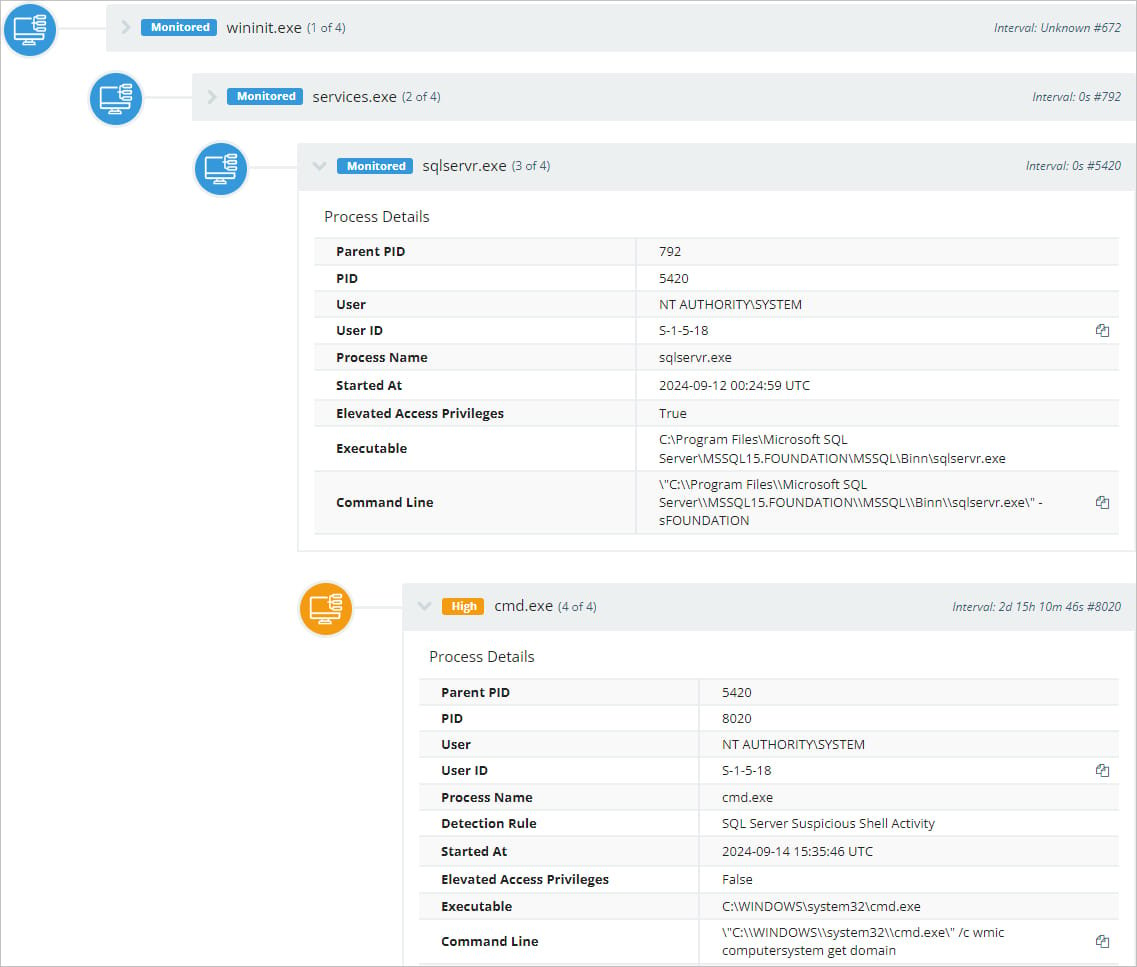
Huntress explains that the Foundation software includes a Microsoft SQL Server (MSSQL) that can be configured to be publicly accessible via TCP port 4243 to support a companion mobile app.
However, this also exposes the Microsoft SQL server to external attacks that try and brute force MSSQL accounts configured on the server.
By default, MSSQL has an admin account named ‘sa’ while Foundation has added a second one named ‘dba.’
Users who have not changed the default passwords on these accounts are susceptible to hijacks by external actors. Those who did but picked weak passwords may still be compromised via brute-forcing.
Huntress reports that it observed very aggressive brute-force attacks against these servers, sometimes reaching up to 35,000 attempts on a single host over an hour before they successfully guessed a password.
Once the attackers gain access, they enable the MSSQL ‘xp_cmdshell’ feature, which allows the threat actors to execute commands in the operating system through an SQL query.
For example, the EXEC xp_cmdshell 'ipconfig' query will cause the ipconfig command to be executed in a Windows command shell, and the output will be displayed in the response.
Source: Huntress
Two commands observed in the attacks are ‘ipconfig,’ to retrieve network configuration details, and ‘wmic,’ to extract information about the hardware, OS, and user accounts.
Huntress’s investigation from the three million endpoints under its protection unveiled 500 hosts running the targeted accounting software, 33 of which publicly exposed MSSQL databases with default admin credentials.
Huntress told BleepingComputer it had alerted Foundation of its findings, and the software vendor responded by saying the issue only affected the on-premise version of its application and not their cloud-based product.
Foundation also noted that not all servers have port 4243 open, and not all targeted accounts use the same default credentials.
Huntress recommends that Foundation admins rotate account credentials and ensure they’re not publicly exposing the MSSQL server if not needed.
Source link
lol
Hackers are brute-forcing passwords for highly privileged accounts on exposed Foundation accounting servers, widely used in the construction industry, to breach corporate networks. The malicious activity was first spotted by Huntress, whose researchers detected the attacks on September 14, 2024. Huntress has already seen active breaches through these attacks at plumbing, HVAC, concrete, and other…
Recent Posts
- Nutanix Grows New Customers As Channel Engagement Increases, CEO Says
- Tenable Selected by Tohoku University to Secure External-Facing Assets Amidst Migration to the Cloud
- New NachoVPN attack uses rogue VPN servers to install malicious updates
- Jen Caltrider Unwraps this Season’s Hidden Privacy Nightmare
- NordVPN Black Friday Deal: Save up to 74% on yearly subscriptions
