New Octo Android malware version impersonates NordVPN, Google Chrome
by nlqip

A new version of the Octo Android malware, named “Octo2,” has been seen spreading across Europe under the guise of NordVPN, Google Chrome, and an app called Europe Enterprise.
The new variant, analyzed by ThreatFabric, features better operational stability, more advanced anti-analysis and anti-detection mechanisms, and a domain generation algorithm (DGA) system for resilient command and control (C2) communications.
Ultimately, its appearance in the wild confirms that the project is alive and evolving despite the turbulence it went through recently.
Brief history and evolution
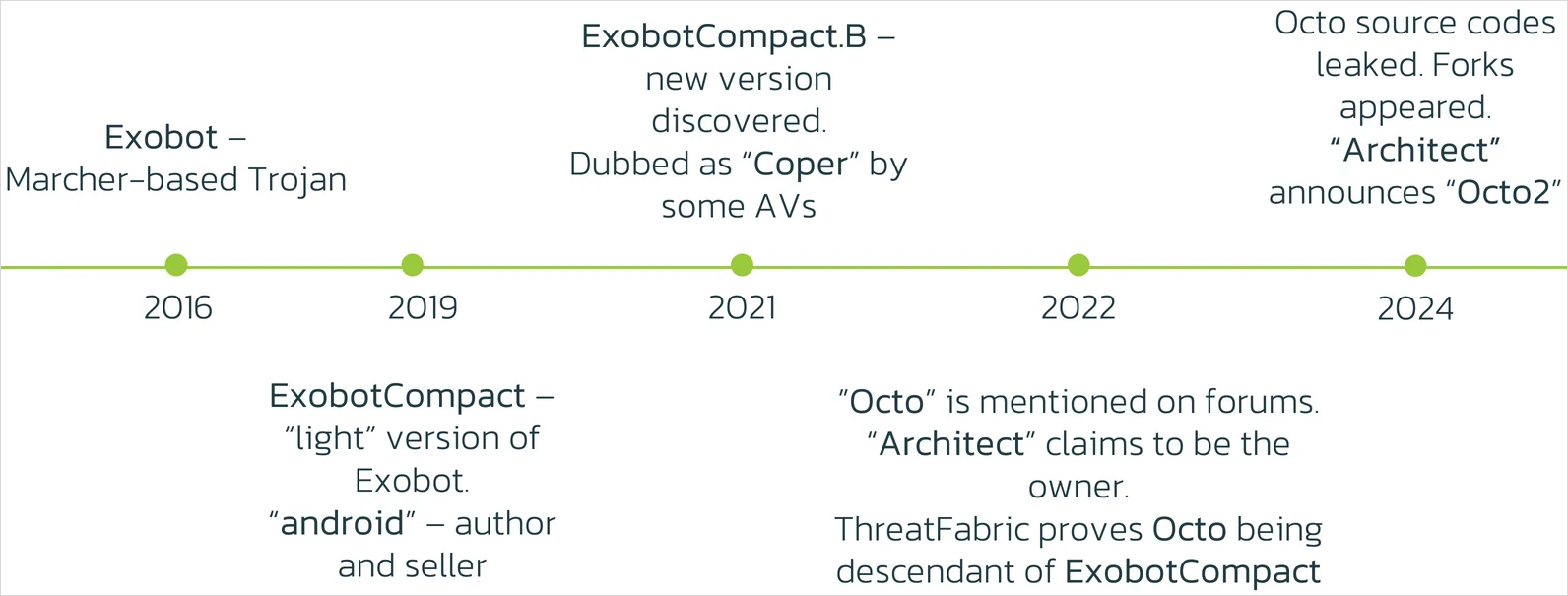
Octo is an Android banking trojan that evolved from ExoCompact (2019-2021), which itself was based on the ExoBot trojan that launched in 2016 and had its source code leaked online in the summer of 2018.
ThreatFabric discovered the first version of Octo in April 2022 on fake cleaner apps in Google Play. TF’s report at the time highlighted the malware’s on-device fraud capabilities that allowed its operators extensive access to the victim’s data.
Among other things, Octo v1 supported keylogging, on-device navigation, SMS and push notification interception, device screen locking, sound muting, arbitrary app launches, and using infected devices for SMS distribution.
ThreatFabric says the Octo was leaked this year, causing multiple forks of the malware to appear in the wild, presumably creating a dent in the sales for the original creator, ‘Architect.’
Following these events, Architect announced Octo2, likely as an attempt to throw an upgraded version into the malware market and spark cybercriminals’ interest. The malware’s creator even announced a special discount for customers of Octo v1.
Source: ThreatFabric
Octo2 operations in Europe
Campaigns currently deploying Octo2 focus on Italy, Poland, Moldova, and Hungary. However, as the Octo Malware-as-a-Service (MaaS) platform has previously facilitated attacks worldwide, including in the U.S., Canada, Australia, and the Middle East, we will likely see Octo2 campaigns appear in other regions soon.
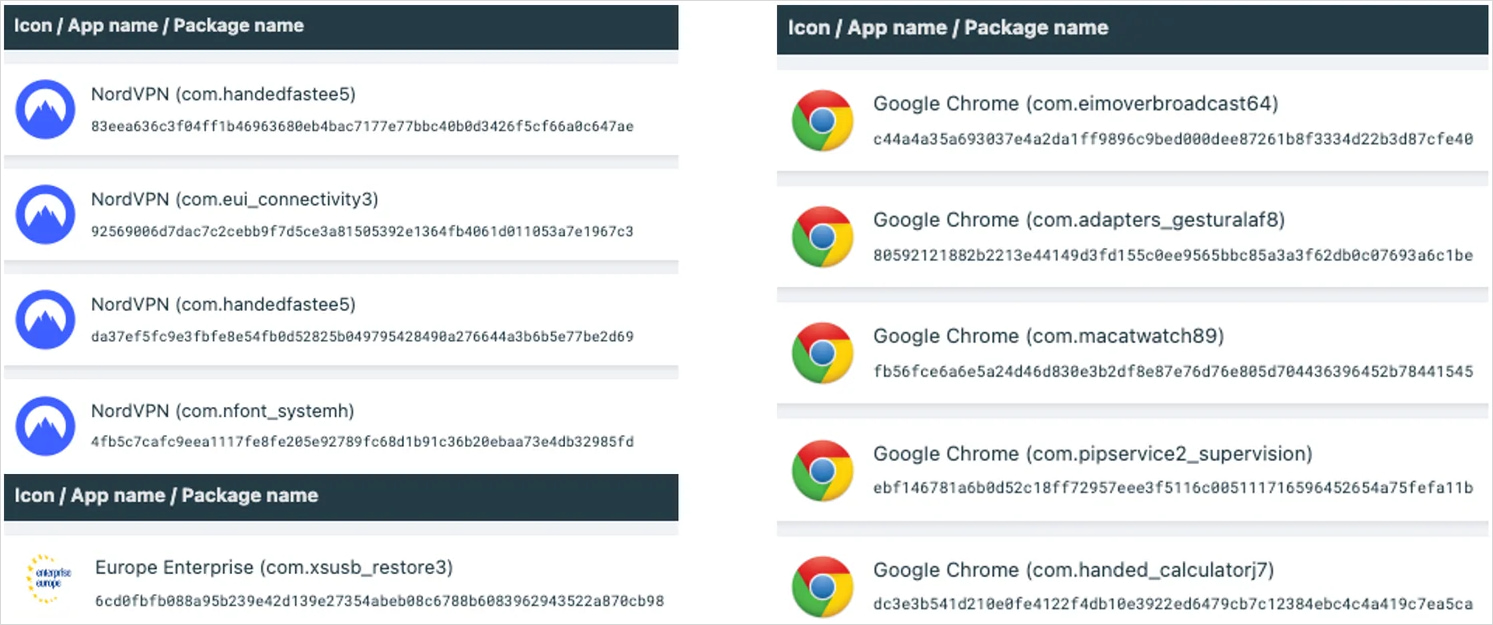
In European operations, the threat actors use fake NordVPN and Google Chrome apps, as well as a Europe Enterprise app, which is likely a lure used in targeted attacks.
Octo2 uses the Zombider service to add the malicious payload into these APKs while bypassing Android 13 (and later) security restrictions.
Source: ThreatFabric
More stable, more evasive, more capable
Octo2 is more of a rolling upgrade to the first version, improving the malware incrementally rather than implementing ground-breaking changes or rewriting code from scratch.
First, the malware author introduced a new low-quality setting on the remote access tool (RAT) module called “SHIT_QUALITY” that reduces data transmissions to a minimum, allowing more reliable connectivity when internet connection speeds are subpar.
Octo2 also decrypts its payload using native code and complicates analysis by dynamically loading additional libraries during execution, further improving its already strong evasion capabilities.
Finally, Octo2 introduces a DGA-based C2 domain system that allows the operators to quickly update and switch to new C2 servers, rendering blocklists ineffective and improving resilience against server takedown attempts.
ThreatFabric also notes that Octo2 now receives a list of apps to intercept and block push notifications from, allowing the operators to refine their targeting scope.
Octo2 has not been spotted on Google Play, so its distribution is currently believed to be limited to third-party app stores, which Android users should avoid.
Source link
lol
A new version of the Octo Android malware, named “Octo2,” has been seen spreading across Europe under the guise of NordVPN, Google Chrome, and an app called Europe Enterprise. The new variant, analyzed by ThreatFabric, features better operational stability, more advanced anti-analysis and anti-detection mechanisms, and a domain generation algorithm (DGA) system for resilient command and…
Recent Posts
- The 10 Hottest Semiconductor Startups Of 2024
- Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps
- Healthcare Ransomware Attacks: How to Prevent and Respond Effectively | BlackFog
- Black Friday Versus The Bots
- Over 2,000 Palo Alto firewalls hacked using recently patched bugs
