Why your password policy should include a custom dictionary
by nlqip

If your organization is like many, your employees may be relying on weak or easily guessable passwords — and inadvertently rolling out the red carpet for hackers and cybercriminals in the process. So how do you stop your staff from leaving the keys to your organization’s data and systems under the proverbial doormat? Integrating a custom dictionary into your password policy should be part of the solution.
In this post, we’ll explore custom dictionaries: what they are, why you can’t afford to ignore them, and how they fit into your cybersecurity strategy.
We’ll also provide examples of the kinds of words and terms your custom dictionary should include and discuss how a tool like Specops Password Policy can seamlessly integrate these dictionaries into your existing Active Directory password policy.
What are custom dictionaries?
Custom dictionaries are specialized lists of words, phrases, and character combinations that end users are prohibited from using when creating their passwords. A custom dictionary should be much more than a standard word list; it should include terms specific to your organization, as well as common words and phrases associated with your industry.
Essentially, incorporating a custom dictionary into your password policy gives your organization an additional layer of defense against targeted credential-based attacks.
Why are custom dictionaries needed?
Custom dictionaries are important for numerous reasons:
- End users create weak or easily-guessed passwords: Even with your best education efforts, humans are creatures of habit — meaning many users will opt for easy-to-remember (and therefore easy-to-guess) passwords. These include personal information (their spouse’s name), common words (admin, password), or simple variations of banned passwords (qwerty123!). Another tempting and memorable option is to choose words related to your specific business or industry.
- Risk of brute force/hybrid dictionary attacks: Cybercriminals frequently employ brute force and hybrid dictionary attacks to crack passwords — and if you don’t have a custom dictionary in place, these kinds of attacks can be extremely effective. For example, they may add your organization’s name and products to their attack dictionaries, in the hope that at least a handful of end users have used these terms in their passwords.
- Social engineering and targeted attacks: Cybercriminals can easily gather information about your organization and its employees through social media and other public sources. Then, they can use this info to create targeted word lists for their password-cracking attempts. Ensuring your custom dictionary includes company-specific terms and common employee information can help thwart these attacks.
- Industry-specific vulnerabilities: Every industry has its jargon and commonly used terms, and hackers use this knowledge to better target their password attacks. Don’t forget to beef up your custom dictionary with industry lingo — it’s a simple way to add an extra layer of security to your password policy.
How is your organization’s overall Active Directory password health? Find out now with a free, read-only check with Specops Password Auditor.
Custom dictionary examples
To better understand the concept of custom dictionaries, imagine that you handle IT for the Mid Cheshire NHS Foundation Trust – a regional healthcare foundation who reached out to Specops to help strengthen their password security. As you’re creating custom dictionaries for your organization, you’d want to include words and terms like:
Industry terms
As in other industries, healthcare professionals often default to industry jargon when creating passwords. To better protect your organization, you’d want to ensure your custom dictionary included terms that an attacker familiar with the healthcare sector might try first. Examples include:
- NHS (National Health Service)
- A&E (Accident and Emergency)
- Triage
- Outpatient
- Inpatient
Organization-specific terms
Terms unique to your organization would be among the first guesses for anyone targeting it specifically. To reduce the risk of these targeted attacks, ensure that your custom dictionary prevents their use in passwords. Examples include:
- Mid Chesire
- NE (acronym)
- Foundation trust
- Ward names (e.g., Nightingale, Florence)
- Department names (e.g., Radiology, Pathology)
- Hospital building names (e.g., Victoria Wing)
Common password patterns
In addition to industry and organization-specific terms, you want to prevent users from relying on common, easily guessable formats. Prohibiting users from following common password patterns will force them to create unique passwords. Examples include:
- NHS2024!
- Welcome123!
- ChangeMe1!
- NurseRN2024
- Dr[Lastname]2024
Specops Password Policy makes custom dictionaries easy
Integrating custom dictionaries into your password policies will help enhance your organization’s security, keeping your users, data, and systems safe. But what’s the best way to make that happen? For most organizations, a tool like Specops Password Policy is your best bet.
With Specops Password Policy, you can easily create and import tailored lists of prohibited passwords, seamlessly integrating them into your Active Directory environment.
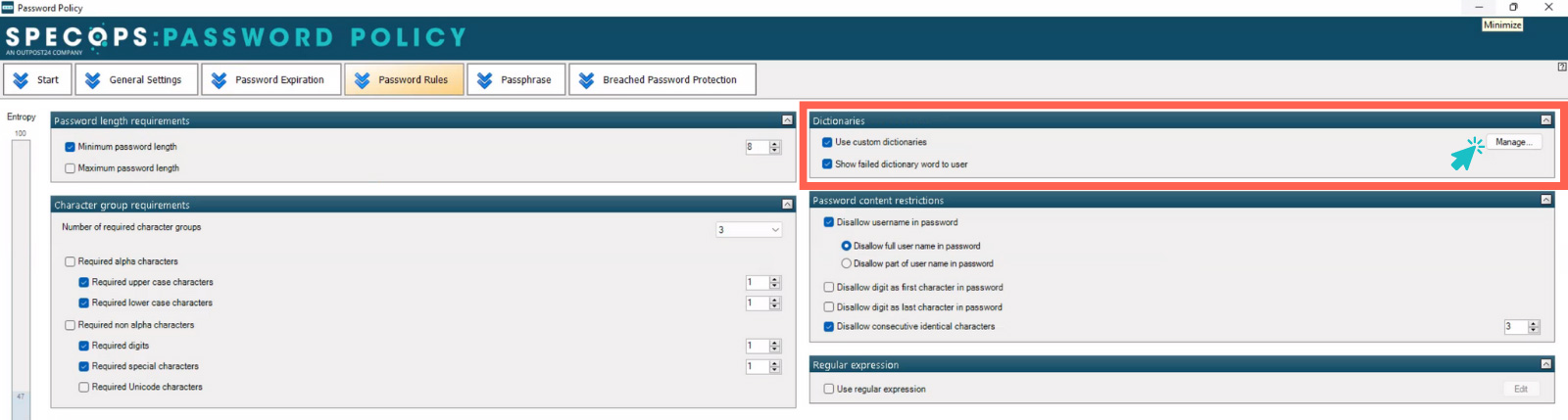
Combining your custom dictionaries with Specops’ breached password protection feature — which scans your Active Directory for over four billion known compromised passwords — allows you to mount a powerful defense against dictionary attacks and password reuse.
These tools will allow you to enhance your organization’s Active Directory password security, reduce risk of security breach, and ensure you are meeting compliance with industry standards.
Ready to make your organization more secure by adding a custom dictionary and banishing over four billion+ compromised passwords?
Try Specops Password Policy for free.
Sponsored and written by Specops Software.
Source link
lol
If your organization is like many, your employees may be relying on weak or easily guessable passwords — and inadvertently rolling out the red carpet for hackers and cybercriminals in the process. So how do you stop your staff from leaving the keys to your organization’s data and systems under the proverbial doormat? Integrating a…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
