New scanner finds Linux, UNIX servers exposed to CUPS RCE attacks
by nlqip

An automated scanner has been released to help security professionals scan environments for devices vulnerable to the Common Unix Printing System (CUPS) RCE flaw tracked as CVE-2024-47176.
The flaw, which enables attackers to perform arbitrary remote code execution if certain conditions are met, was disclosed late last month by the person who discovered it, Simone Margaritelli.
Although its RCE aspect appears limited in real-world deployments due to the prerequisites for exploitation, Akamai later showed that CVE-2024-47176 also opened the possibility for 600x amplification in distributed denial of service (DDoS) attacks.
The scanner was created by cybersecurity researcher Marcus Hitchins (aka “MalwareTech”), who created the scanner to help system administrators scan their networks and quickly identify devices running vulnerable CUPS-Browsed services.
“The vulnerability arises from the fact that cups-browsed binds its control port (UDP port 631) to INADDR_ANY, exposing it to the world. Since requests are not authenticated, anyone capable of reaching the control port can instruct cups-browsed to perform printer discovered.”
“In cases when the port is not reachable from the internet (due to firewalls or NAT), it may still be reachable via the local network, enabling privilege escalation and lateral movement.”
“For this reason, I’ve created this scanner designed to scan your local network for vulnerable cups-browsed instances.” – Marcus Hitchins
How the scanner works
The Python script (cups_scanner.py) sets up an HTTP server on the scanning machine that listens for incoming HTTP requests (callbacks) from devices on the network.
CVE-2024-47176 arises from CUPS-browsed (a daemon part of CUPS) binding its control port (UDP port 631) to INADDR_ANY, exposing the port to the network and allowing any system to send commands to it.
The scanner sends a custom UDP packet to the network’s broadcast address on port 631, sent to each IP address in the specified range, telling CUPS instances to send a request back.
If a device running a vulnerable cups-browsed instance receives the UDP packet, it will interpret the request and send an HTTP callback to the server, so only those that respond are marked as vulnerable.
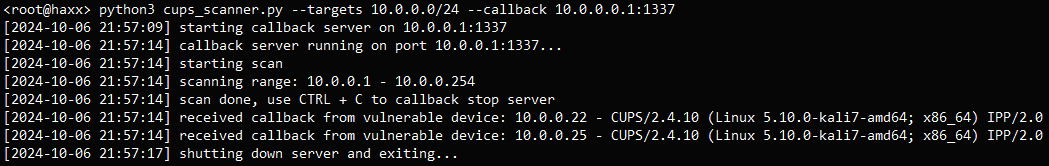
Source: GitHub
The results are written in two logs: one (cups.log) containing the IP addresses and CUPS version of the devices that responded and one (requests.log) containing the raw HTTP requests received by the callback server that can be used for deeper analysis.
By using this scanner, system administrators can plan and execute targeted patching or reconfiguration action, minimizing the exposure of CVE-2024-47176 online.
BleepingComputer has not tested the script and cannot warranty its effectiveness or safety, so you should use it at your own risk.
Source link
lol
An automated scanner has been released to help security professionals scan environments for devices vulnerable to the Common Unix Printing System (CUPS) RCE flaw tracked as CVE-2024-47176. The flaw, which enables attackers to perform arbitrary remote code execution if certain conditions are met, was disclosed late last month by the person who discovered it, Simone…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
