Quishing attacks are targeting electric car owners: Here’s how to slam on the brakes
by nlqip

Scams
Ever alert to fresh money-making opportunities, fraudsters are blending physical and digital threats to steal drivers’ payment details
15 Oct 2024
•
,
5 min. read

Many countries and regions across the world have been moving quickly on electric cars in recent years. Around 14 million new cars were registered in 2023 alone, a 35% annual increase which brings the worldwide total to over 40 million. But with new technology comes new threats. Ever alert to fresh money-making opportunities, criminal groups are blending physical and virtual-world threats to steal drivers’ payment details.
One of their latest tricks, spotted in several countries in Europe, is to use QR code phishing techniques known as “quishing” to eavesdrop on or steal payment details. In fact, it’s not at all dissimilar from tricks that leverage fake QR codes on parking meters, and EV drivers need to watch out for this kind of threat at charging stations.
What’s quishing and how does it work?
Phishing is one of the most popular and effective techniques for cybercriminals to achieve their goals. It’s often a precursor to all kinds of cyberthreats, revolving around theft of your personal information and log-ins, or covert installation of malware. Why does it work so well? Because it relies on our propensity to believe what we are told by people or organizations in positions of authority.
There are so many variations of phishing that it can be difficult for police, corporate security teams and government agencies to keep their public awareness exercises up to date. Quishing is a good example. Although QR codes have been around since the 90s, quishing as a threat really started to appear during the pandemic. That’s because QR codes became a familiar sight up and down the high street, as a more hygienic way to access everything from menus to medical forms.
Fraudsters leapt into action, sticking fake QR codes over the real ones. When scanned, they take victims to a phishing site to harvest their credentials/information or download malware. It’s a particularly effective tactic because it doesn’t arouse the same level of suspicion among users as, say, phishing URLs. Mobile devices are also typically less well protected than laptops and desktops, so there’s more chance of success. A report from late last year noted a 51% increase in quishing incidents in September versus January-August 2023.
Why are EVs at risk?
Ever-resourceful criminal actors have now spotted a way to adapt the scam to the new EV craze sweeping Europe. According to reports from the UK, France and Germany, fraudsters are sticking malicious QR codes on top of legitimate ones on public charging stations. The code is meant to take users to a website where they can pay the station operator (e.g., Ubitricity) for their electricity.
However, if they scan the bogus code, they’ll be taken to a lookalike phishing site that prompts them to enter their payment details, which are then harvested by the malicious actors. It’s claimed that the correct site will load at the second attempt, to ensure victims can eventually pay for their charging. It’s also claimed in some reports that bad actors may even be using signal jamming technology, to prevent victims from using their charging apps and forcing them to scan the malicious QR code.
With over 600,000 EV charging points across Europe, there’s plenty of opportunities for scammers to catch drivers unawares with such scams. They take advantage of the fact that many EV owners may be new to the experience, and more inclined to scan the code rather than trying to download the official charging/payment app or call the helpline. With various vendors supplying these stations, the scammers may also be looking to capitalize on user fatigue. A QR code is often a quicker and more attractive option than taking the time to download multiple charging apps.
There have been a number of reports about scammers targeting motorists via malicious QR codes stuck to parking meters. In this case, the unwitting motorist may not only lose their card details – they might also be hit by a parking fine from the local council.
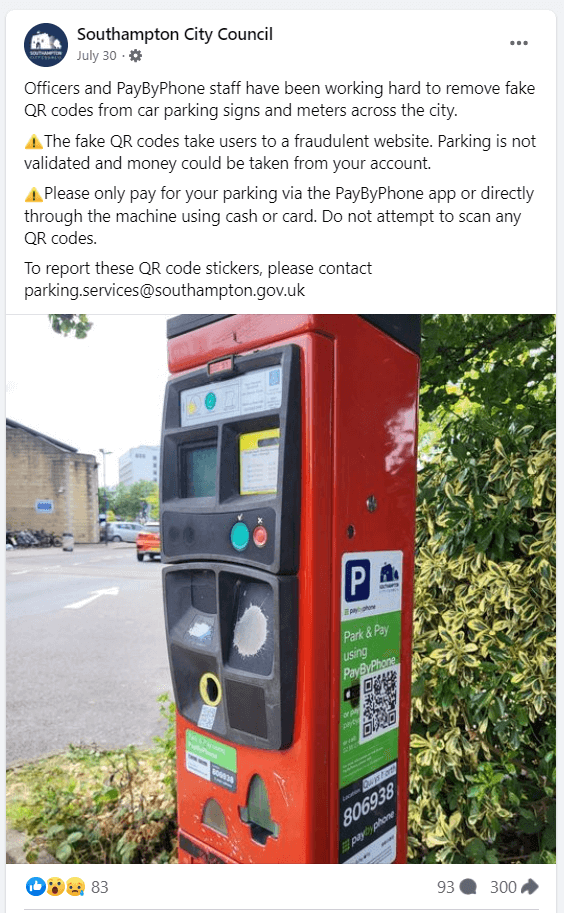
 How to stay safe from QR phishing
How to stay safe from QR phishing
Although the current scams seem to be confined to harvesting payment details via phishing pages, there’s no reason why bad actors couldn’t tweak the threat to install malware that hijacks the victim’s device and/or steals other logins and sensitive information from it. Fortunately, there are some simple steps you can take to mitigate the risk of quishing while you’re out and about:
- Look closely at the QR code. Does it appear as if stuck over the top of something else, or is it part of the original sign? Is it a different color or font to the rest of the sign, or does it look out of place in any other way? These could be red flags.
- Never scan a QR code unless it’s displayed on the charging/parking meter terminal itself.
- Consider only paying via a phone call or the official charging app of the relevant operator.
- Consider disabling the option to perform automatic actions when scanning a QR code, such as visiting a website or downloading a file. After scanning, look at the URL to check that it’s a legitimate domain associated with the service, rather than a suspicious URL.
- Does the website the QR code takes you to feature any grammatical or spelling mistakes or there’s something else that feels off about it? If so, it may be a phishing site.
- If something doesn’t look right, call the charging operator direct.
- Many parking meters, for example, offer multiple ways to pay, such as credit card, NFC payments or coins. If you’re uncomfortable scanning a QR code, consider using one of these alternatives to avoid the risk of interacting with a fraudulent code.
- If you think you may have been scammed, freeze your payment card and report potential fraud to your bank/card provider.
- Check your bank statement for any suspicious transactions, if you are concerned you may have been a victim of quishing.
- Use two-factor authentication (2FA) on all accounts that offer for an extra layer of security. This helps protect your account even if a scammer manages to redirect you to a fraudulent website and steal your credentials.
- Ensure your mobile device has security software installed from a reputable provider.
News of the latest QR quishing campaign will only increase calls for codes to be banned from public places. But in the meantime, it pays to be cautious.
Source link
lol
Scams Ever alert to fresh money-making opportunities, fraudsters are blending physical and digital threats to steal drivers’ payment details 15 Oct 2024 • , 5 min. read Many countries and regions across the world have been moving quickly on electric cars in recent years. Around 14 million new cars were registered in 2023 alone, a…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
