The Phantom Menace of Social Engineering
by nlqip
Clickjacking (Clickfix), also known as a “UI redress attack,” is a malicious technique where an attacker tricks a user into clicking on something different from what they perceive they are clicking on. This is often achieved by layering invisible or disguised elements over legitimate website content. For example, an attacker might place an invisible button over a legitimate “Submit” button. When the user clicks what they believe is the “Submit” button, they are actually clicking on the hidden button, which could lead to unintended actions like:
Financial gain for the attacker: Clickjacking can be used in conjunction with advertising networks, where each click generates revenue for the attacker.
Redirects to malicious websites: The hidden element could redirect the user to a malicious website designed to steal credentials or deliver malware.
Unwanted interactions with web elements: The click could trigger actions like liking a page, sharing content, or making purchases without the user’s knowledge or consent.
This cunning social engineering tactic, first observed in May 2024, uses deceptive “ClearFake” pop-up windows to trick users into executing malicious PowerShell code. As detailed in a recent blog post by Sekoia.io, ClickFix is rapidly gaining traction amongst cybercriminals due to its effectiveness in bypassing traditional security measures and exploiting human vulnerability.
The Sekoia Threat Detection & Research (TDR) team, who have been tracking this tactic closely, published a private report (FLINT 2024-027) outlining how ClickFix abuses PowerShell and the clipboard to compromise systems. Essentially, victims are presented with fake error messages in their web browsers, prompting them to copy and paste seemingly innocuous code which, in reality, unleashes malware onto their machines.
Proofpoint researchers, who coined the term “ClickFix,” first reported this tactic being used by the initial access broker TA571 in email phishing campaigns as early as March 2024. These campaigns often employed HTML files masquerading as Word documents to deliver payloads like Matanbuchus, DarkGate, and NetSupport RAT.
What makes ClickFix particularly insidious is its ability to seamlessly integrate with drive-by download attacks. Sekoia.io analysts have observed a surge in campaigns leveraging ClickFix to spread infostealers, botnets, and remote access tools (RATs) on both Windows and macOS systems. By circumventing browser security features and antivirus software, ClickFix significantly increases the attacker’s success rate.
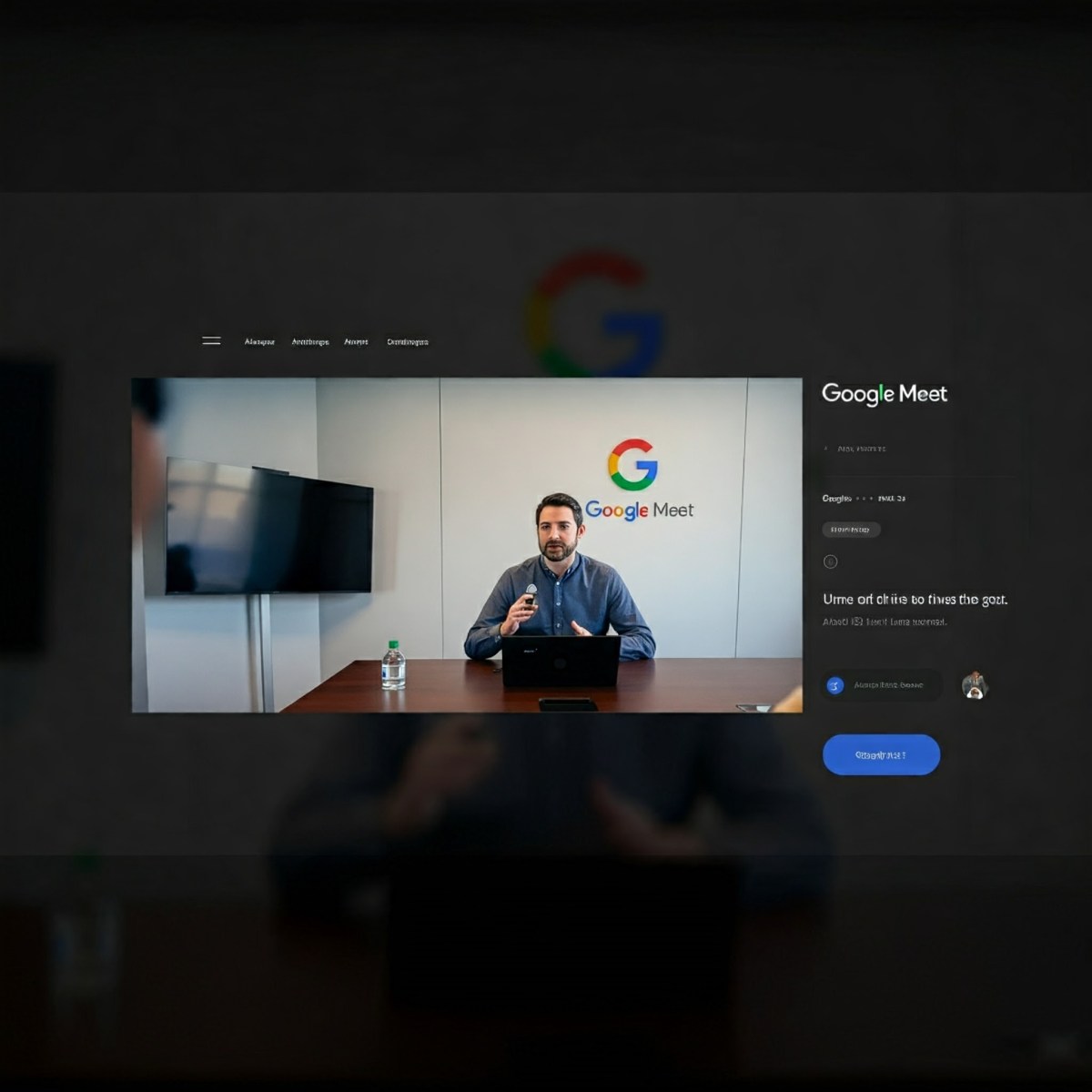
One notable ClickFix cluster, analyzed in depth by Sekoia.io, uses fake Google Meet video conference pages as a lure. This campaign, attributed to the cybercrime groups “Slavic Nation Empire (SNE)” and “Scamquerteo” (sub-teams of “Marko Polo” and “CryptoLove” respectively), highlights the increasing sophistication and organization behind these attacks.
Related
Source link
lol
Clickjacking (Clickfix), also known as a “UI redress attack,” is a malicious technique where an attacker tricks a user into clicking on something different from what they perceive they are clicking on. This is often achieved by layering invisible or disguised elements over legitimate website content. For example, an attacker might place an invisible button…
Recent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’
